.png)

It’s impossible to protect what you don’t fully understand. The basic requirement is to know the characteristics of your assets, their potential vulnerabilities, and their current state. In cloud security, these characteristics are referred to as context.
Achieving full context requires considering multiple factors, and the more context available, the better. The cloud environment has many layers of context, including network reachability, identity (both human and non-human), and security control configurations. A cloud security solution must account for these layers to avoid generating a high volume of false positives. Without these data points, security tools can misinterpret legitimate activities as threats, wasting both time and resources.
To further exacerbate the challenge of getting the context, the cloud is a dynamic landscape which constantly changes. So even when getting the context, the challenge is to keep it aligned with the current state of the cloud.
Managing the high volume of alerts, many of which are false positives, is a constant challenge for security teams. These false alarms both drain resources and delay responses to real threats.
Stream Security’s approach moves beyond the initial detection by providing real-time visibility into how a threat can be exploited in the context of the environment. With insights into network reachability, identity exploitability, and runtime security policies, security teams can unveil the actual threat landscape and respond effectively to critical issues, while avoiding unnecessary distractions.
Let’s review Stream’s real-time context layers for cloud security:
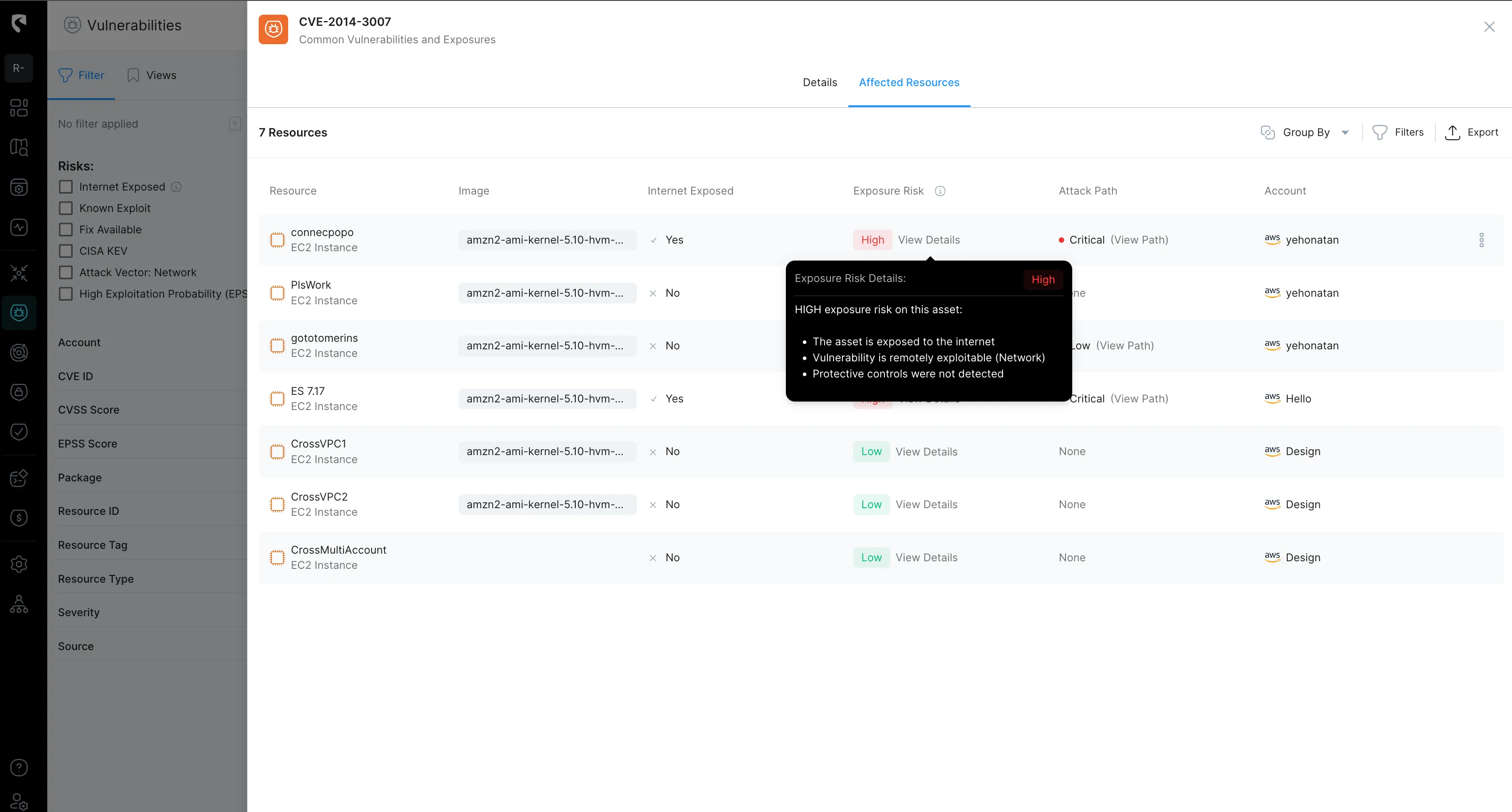
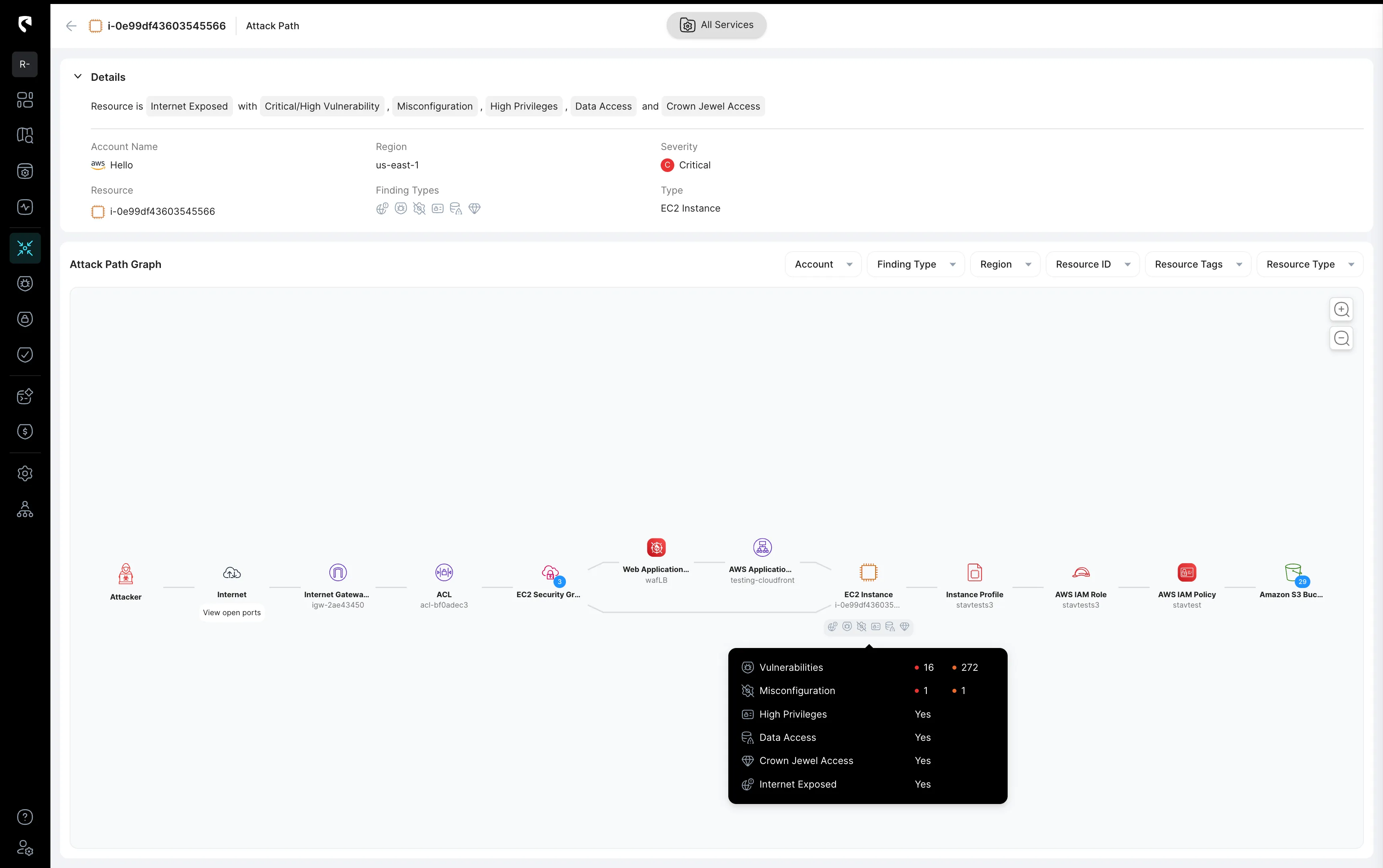
Real-Time Network Reachability - Obtain a clear understanding of how resources and services within your cloud environment are interconnected and whether they are exposed to external access. By evaluating network paths and permission flows in real time, you can prioritize the most critical alerts and ensure that risky alerts receive immediate attention.
Real-Time Identity - Gain clear insights into human and non-human identities by assessing current privileges and entitlements to identify risky permission combinations. Real-time identity context is crucial for clarifying security alerts, as it correlates alerts with active privileges and entitlements.
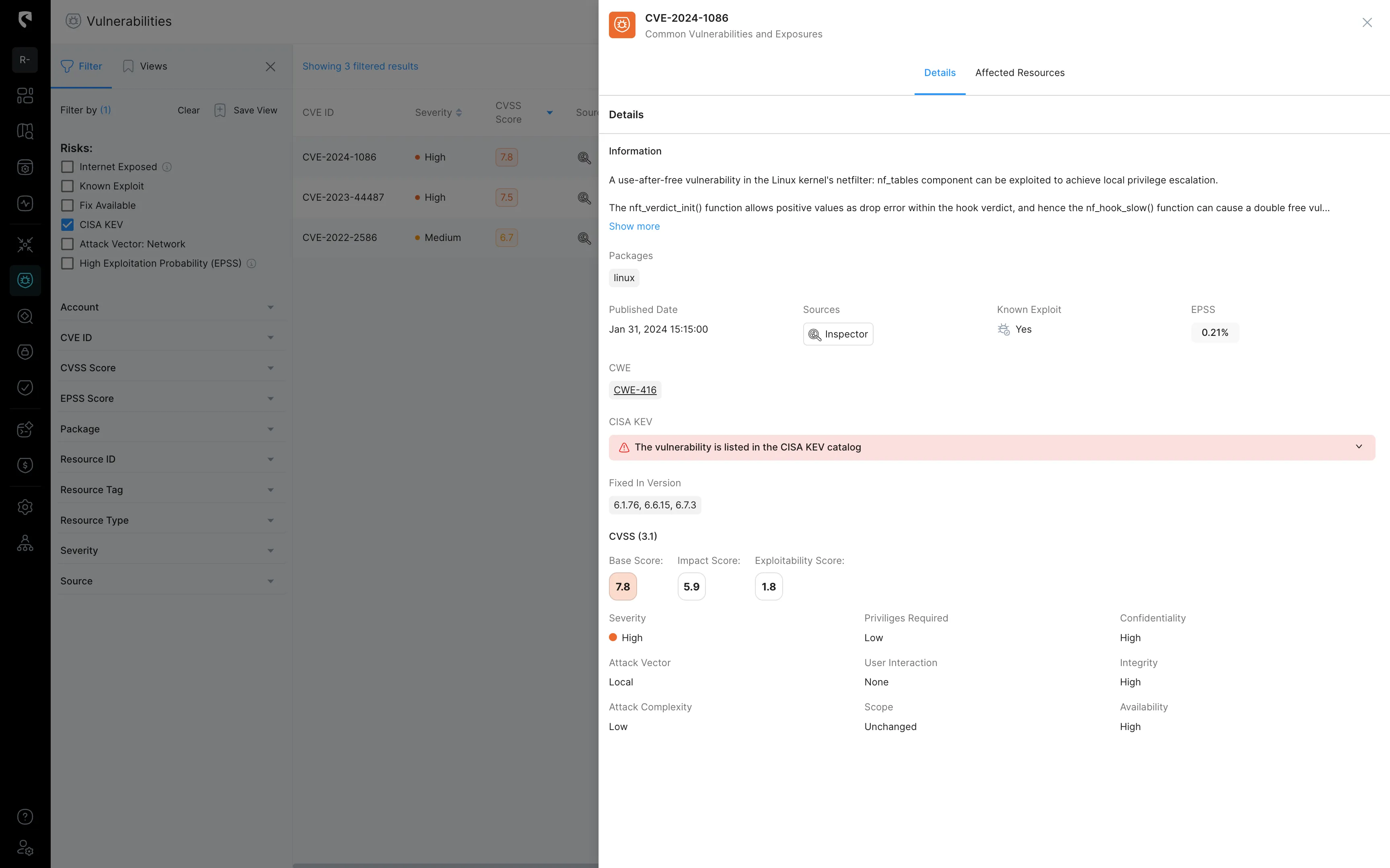
Real-Time Exposure – Not all assets are equally vulnerable. Real-time exposure analysis helps assess the severity of alerts by examining the exploitable weaknesses of potentially compromised assets. By understanding the specific vulnerabilities associated with an asset in real-time, you can more accurately determine the risk and prioritize response efforts based on the actual level of exposure.
Real-Time Security Controls – Even when vulnerabilities exist, they may already be mitigated by security controls in place to block potential exploits. Real-time visibility into your security control policies provides an additional context, allowing you to prioritize risks that aren't covered by other defense layers. By understanding which issues are actively protected and which remain exposed, you can focus your attention on the most pressing threats.
Effective security is about taking decisive action while having minimal disruption to the business. The more context you have, the better equipped you are to not only reduce false positives but also identify a broader range of mitigation strategies. Stream Security’s layered context approach enables security teams to tailor mitigation strategies based on operational realities, ensuring that responses are both effective and minimally invasive, preserving the goal of keeping the business running.
For example, when a vulnerability is detected in a testing environment, patching is a straightforward solution since downtime is tolerable. However, for vulnerabilities in a production environment, where uptime is mission-critical, teams may opt for other strategies, such as updating Web Application Firewall (WAF) rules, to mitigate the issue without affecting operations. This approach ensures that security efforts are both effective and aligned with business priorities.
A typical scenario could involve a Remote Code Execution (RCE) vulnerability on an EC2 instance, that became internet-exposed following a configuration change. This vulnerability could allow attackers to execute malicious code if not mitigated, leading to significant system compromise.
There are different alternatives to mitigate the risk:
Stream Security’s real-time visibility allows teams to make informed decisions, weighing these options based on the current threat landscape and operational demands, ensuring the right action is taken without compromising uptime.
Reducing false positives is essential for maintaining operational efficiency and focusing on real threats. Stream Security’s real-time layered context approach gives teams the visibility they need to prioritize genuine risks. By analyzing factors like network reachability, identity exploitability, and resource configurations in real time, teams can make smarter, faster decisions. This not only reduces the time spent on irrelevant alerts but also helps to enrich the mitigation strategies, improving overall security efficiency.
Ensure your cloud environment remains secure by leveraging Stream Security’s real-time insights and mitigation strategies.
Book a demo with one of our security experts to learn how you can enhance your cloud security with the power of real-time context and protect your infrastructure effectively.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.


.png)
