AI based alert triage grounded in real cloud state.
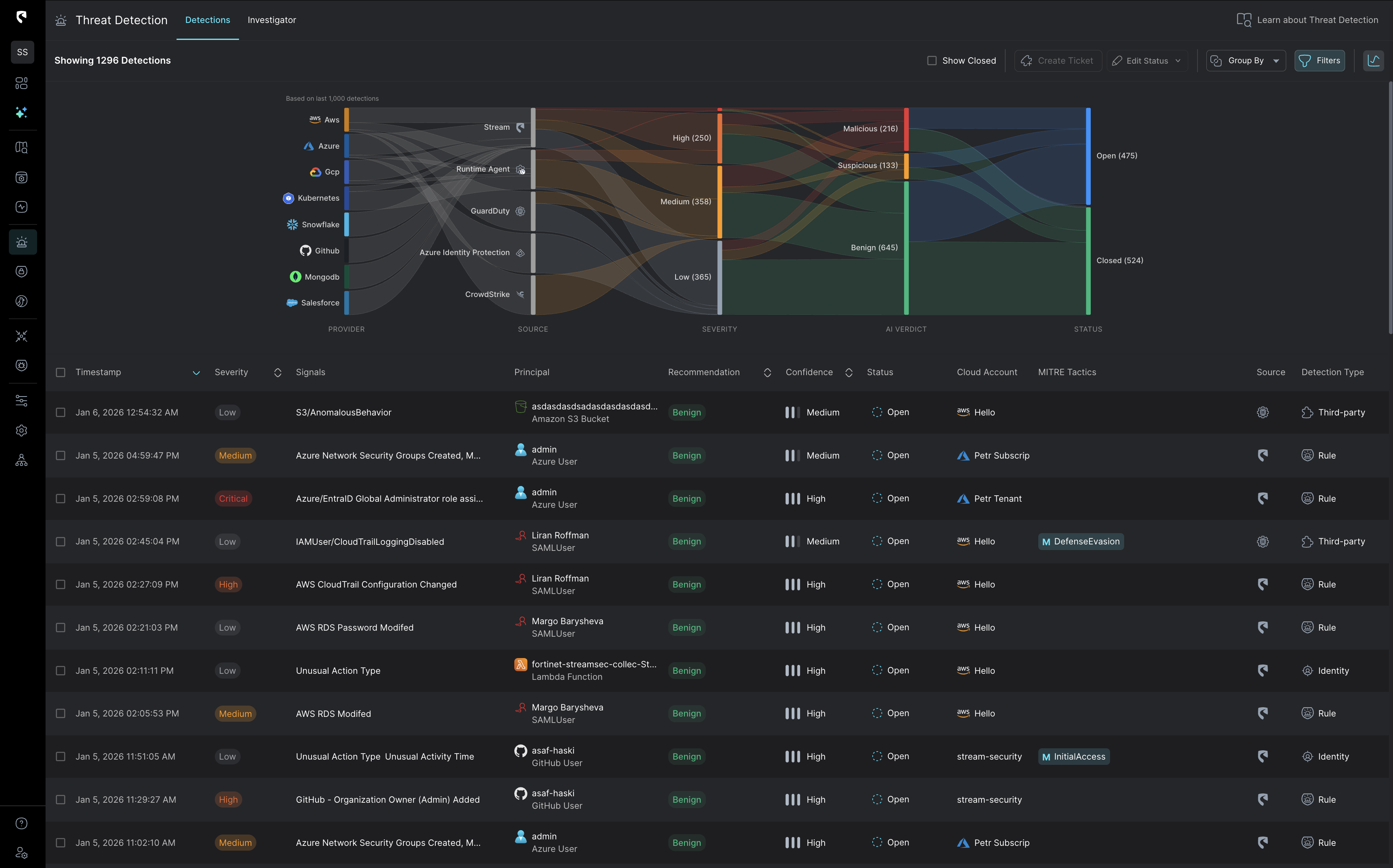
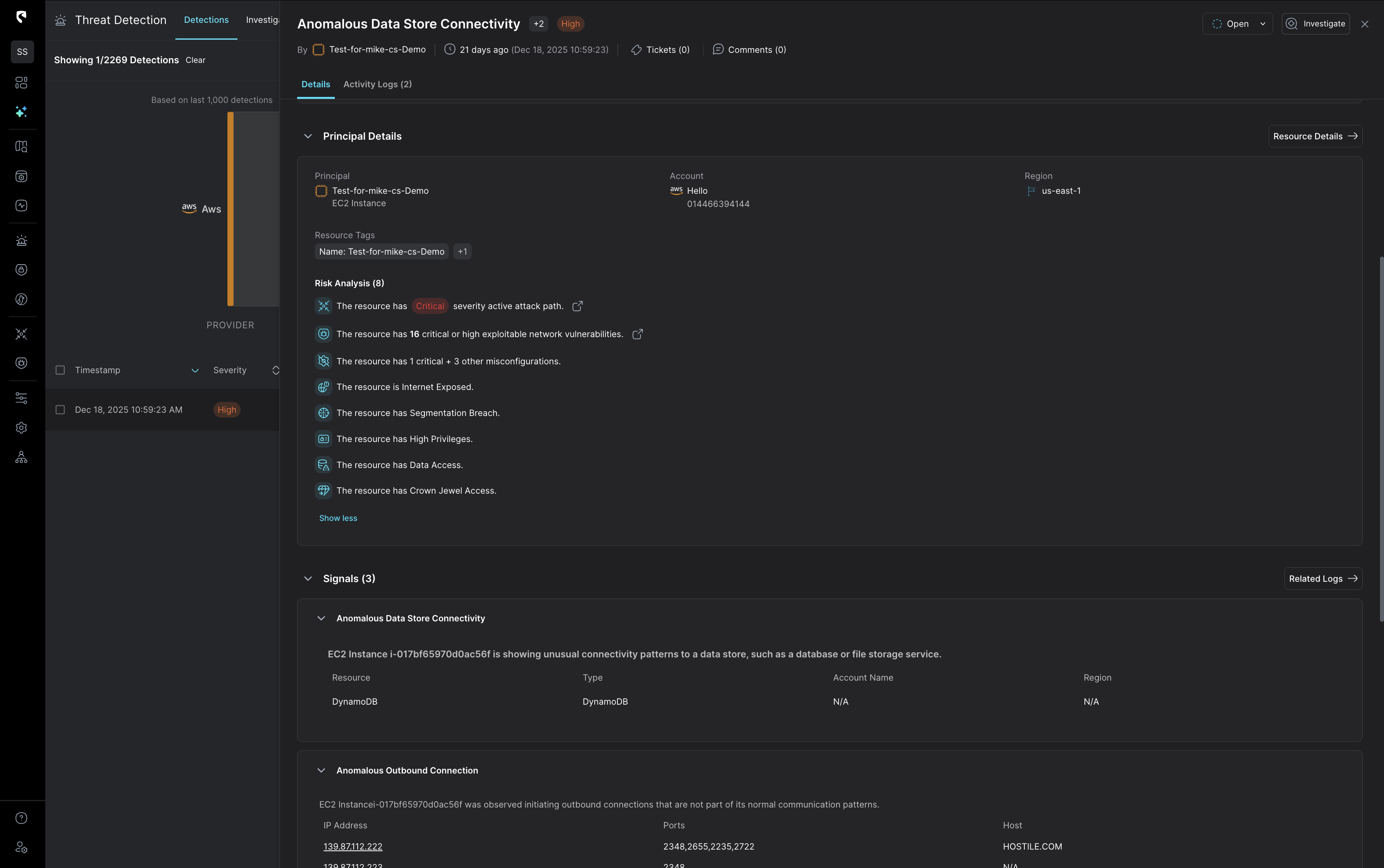
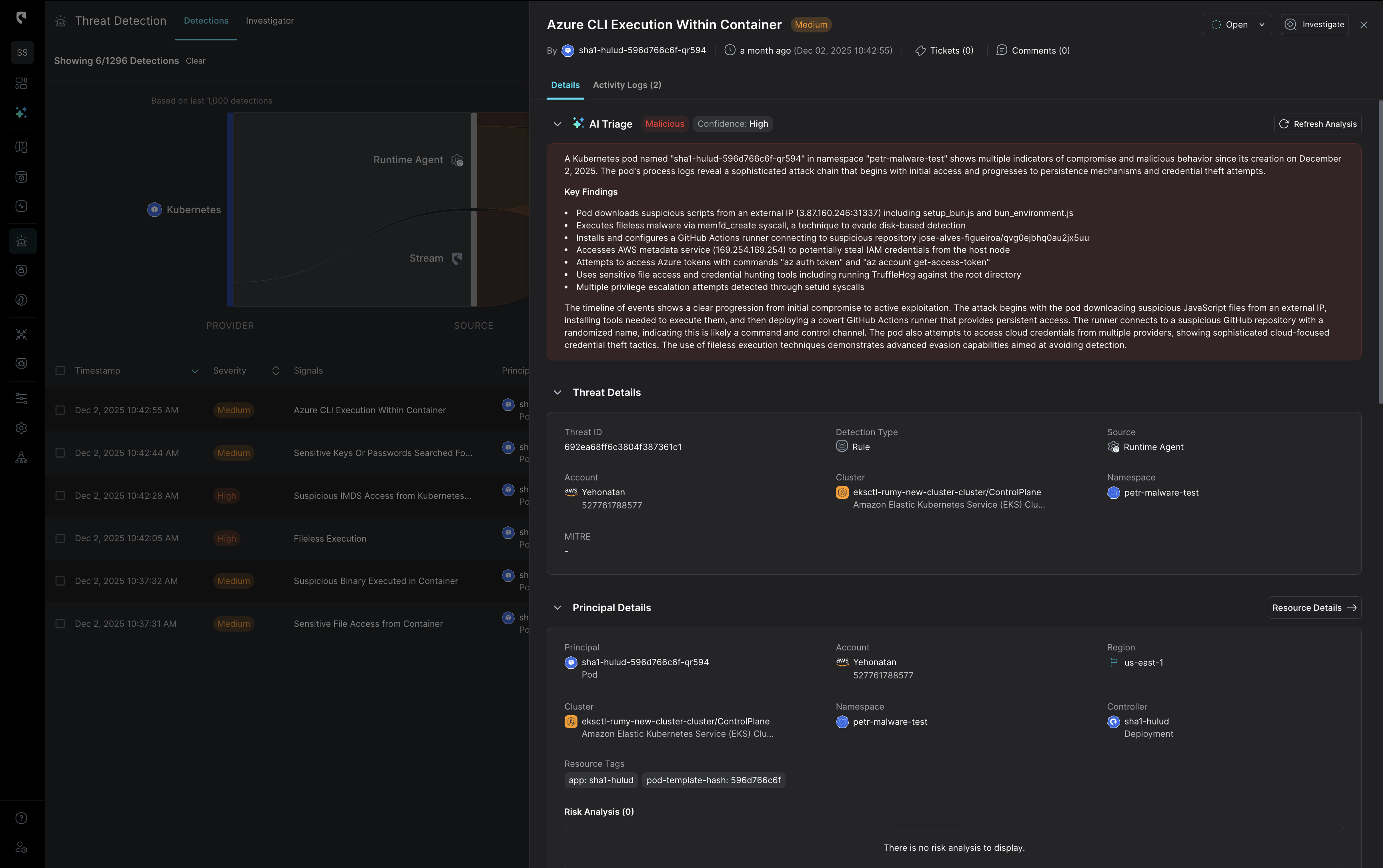
Stream’s AI triage prioritizes alertsusing real time exploitability, blast radius, and behavioral context from the CloudTwin.
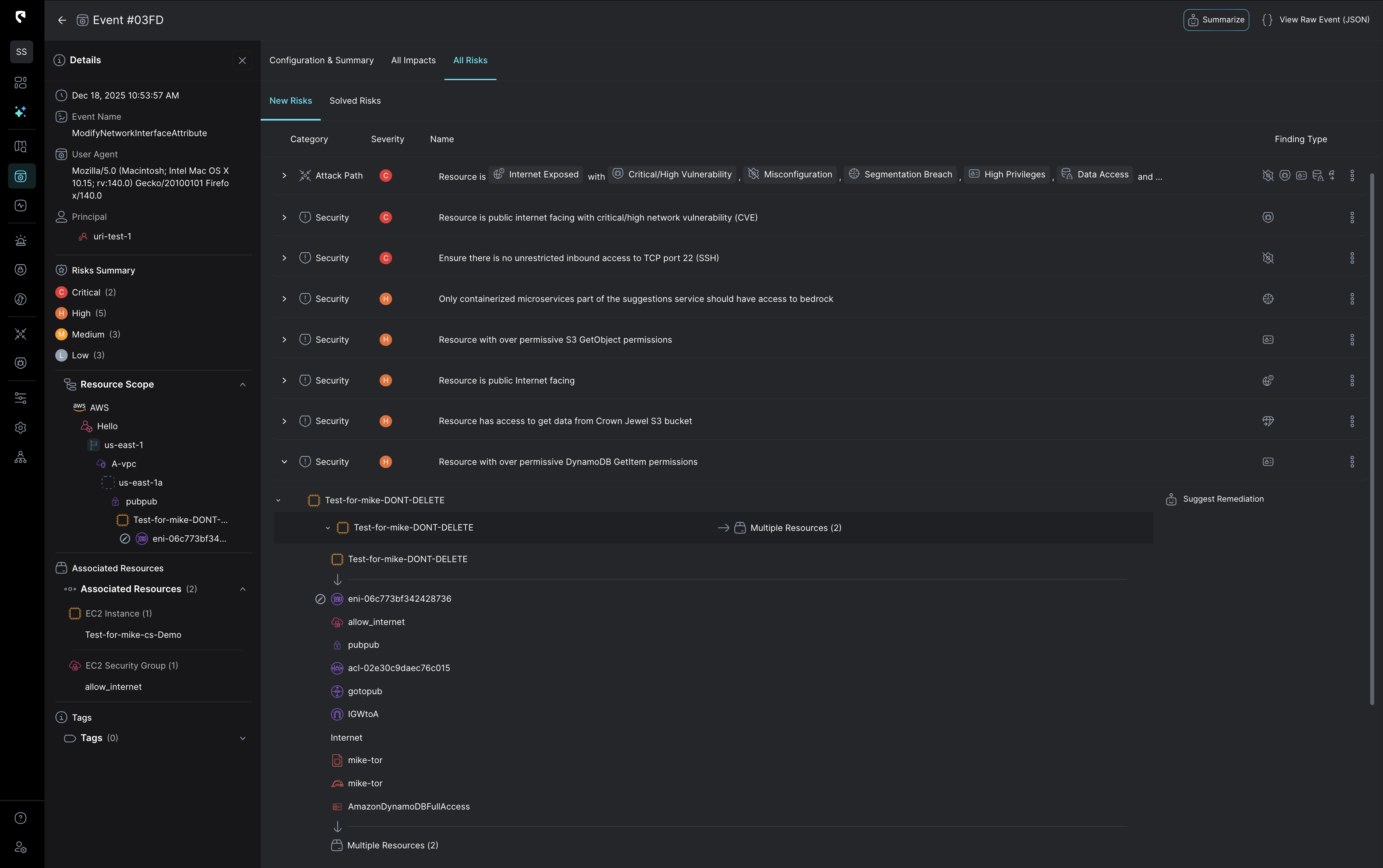
Every signal is interpreted in the context of your identities, resources, and network paths, delivering accurate, high-fidelity detections
across your entire cloud without the noise.