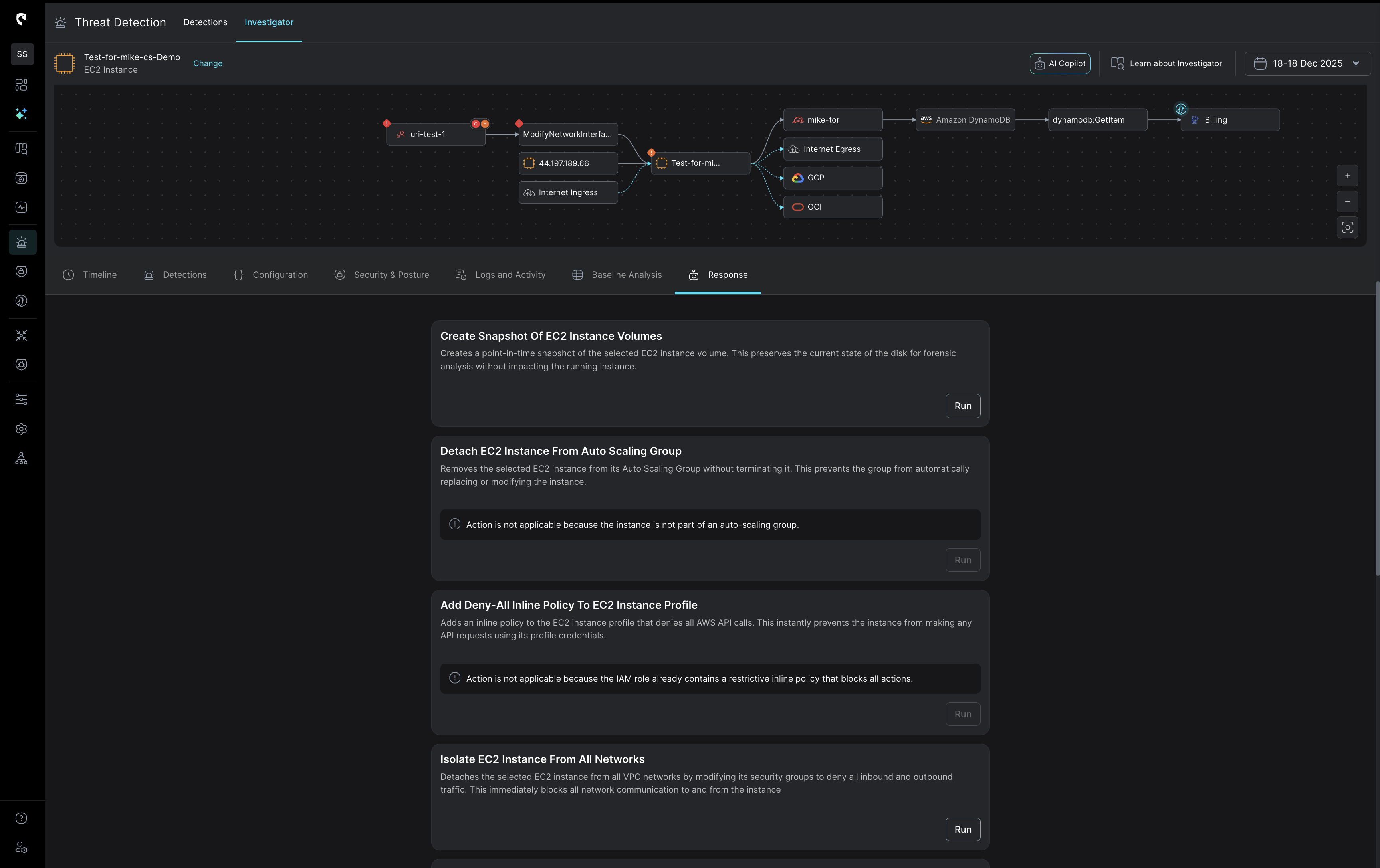
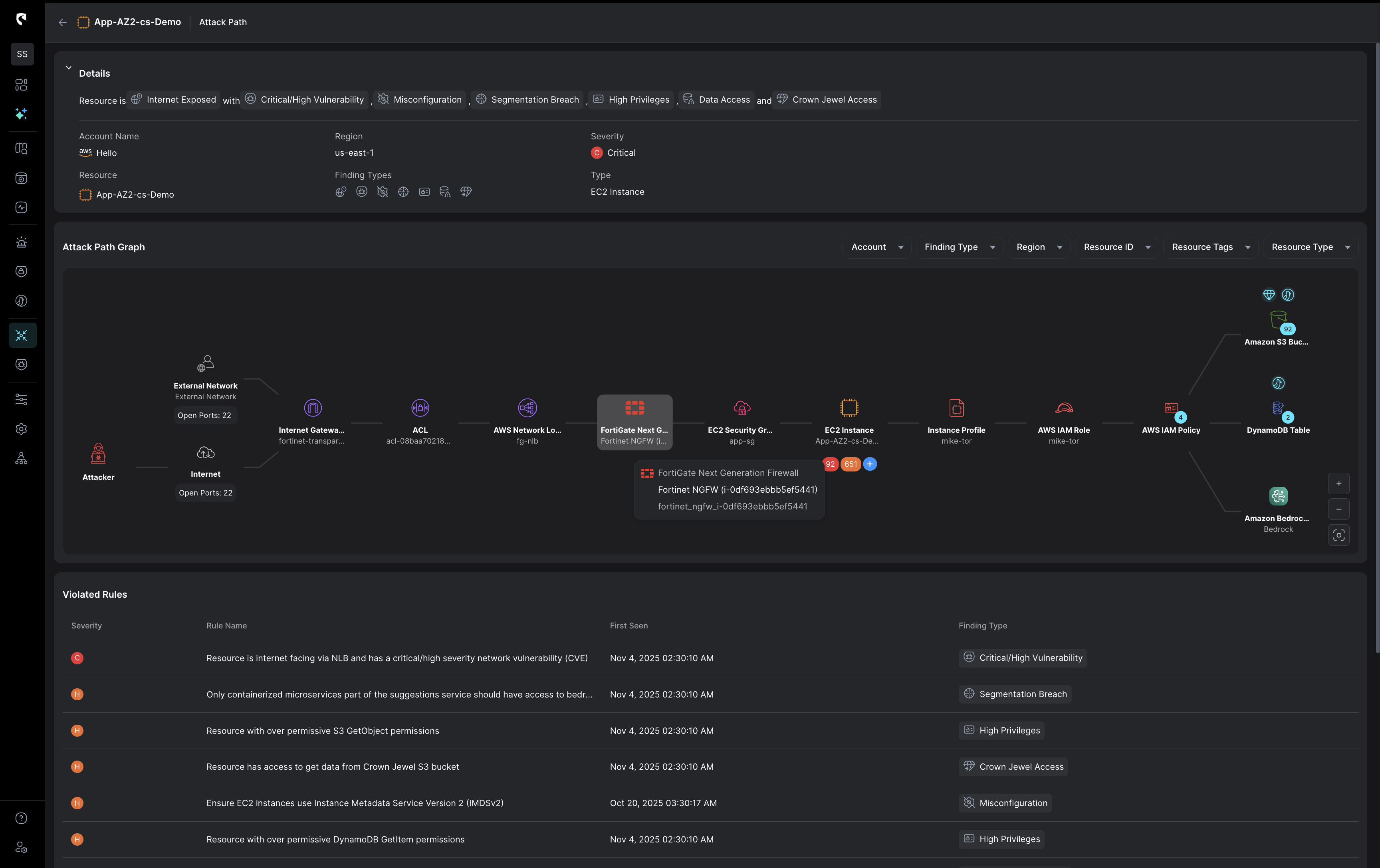
Response strategy powered by real-time cloud context
Stream’s CloudTwin™ brings together data from cloud behavior, configuration, identity, network, perimeter, and runtime sources for full cloud visibility. With this layered context, your team can map full attack blast radius and entry paths to select the best control point for response.