
We just released an integration with GitHub Audit Logs! 🥳
This integration is designed to address a wide range of GitHub threats by providing deep visibility into GitHub activities and enabling real-time detection of malicious behavior through Stream’s advanced detection mechanisms.
Investigate and respond to GitHub threats quickly, with the context you actually need to take the right action.
Stream Security is a Cloud Detection and Response (CDR) platform built to provide real-time visibility that enables detection, investigation, and response across the modern cloud stack.
Our platform correlates cloud-native telemetry, user behavior, and audit data across environments to understand real posture impact, uncover threats early, and enable fast, context-rich investigation and response.
As modern development shifts to the cloud, platforms like GitHub have become an extension of the enterprise cloud environment and a critical part of the attack surface. Yet most SOCs still treat GitHub as a DevOps tool, leaving blind spots in coverage.
With the new GitHub Audit Logs integration, Stream Security’s coverage now extends to one of the most critical areas of the attack surface - the software supply chain. This way, GitHub can be placed under the same security umbrella as your cloud infrastructure, identity systems, and SaaS platforms. SOC, AppSec, and DevSecOps teams can now use one platform to detect and respond to cloud threats.
GitHub is the most widely used platform for code hosting and collaboration for organizations of all sizes. CI/CD workflows are dependent on GitHub as the tool that manages and stores some of an organization’s most valuable assets - their proprietary code.
But what happens when attackers recognize that same value?
In recent years, GitHub has become a prime target for attackers of all types. From opportunistic threat actors to ransomware gangs and nation-state APT groups, GitHub now plays a main role in modern cyberattacks.
Digging a bit deeper into the statistics reveals why: over the past year, more than 22.8 million hardcoded secrets were found in public GitHub repositories, and 35% of private repositories contained at least one plaintext secret.
Recent attacks abusing GitHub have taken many forms. Phishing campaigns observed in the wild have exploited GitHub’s trusted brand to distribute various malware strains (notably the Lumma Stealer). Researchers have also identified malicious GitHub Apps designed to hijack user accounts. Attackers have also been seen abusing fake GitHub comments, bogus “Security Alert” issues, and deceptive "fixes" to steal credentials and trick developers into running malware on their own systems.
More advanced threat actors, including ransomware groups, have gone further - leveraging exposed tokens and hardcoded secrets in GitHub repositories as entry points into environments. These footholds often lead to data theft, privilege escalation, and ultimately, ransomware deployment for extortion.
Here’s one of the most striking examples of the risks:
In the recent supply chain attack involving tj-actions, a single compromised GitHub Action enabled attackers to silently propagate malicious code to over 23,000 repositories.
But what’s often overlooked is that many of these attack behaviors - such as unusual access patterns, permission abuse, or token usage - can be detected early through GitHub Audit Logs.
And this is where Stream’s new GitHub Audit Logs integration comes in.
GitHub Audit Logs (available to GitHub Enterprise customers) offer in-depth visibility into activities across the enterprise, organization, and repository levels. This feature logs a wide range of actions - from code-related operations like git pull, commit, and merge to administrative events such as repository clones and downloads, changes to repository visibility, the addition of members and external collaborators, creation and deletion of organizations or repositories, permission changes, and the disabling of built-in GitHub security controls.
Audit logs enable quick review of these activities, providing critical context on who performed the action, what was done, and when it occurred.
Our GitHub Audit Logs integration is designed to help security teams address the growing risks of GitHub abuse and exploitation. After analyzing a wide range of real-world attacks and threat patterns, we developed a detection framework that identifies suspicious or malicious activity in real-time.
We support multiple detection types tailored to the unique nature of GitHub threats:
Our machine learning engine automatically fingerprints GitHub activity to establish a behavioral baseline and detect anomalies in real time. It identifies a variety of deviations from normal activity, such as:
This mechanism is designed to identify rare or unexpected GitHub behavior, aiming at uncovering early signs of compromise.
The ML engine dramatically reduces false positives by learning your organization's GitHub usage patterns. You can also define custom exclusion conditions to fine-tune detections and receive alerts only for meaningful deviations.
We enrich GitHub Audit Log events with threat intelligence, including known malicious IP addresses and TOR exit node usage, to power IOC-based detections. This helps identify high-risk activity that may otherwise go unnoticed in raw logs.
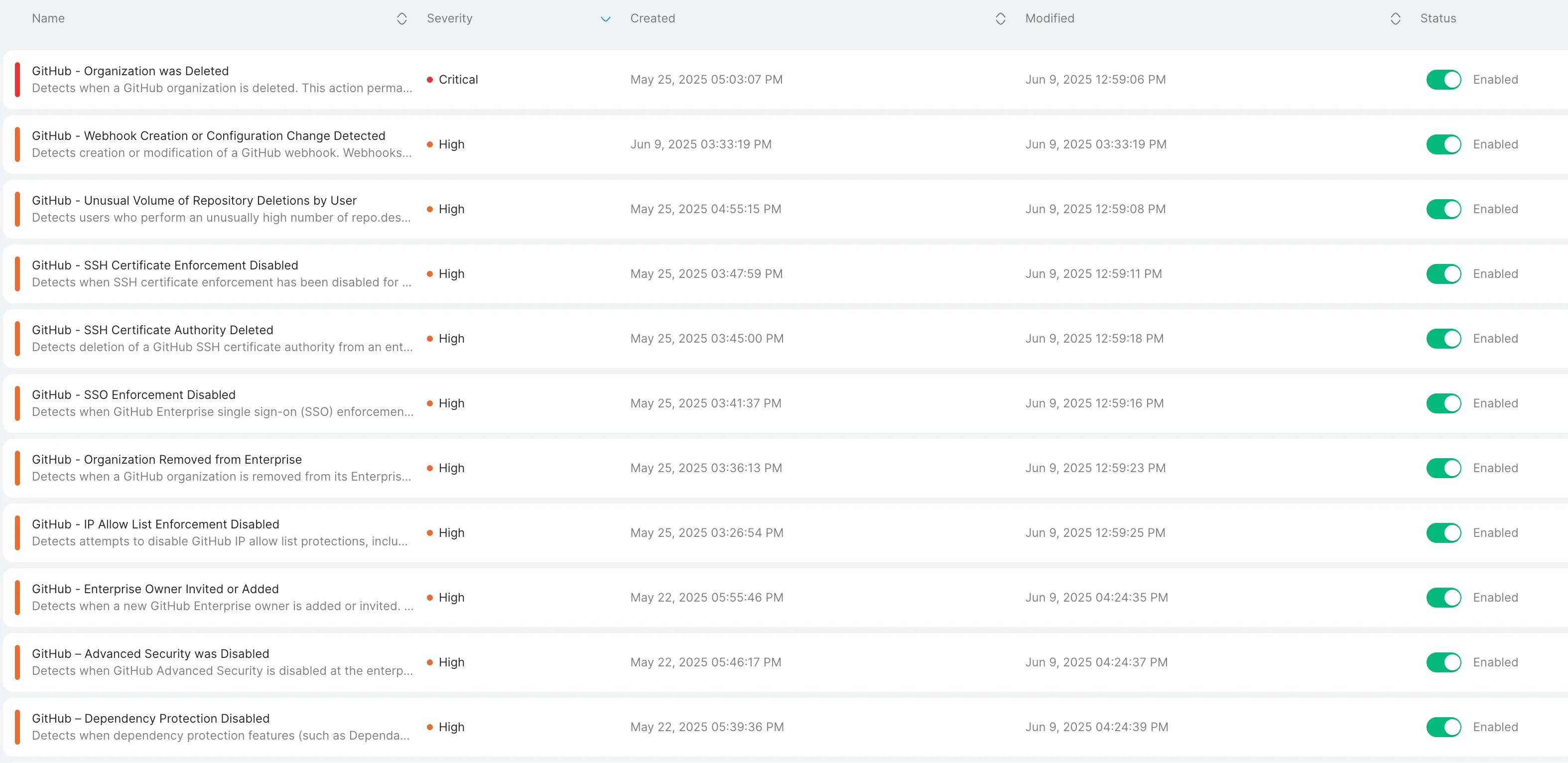
We’ve developed 30+ prebuilt detection rules based on research into real-world GitHub threats. Some examples include:
These rules offer immediate coverage of common GitHub abuse techniques seen in recent attacks in the wild.
Alongside our built-in detections, you can also create your own detection strategy against GitHub threats. Create custom rules based on your organization’s GitHub workflows and usage routine. Whether you want to fine-tune the ML engine or write specific logic for your environment, our platform supports:
This empowers your team to detect real threats while minimizing false positives and alert fatigue.
.webp)
Once suspicious behavior is detected, an alert is triggered. You can quickly triage it by reviewing related GitHub events, analyzing enriched IOCs to attribute the behavior, and correlating activity with cloud-native context.
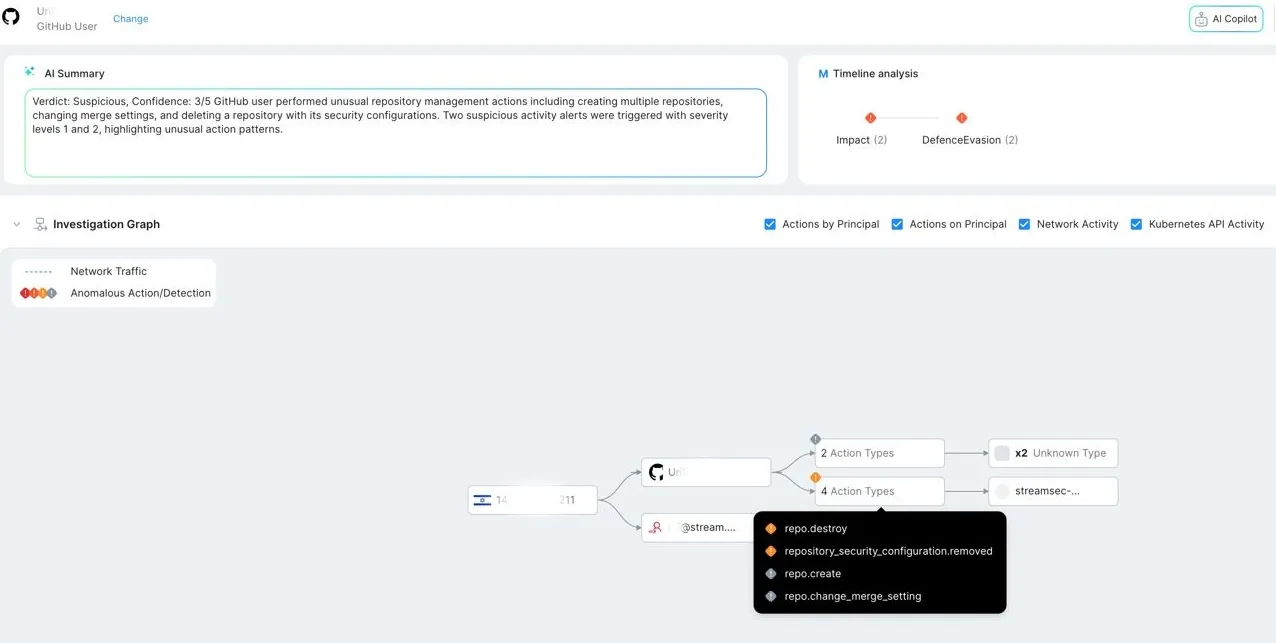
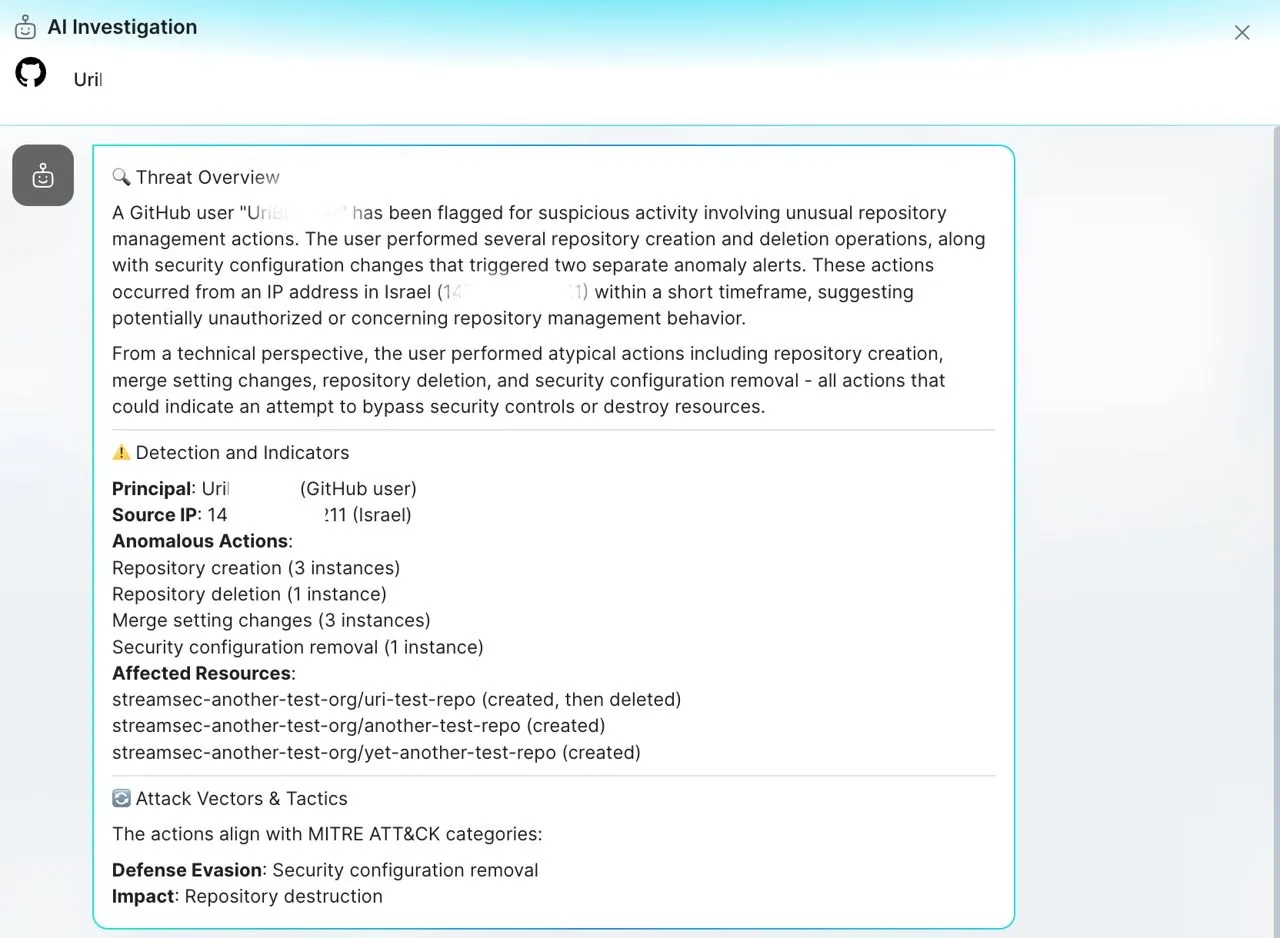
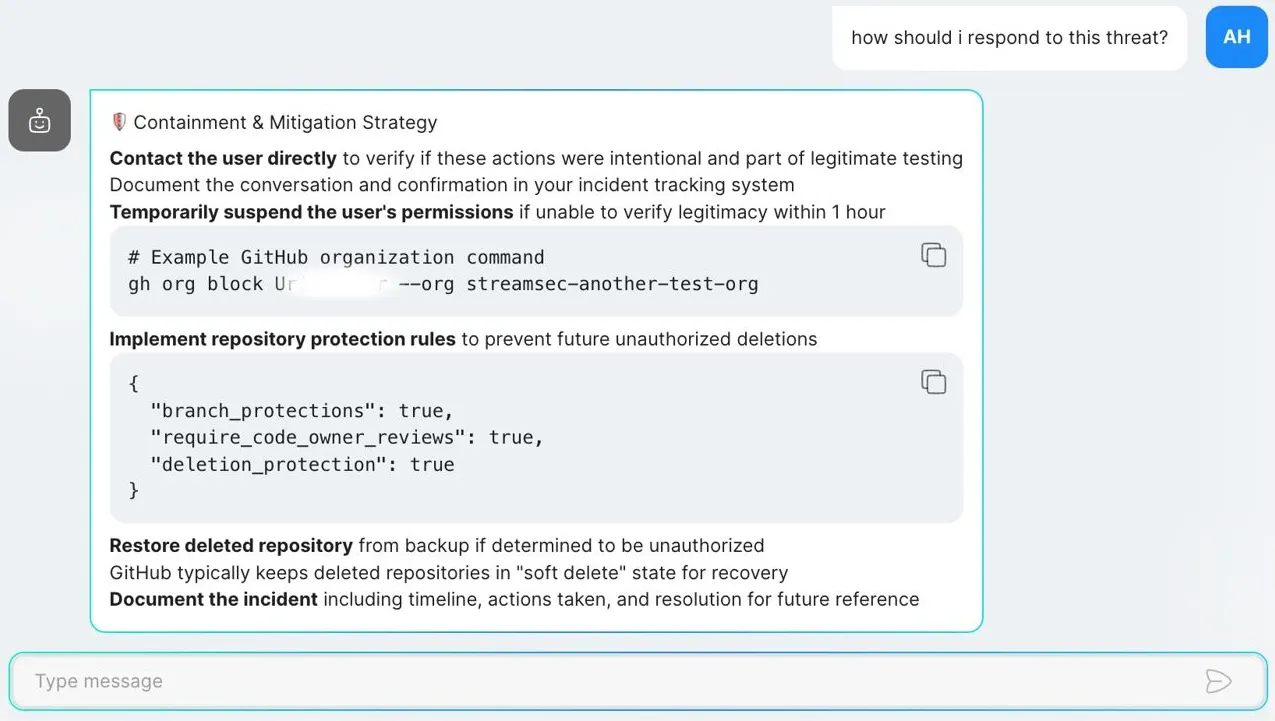
You can also use our AI Copilot to triage and investigate alerts using natural language. The Copilot is trained to automatically enrich the alert, investigate its context, and provide actionable mitigation steps to help you respond quickly and effectively.
If your SOC, AppSec, or DevSecOps team is looking to:
This integration was built for you.
👉 Want to see it in action? Request a demo to speak to one of our experts.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
