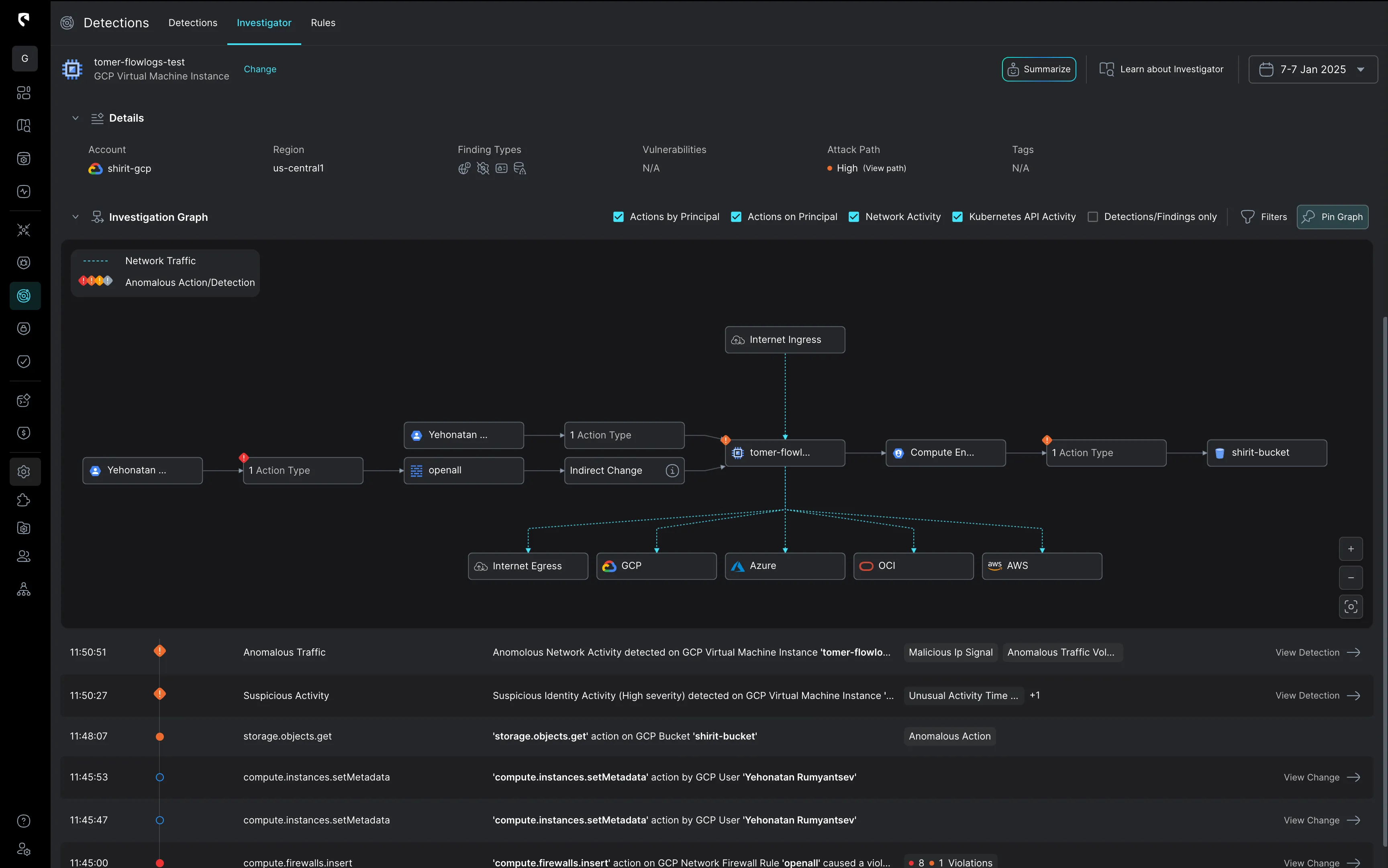
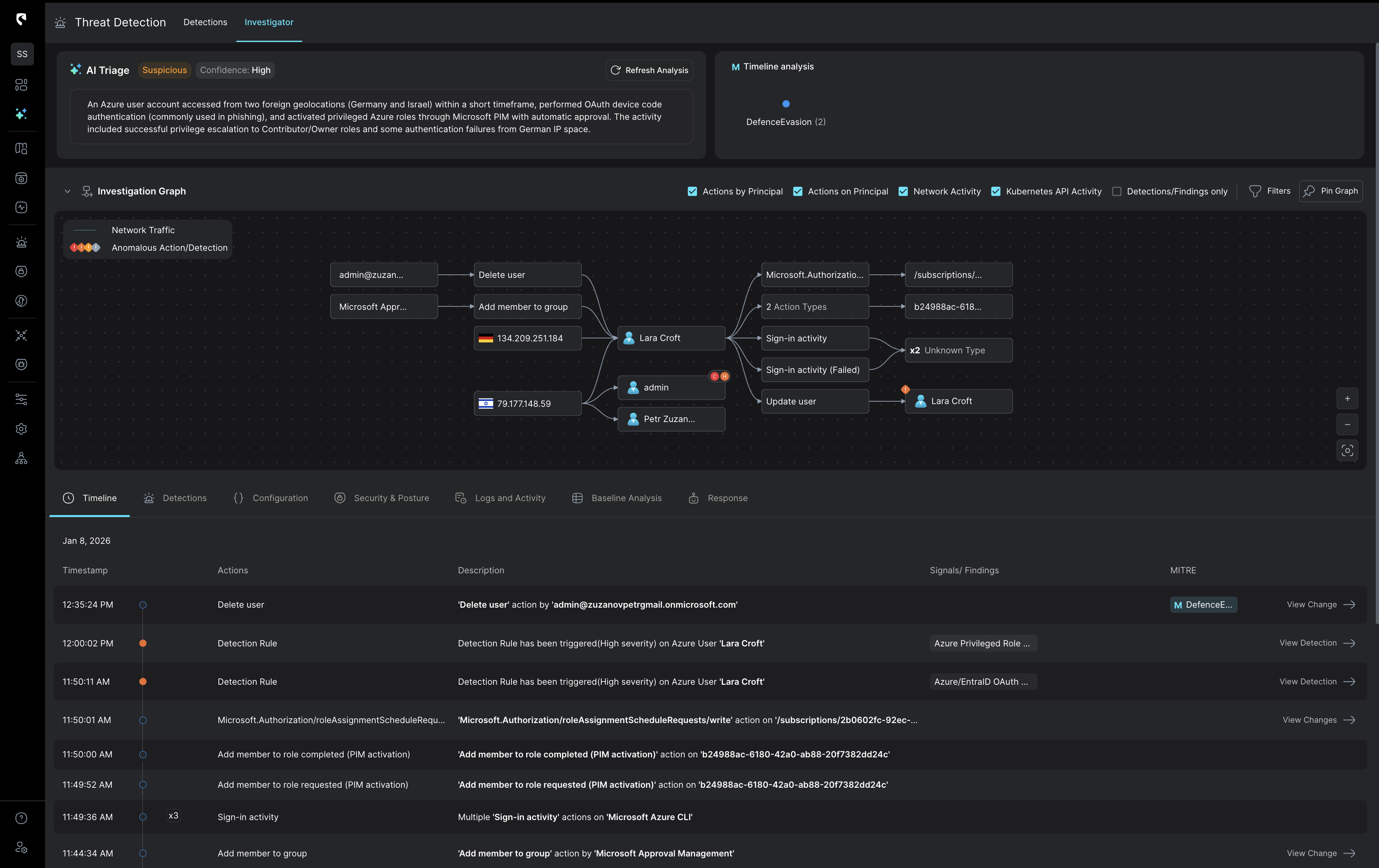
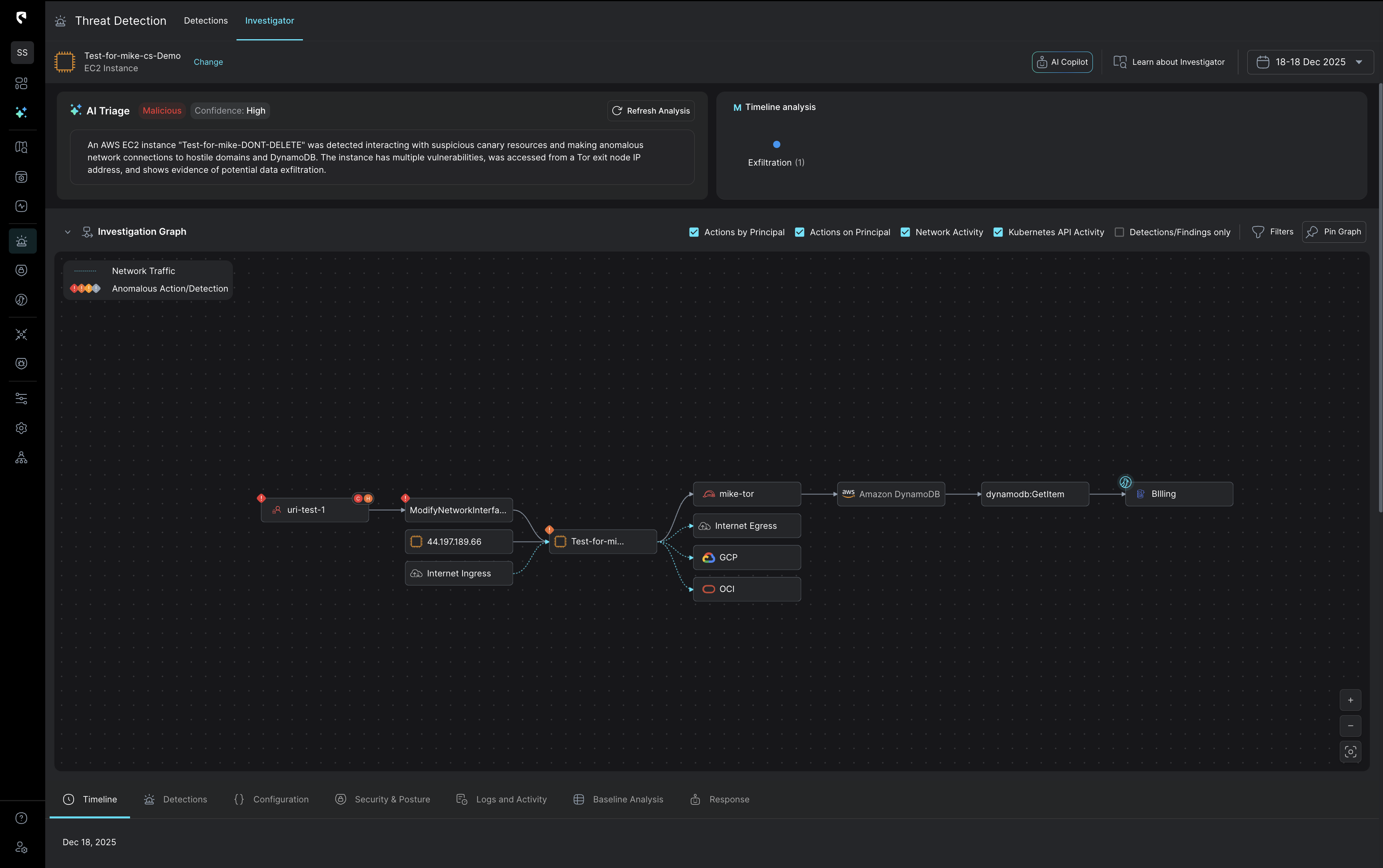
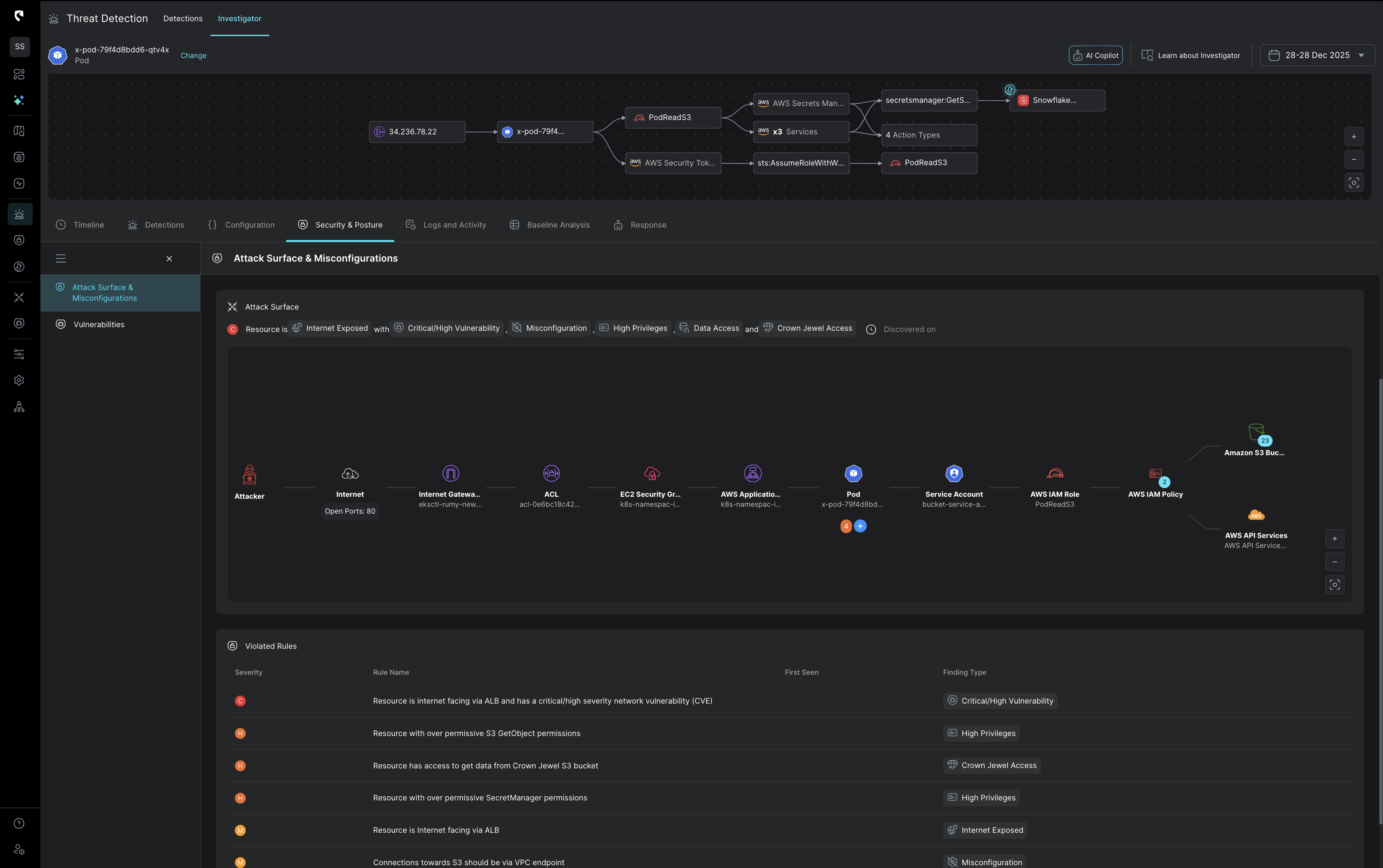
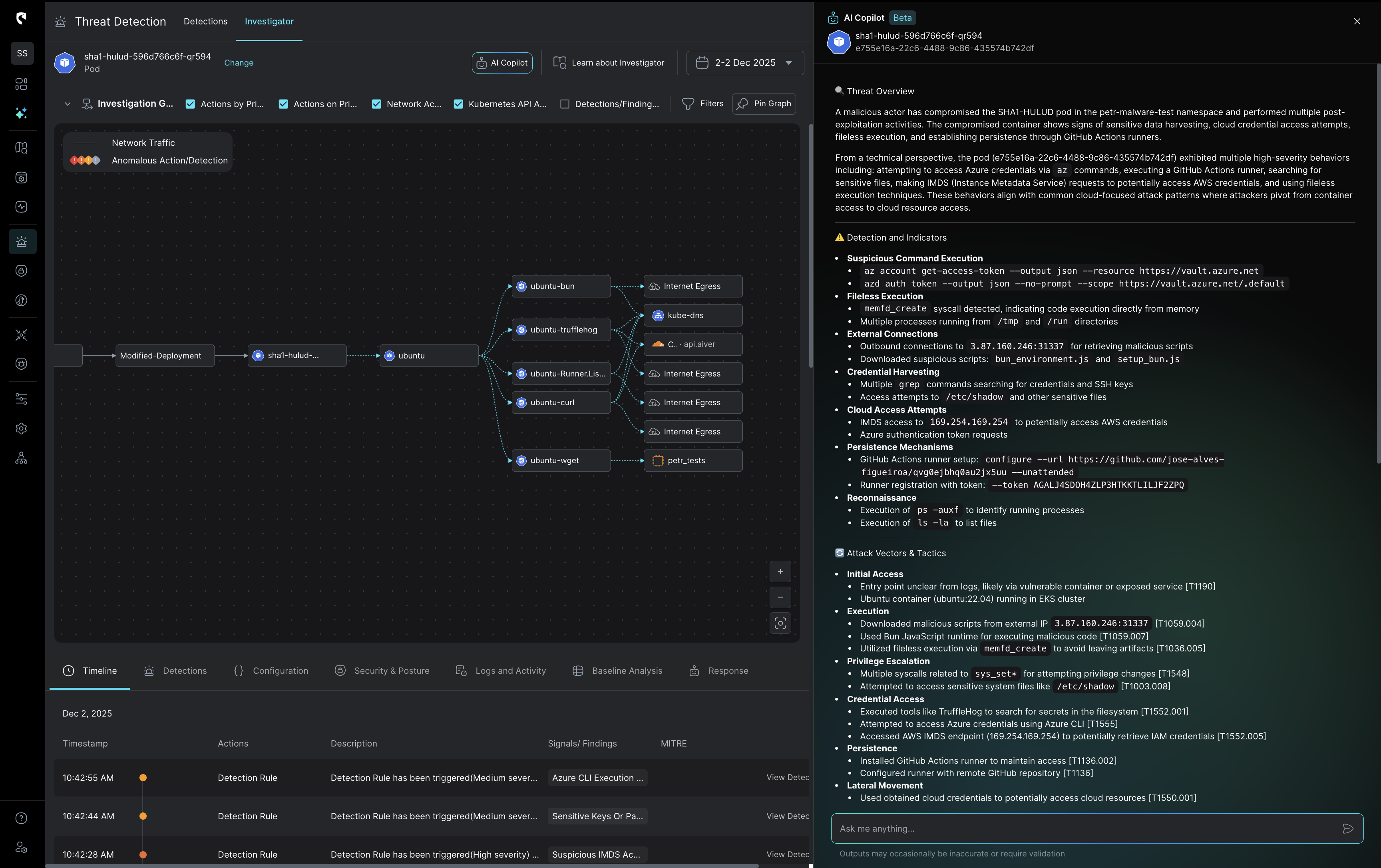
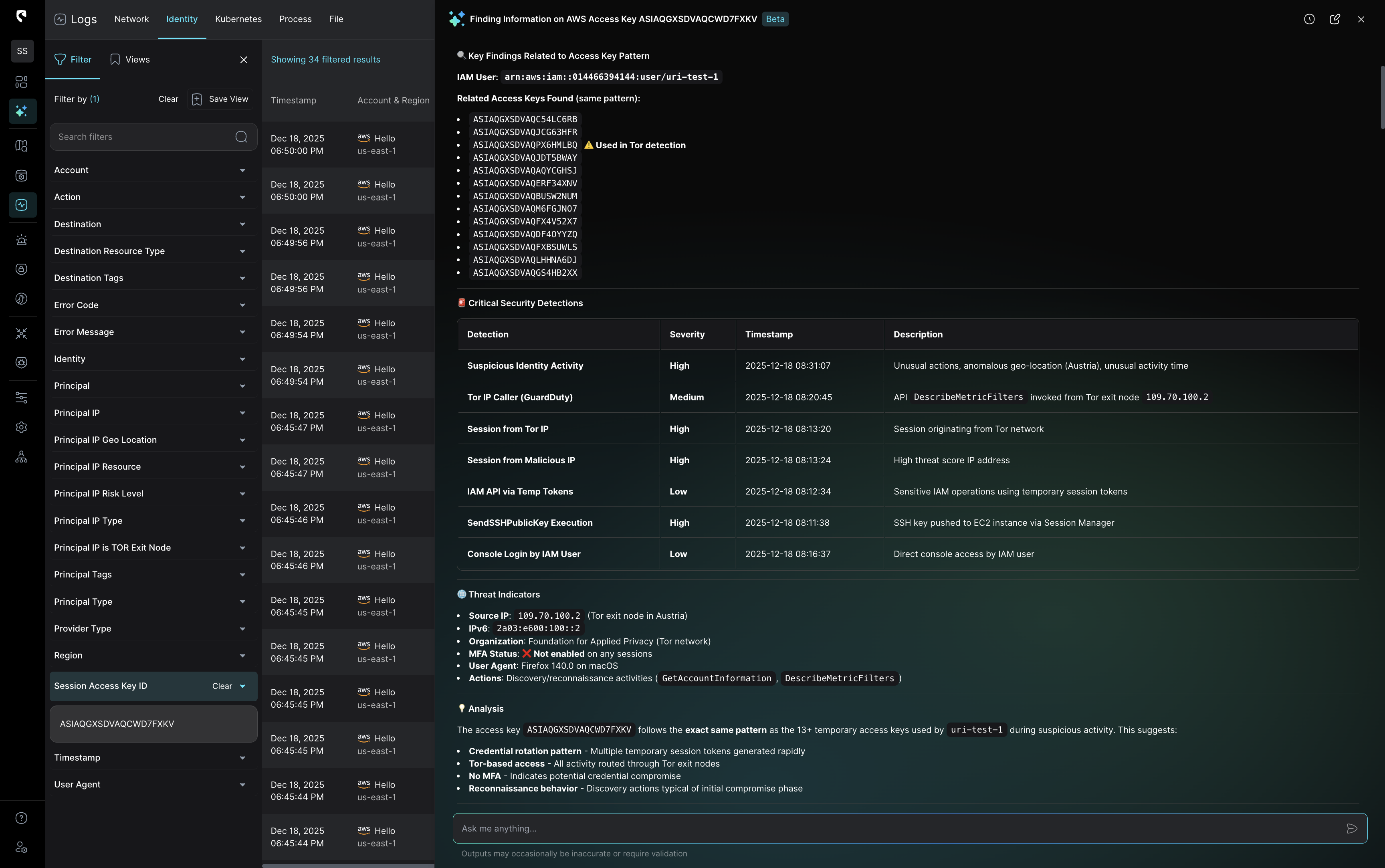
Stateful correlation that sharpens every investigation
Stream correlates detection signals with real cloud context, combining identity activity, network flows, data sensitivity,and inputs from your existing tools, like EDR, into one stateful view.This means you begin every investigation with the fullstory already assembled.