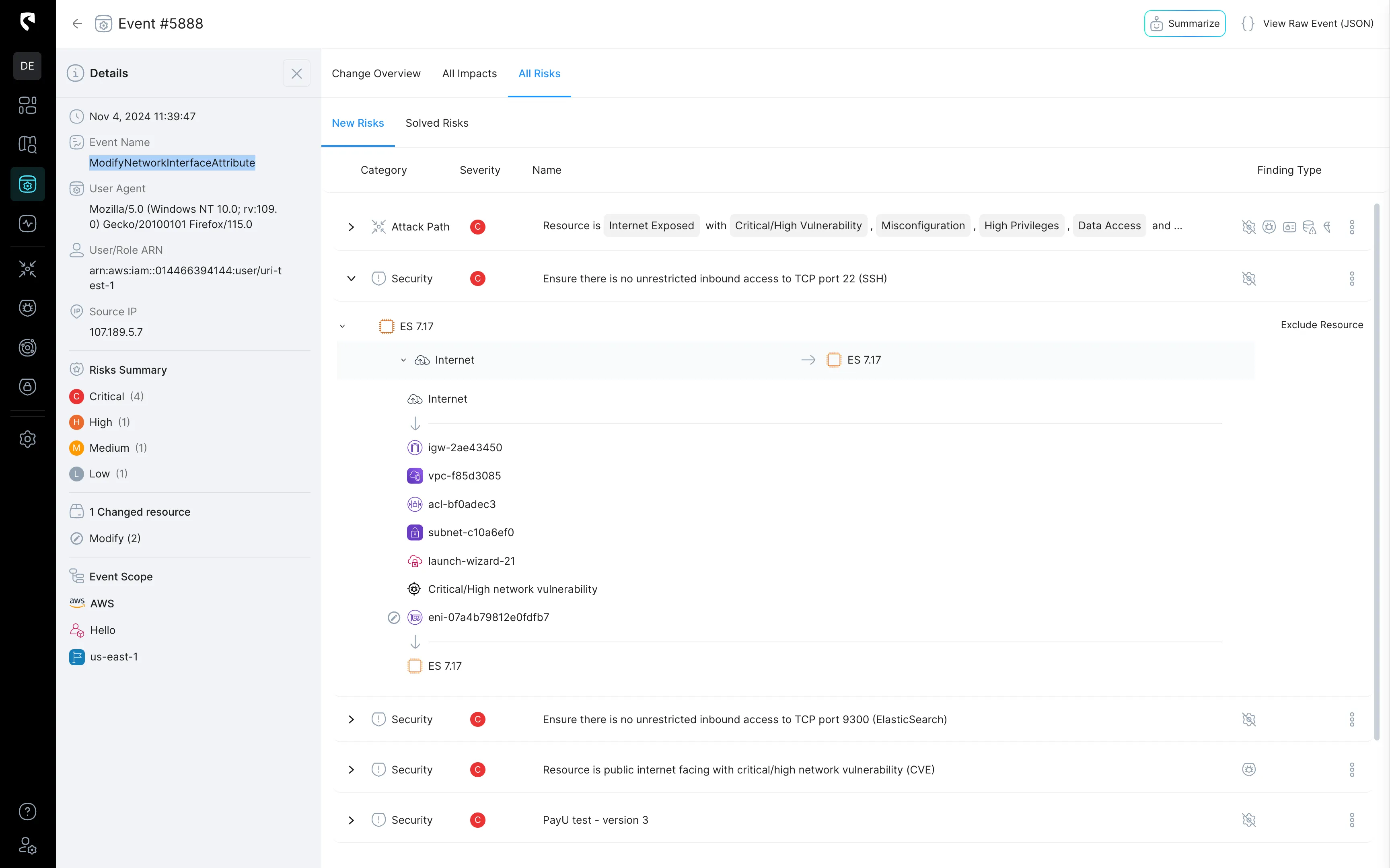
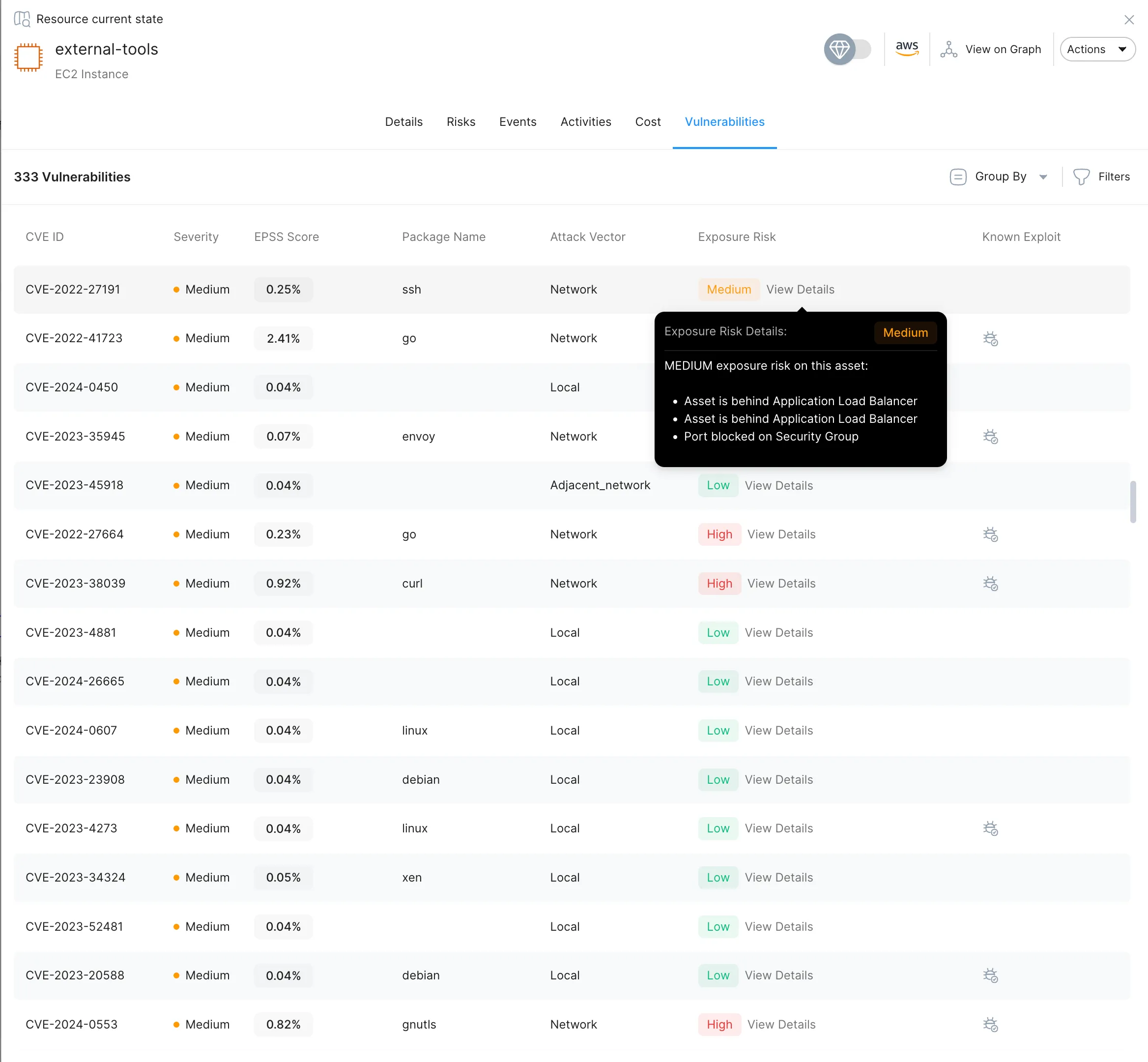
Equip Your Team to Defend with Confidence
Stream.Security empowers your SecOps team with actionable insights and the clarity they need to defend effectively. With advanced attack surface understanding, you gain the ability to see threats as attackers do—and respond with precision.