
Stream now integrates with Salesforce for advanced threat detection. The integration provides in-depth detection capabilities that will help you catch Salesforce breaches in real time, including the recent Salesloft Drift compromise.
Salesforce is one of the world’s most popular CRM platforms, enabling businesses to manage their interactions with customers in a single, cloud-based system. Instead of relying on spreadsheets or disconnected apps, users can leverage Salesforce to analyze data to understand customer behavior and trends, track sales opportunities, run targeted marketing campaigns, and provide customer service and support.
As such, Salesforce stores sensitive customer data, including PII (Personally Identifiable Information), email addresses, customer contacts, account histories, internal case records, and other business-critical data.
Over the years, this has made Salesforce a top target for attackers, seeking to monetize sensitive business data to make a profit.
Only this year, two notable data breaches involving Salesforce were reported worldwide. The first, which took place between June and August, was a large-scale social engineering campaign where the ShinyHunters APT Group (AKA UNC6040) impersonated IT support and tricked employees into installing a fake Salesforce Data Loader or approving a malicious OAuth app. This in turn gave attackers valid Salesforce tokens and credentials, which they abused to quietly export CRM records at scale, impacting dozens of companies with millions of customer contacts, loyalty program details, and case notes stolen. This was not a vulnerability exploitation, but a simple abuse of human trust and the OAuth integration mechanism.
The most recent breach, which has been widely discussed across the security community, originated in Drift, a sales & marketing chatbot platform acquired by Salesloft in 2024. Drift is widely used in public-facing websites and in sales workflows, providing real-time chatbots for site visitors. To enrich these interactions, Drift integrates with CRMs like Salesforce: it qualifies leads, books meetings, routes inquiries to sales reps, and pulls customer/account information directly from Salesforce.
For this integration, Drift connects to Salesforce using OAuth, a static refresh token which can be exchanged for a short-lived access token whenever the chatbot needs data. These tokens typically grant permissions to read account and contact records, access opportunities, leads, or cases, and in some cases create or update records.
Between March and June 2025, an APT group known as UNC6395 (AKA GRUB1) accessed Salesloft’s GitHub account, where they downloaded content from multiple repositories, added a guest user, and established malicious workflows.
Later, the attackers shifted to Drift’s AWS environment, where they obtained OAuth tokens tied to Drift–Salesforce and Drift–Google Workspace integrations.
With valid tokens in hand, the attackers impersonated Drift and authenticated directly into Salesforce environments, and, in some cases, Google Workspace as well. Because OAuth tokens bypass interactive logins, no passwords or MFA prompts were triggered. Once initial access was achieved, the attackers began with reconnaissance, enumerating accessible Salesforce objects and schemas, and identifying high-value targets such as Accounts, Cases, and Opportunities. At this point, the threat actors moved to exfiltration, abusing SOQL queries and the Salesforce Bulk API to pull large datasets. In some cases, they conducted defense evasion tactics and deleted query jobs/logs to reduce visibility and erase traces.
One particularly concerning finding was that support case content often contained plaintext credentials and tokens (e.g., AWS keys, Snowflake tokens, API secrets), which gave attackers opportunities to pivot into other cloud services. When the breach became public, Salesloft revoked all Drift tokens and suspended the app. But by then, organizations such as Cloudflare, Palo Alto Networks, and Zscaler had already reported exposure and were forced to rotate tokens at scale.
This attack is another example of a compromise that leverages valid authentication mechanisms for malicious purposes. Notably, diving into Salesforce Audit Logs could have exposed these anomalies early, before attackers were able to exfiltrate data or pivot into cloud environments.
Today, we’re introducing our new Salesforce Audit Logs integration for advanced threat detection. Built to address the growing risks of misuse and exploitation in Salesforce environments, this integration delivers a multi-layered detection framework that combines behavioral profiling, machine learning, threat intelligence enrichment, and out-of-the-box rules.
With it, you can spot suspicious or malicious activity in real time across the full attack chain, from reconnaissance to exfiltration.
Our detection engine establishes a baseline of normal Salesforce activity, then highlights anomalies such as first-seen queries, unusual login times, sudden spikes in SOQL query and event volume, or access from suspicious geolocations.
Events are automatically enriched with external threat intelligence, enabling proactive alerts on activity tied to malicious IPs, TOR exit nodes, or other IOCs. Pre-built detection rules further accelerate visibility into known attacker techniques like bulk API abuse, report exports, and malicious OAuth app usage.
For organizations with unique workflows, we support Bring Your Own Detection (BYOD), allowing you fine-tune rules and reduce false positives, add your own custom rules, and tailor detections to your Salesforce environment.
To illustrate the value, here’s how our detections would have surfaced the Salesloft-Drift attack impacting Salesforce:
This multi-layered detection approach allows you to detect not only complex incidents like Salesloft-Drift, but also insider misuse, misconfigurations, and emerging SaaS-specific threats.
SaaS is now a primary attack vector, as OAuth flows, third-party integrations, and supply-chain trust introduce serious risk. Once initial access is secured, the cloud becomes the blast radius, with attackers quickly pivoting into AWS, Snowflake, and other connected systems. That’s why detection must be unified across SaaS and cloud, linking SaaS entry points to cloud impact clearly and quickly in order to build better response.
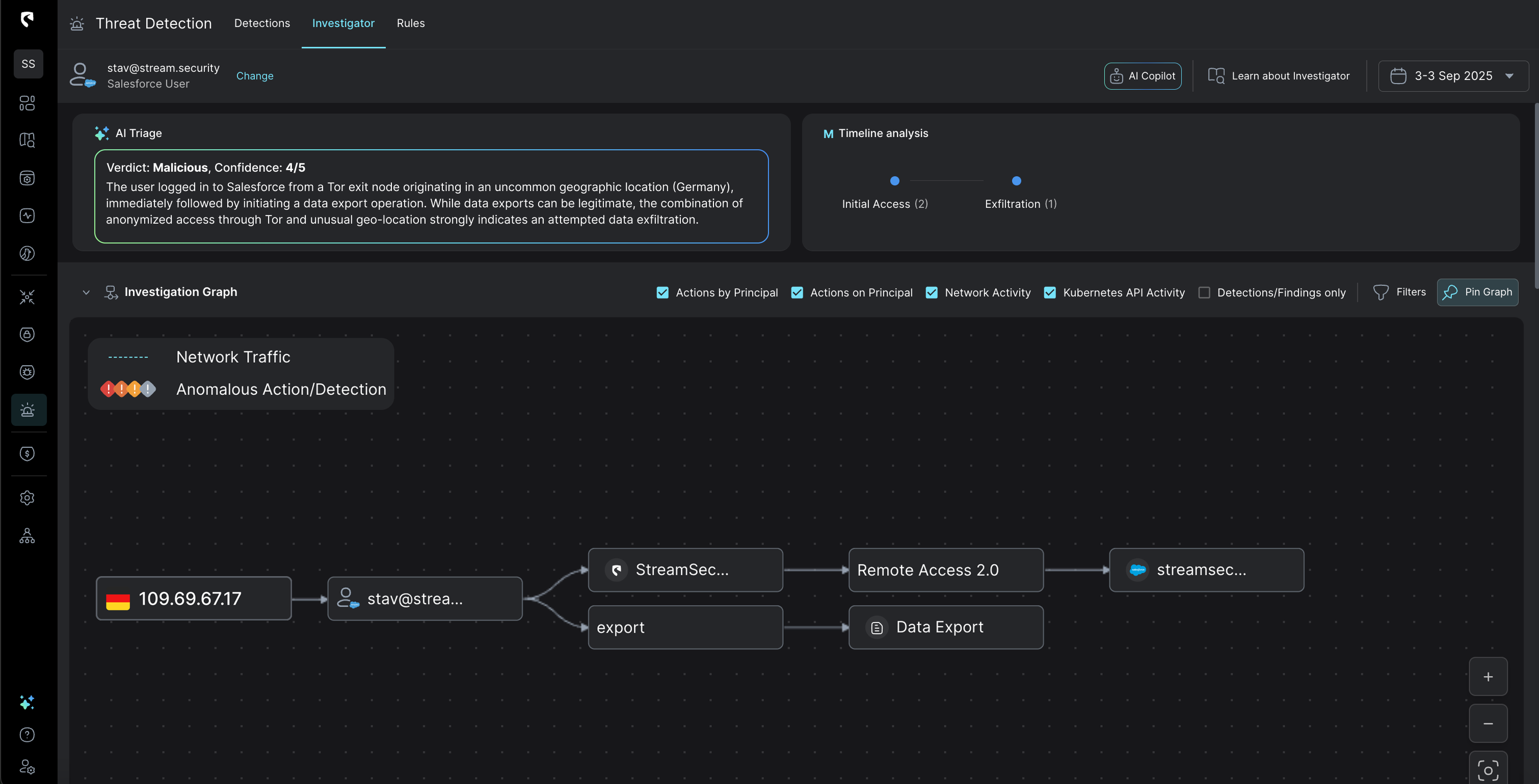
When an alert is triggered, you can dive into related Salesforce events and alerts, review enriched IOC context, and cross-correlate findings with other cloud signals in the Stream Investigator.
To accelerate and focus your triage and investigation, Stream’s AI Copilot assists directly in the Stream CDR platform. It is trained to automatically enrich the alert, investigate its context, highlight potential root causes, and provide actionable mitigation steps to help you respond quickly and effectively.
With Stream’s Salesforce integration, gain the visibility and detection needed to defend against breaches, insider misuse, and advanced Salesforce threats.
Speak to our team of experts to see it in action by clicking here.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.


.png)