.png)
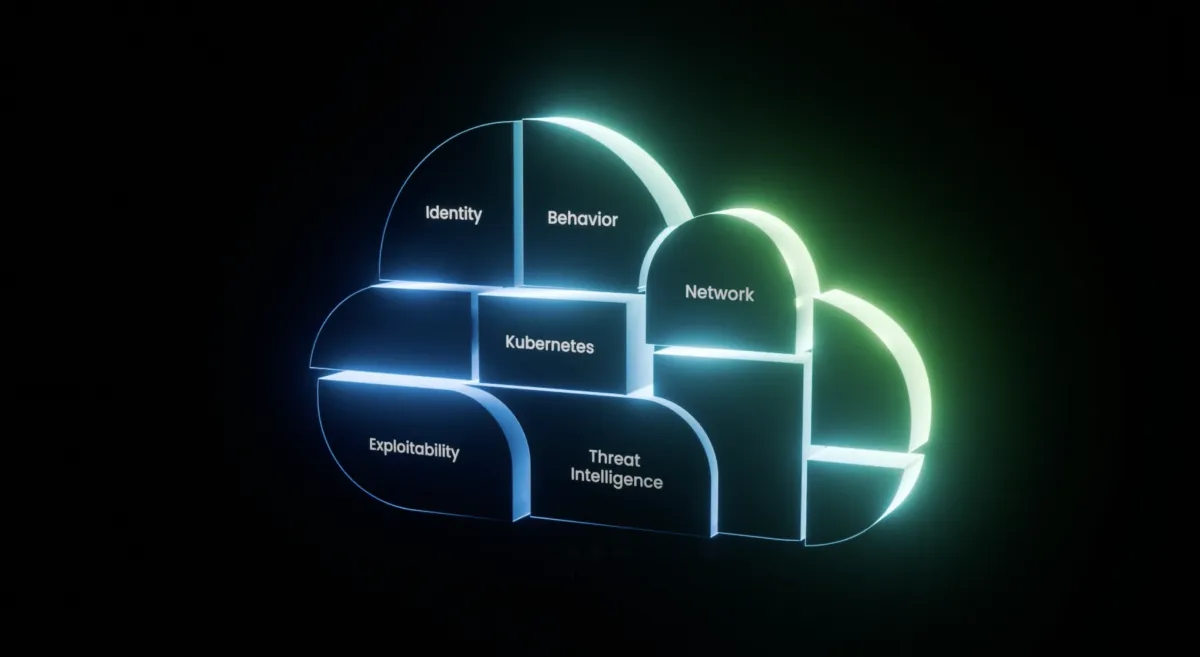
Seeing logs and alerts isn’t seeing the cloud. Today’s attackers hide in the gaps between tools. This blog shows why visibility into cloud context is the key to exposing their paths and stopping incidents before they become breaches.
When security teams say they “see the cloud,” what they often mean is they see pieces of it: logs, workloads, alerts, and maybe some configuration snapshots. But that isn’t cloud context.
When organizations migrated to the cloud, developers led the transformation. They rehosted, replatformed, and rebuilt infrastructure around scalable APIs, ephemeral services, and complex identity structures. In contrast, security teams lifted and shifted legacy tooling into this new environment. SIEMs were extended to ingest cloud logs. EDRs were deployed on virtual machines. SOAR playbooks were tweaked to trigger cloud-specific actions. On the surface, these changes suggested readiness.
But what they didn’t bring along was visibility into context.
Traditional tools remained focused on hosts, endpoints, and raw log ingestion. As infrastructure became dynamic and identity-driven, these tools lacked the capability to understand how one event influenced another. A suspicious login, policy modification, or data access might all be logged, but without the cloud context to correlate them, they remain just noise.
The result? Security teams are left working with fragments: alerts that lack meaning, logs that lack relevance, and incidents that unfold invisibly between the lines.
Cloud context refers to connections within the layered structure of the cloud itself, including identities, configurations, network paths, workloads, and Kubernetes clusters.
Security teams need visibility into how these layers connect. When tracked continuously, changes in cloud context – both malicious and not – make up the full path of cloud activity. In the case of a breach, understanding how attackers cross, manipulate, and exploit the cloud itself provides context for attack paths and blast radius measurements.
Traditional security tools don’t have visibility into the cloud and therefore miss the layers that connect and contextualize the alerts they send to security teams.
Modern attackers aren’t only dropping malware payloads. They escalate privileges, pivot across accounts, modify routes, and assume roles. These are called cloud-conscious attackers, and their behavior is almost invisible to tools that only monitor logs or endpoints.
Threats now live in the space between workloads: in trust policies, IAM roles, VPC routes, and misconfigured security groups. The cloud context layer is the blind spot that can enable the most severe breach.
Imagine an adversary who:
Each step might look benign on its own. But together, it forms an attack storyline. And only with cloud context monitored in real time can you see the full picture.
Let’s say an attacker compromises a developer’s credentials and assumes a role.
In a typical setup:
Without complete visibility into cloud context, this event looks benign.
Stream.Security’s CloudTwin™, a continuously updated replica of your entire cloud that is the basis of Stream’s detection and response engine, provides teams with that visibility in order to see full attack paths across cloud layers. By correlating actions using timing, access paths, and behavior to show how one change leads to the next in an attack, Stream reveals how activity and architecture interact. Analysts using Stream can instantly see enriched attack paths to determine root cause, attack blast radius, and response options.
Stream’s CDR platform reveals a unified breach narrative that integrates data from security tools as well as cloud data:
What looks like five disconnected alerts to legacy tools is actually a single, coherent attack path. The CloudTwin™ displays this progression, showing both attacker intent and breach blast radius all in real time.
When you integrate cloud context into your security workflow, you fundamentally change how your team works. Instead of spending hours correlating isolated alerts, analysts act on complete narratives.
Cloud context reveals the hidden relationships between identity, configuration, and infrastructure that determine whether an event is benign or a breach in progress. Full visibility across cloud layers removes false positives not by filtering alerts, but by showing which ones lead to meaningful change - and which don’t. By enriching alerts with cloud context, security teams can understand what changed in the cloud, who changed it, what it exposed, and why it matters.
Cloud context is not a “nice to have.” It is the missing visibility layer that traditional tools weren’t built to understand. It enriches what your SIEM logs. It gives your EDR broader perspective. It tells your response tools what the right action is, not just what might be possible.
Stream.Security brings complete cloud context in real-time to every stage of incident response, empowering SOC, SecOps, and IR teams to:
Ready to see what cloud context can do for your team?
Meet with our CDR experts to see how cloud context transforms security from reactive triage into confident, real-time response.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.


.png)
