The summer’s biggest security conferences just ended, with great research presented by the best security engineers in the industry from around the globe. Many of the tools presented were around new offensive techniques and recently uncovered vulnerabilities. Within the security community, vendors use this information to improve their defense solutions, validating detection capabilities to ensure that clients are secure.
One such project proposed at DEF CON 2025 was the open-source EntraGoat created by Security Researchers at Semperis. Let’s dive in to see how the tool works and how it helps our community.
GOAT projects started to appear around 2020 - developed as a playground by hackers, for hackers. Pentesters and Red Teamers could hone their skills in the GOATs with the goal of simplifying deployment of lab infrastructure with built-in common vulnerabilities and misconfigurations. Since then, many GOAT project have been launched to cover the most popular modern technologies: Microsoft Active Directory, Amazon web Services, Kubernetes, and more. In 2025, EntraGoat joined the family as the latest in a string of successful projects.
Security providers (like Stream.Security) use GOAT projects to validate detection capabilities and ensure their tools can provide the best defense against attackers.
According to the Semperis researchers who created the tool, Jonathan Elkabas and Tomer Nahum,
"EntraGoat is a deliberately vulnerable Microsoft Entra ID infrastructure designed to simulate real-world identity security misconfigurations and attack vectors. EntraGoat introduces intentional vulnerabilities in your environment to provide a realistic learning platform for security professionals. It features multiple privilege escalation paths and focuses on black-box attack methodologies."
Currently, EntraGoat contains six scenarios. And if you have Stream.Security deployed in your organization, you will see that exploitation of all six attack scenarios was successfully detected in real time. (🎉)
In this blog, we’re going to analyze a few of those scenarios to see how Stream’s platform was able to detect and conduct full forensic analysis on the scenarios in just a few minutes.
Let’s take a look:
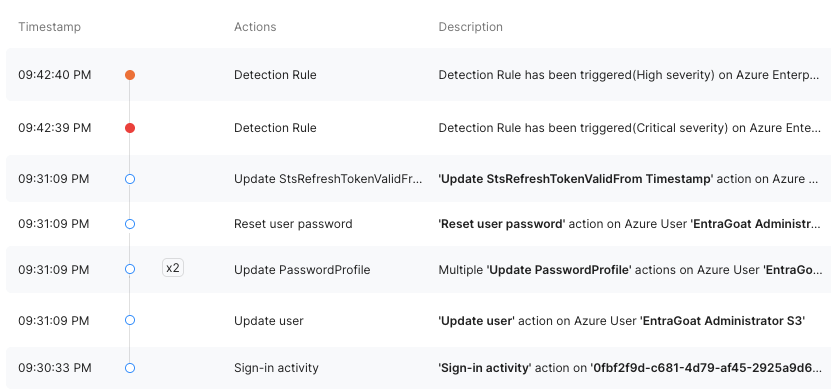
The kill chain is this scenario is very simple, but very realistic.
Stream.Security successfully caught High/Critical steps of this scenario such as:
However, detections themselves are just half the story. Threat investigation processes can span multiple weeks - or even a month. With Stream.Security, investigating Scenario 3 took just a few minutes.
In Stream’s platform, analysts can see how all related logs are grouped together into a single security incident and presented as a visual historic chain of action that led to compromise. As a result, SOC analysts managing the case will immediately see a clear picture of the incident that includes the step-by-step attack process based on related logs and Indicators of Compromise (IOCs) only.
.png)

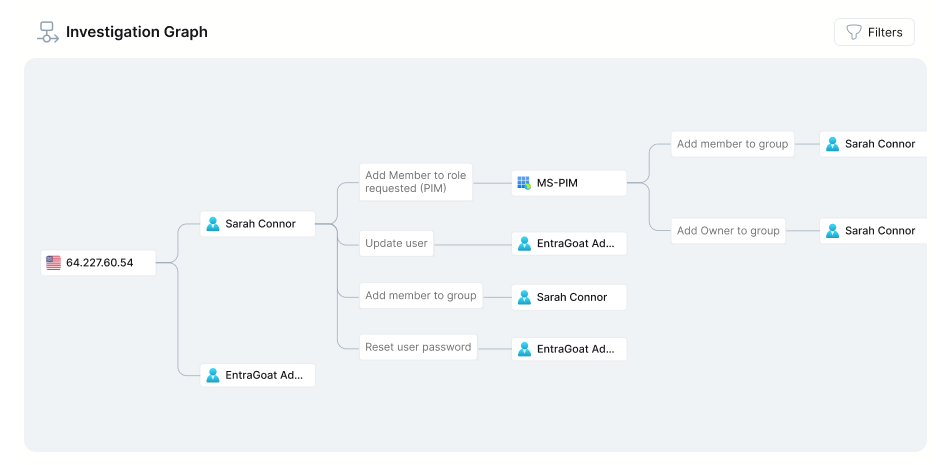
Let's have a look at another scenario from EntraGoat, Scenario 5:
In this more complex case, visualization can be a major challenge for SOC analysts using logs to track attacker behavior. In Stream.Security’s platform, bringing together all related activities into one storyline is easy. Stream automatically reconstructs the attack storyline, mapping all user behavior, identity changes, and infrastructural events that enable attack proliferation in real time. Analysts can reduce MTTR (Mean Time to Respond) and other key KPI metrics that the SOC is measured on with faster triage and deeper investigations in order to make high-confidence decisions without drowning in data.
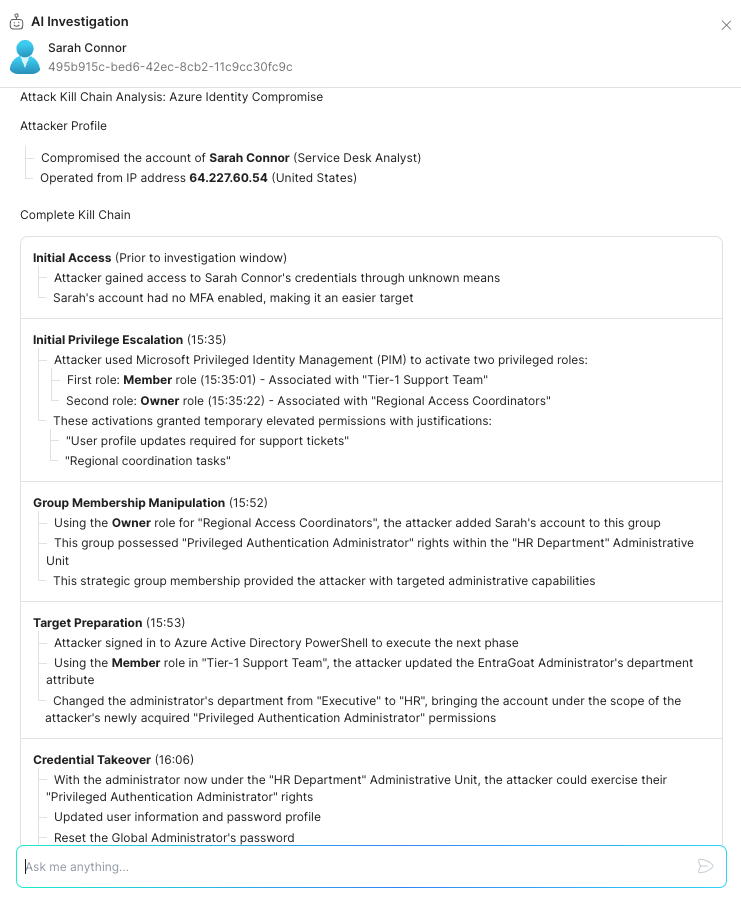
Stream’s AI Investigator brings the platform’s capabilities to another level, allowing SOC analysts at any level to be empowered with complete knowledge of cloud-native attacks (in this case, Microsoft Entra ID). The Investigator groups together events across the entire attack storyline to present a clear, natural-language summary of events so that analysts at any tier will be able to follow the attacker’s intent throughout the kill chain. After presenting the investigation, response recommendations are given so teams can mitigate the breach with precision and minimal downtime.
Here’s the AI Investigator’s summary of Scenario 5:
Kudos to the Semperis team for building EntraGoat. The scenarios demonstrated in EntraGoat provide security engineers with the ability to hone their skills within a playground environment. Tools like EntraGoat are crucial to advancing our industry, enabling hands-on learning that strengthens security teams everywhere. This makes defense groups, and organizations as a whole, more resilient against modern attacks - especially those that leverage the complexities of the cloud to cause damage.
As more analysts learn to mitigate cloud-native attacks, the security organization’s posture and maturity significantly improves. But this process takes time and investment in a threat landscape that is moving faster than analysts can keep up.
With Stream.Security, organizations can operationalize what EntraGoat teaches by detecting and responding to similar attack paths in real time. Stream empowers security teams to respond to cloud-native attacks with speed, precision, and context, no manual log correlation or additional headcount required.
Tools like EntraGoat expose how identity-driven attacks unfold in the cloud. Stream.Security ensures you can detect and respond to them instantly, operationalizing those lessons in real time with zero friction.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
