As a DevOps engineer, there are cases where you need to provide cross-account access to the objects in your AWS account.
If you want to achieve that, you can use the cross-account assumption of IAM roles or resource-based policies. However, there are several problems when implementing these methods:
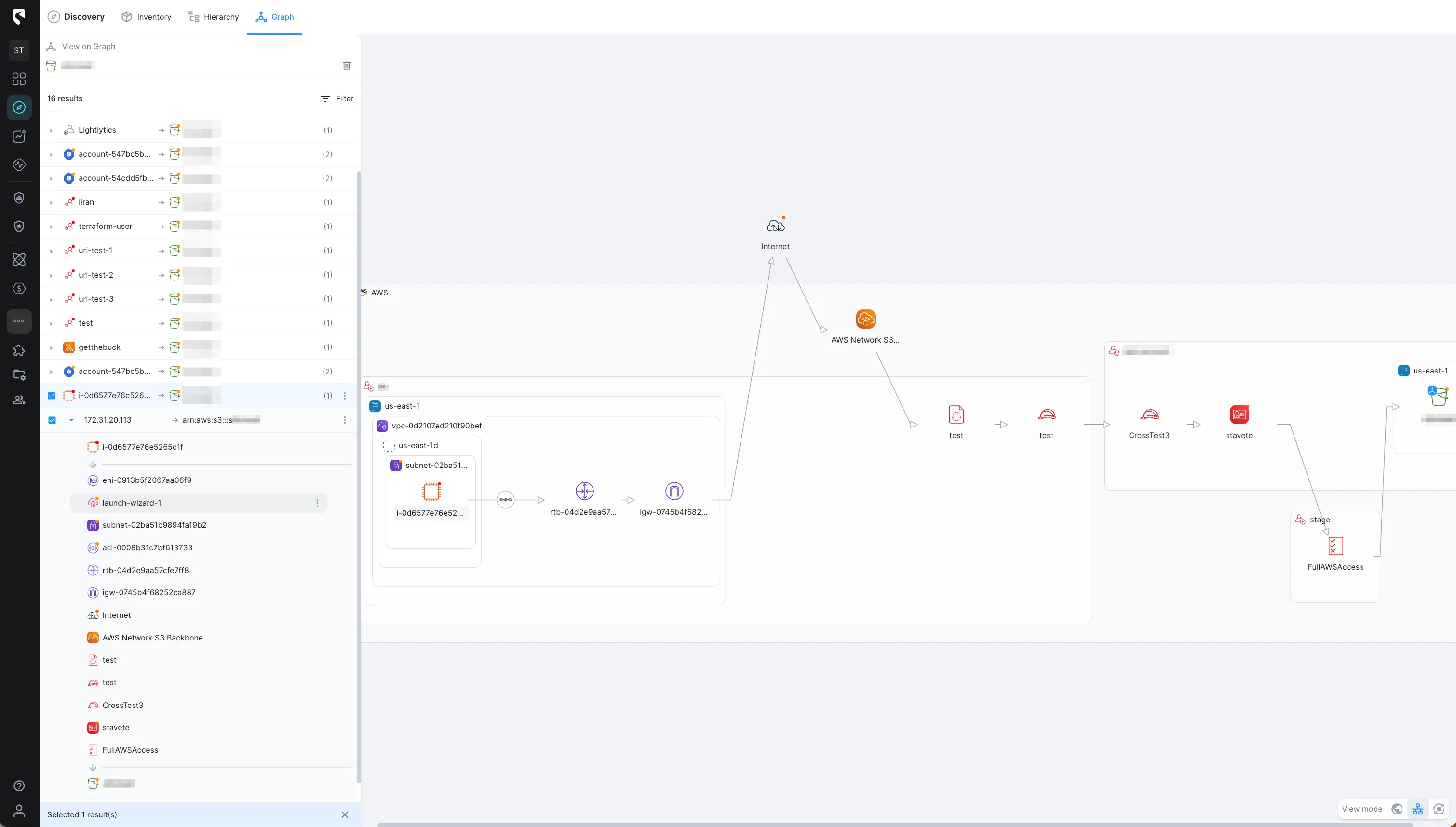
With Stream Security, you can eliminate all of the above concerns and gain control of your cross-account access! Now we supports all methods of cross-account assume role, and will help you understand which resources and even users have access to another account, via which configuration.
Start using Stream Security to gain control over your existing infrastructure and design changes easily, and risk-free.
Cross-account IAM Roles are used to define access to resources within a single account, but they are not restricted to a single account. For example, The EC2 servers in your staging environment can safely get access to an S3 bucket in production by using a properly defined role to do so. Cross-account Role is the right tool to comply with best practices and simplify credential management, as it eliminates the need to manage third party credentials.
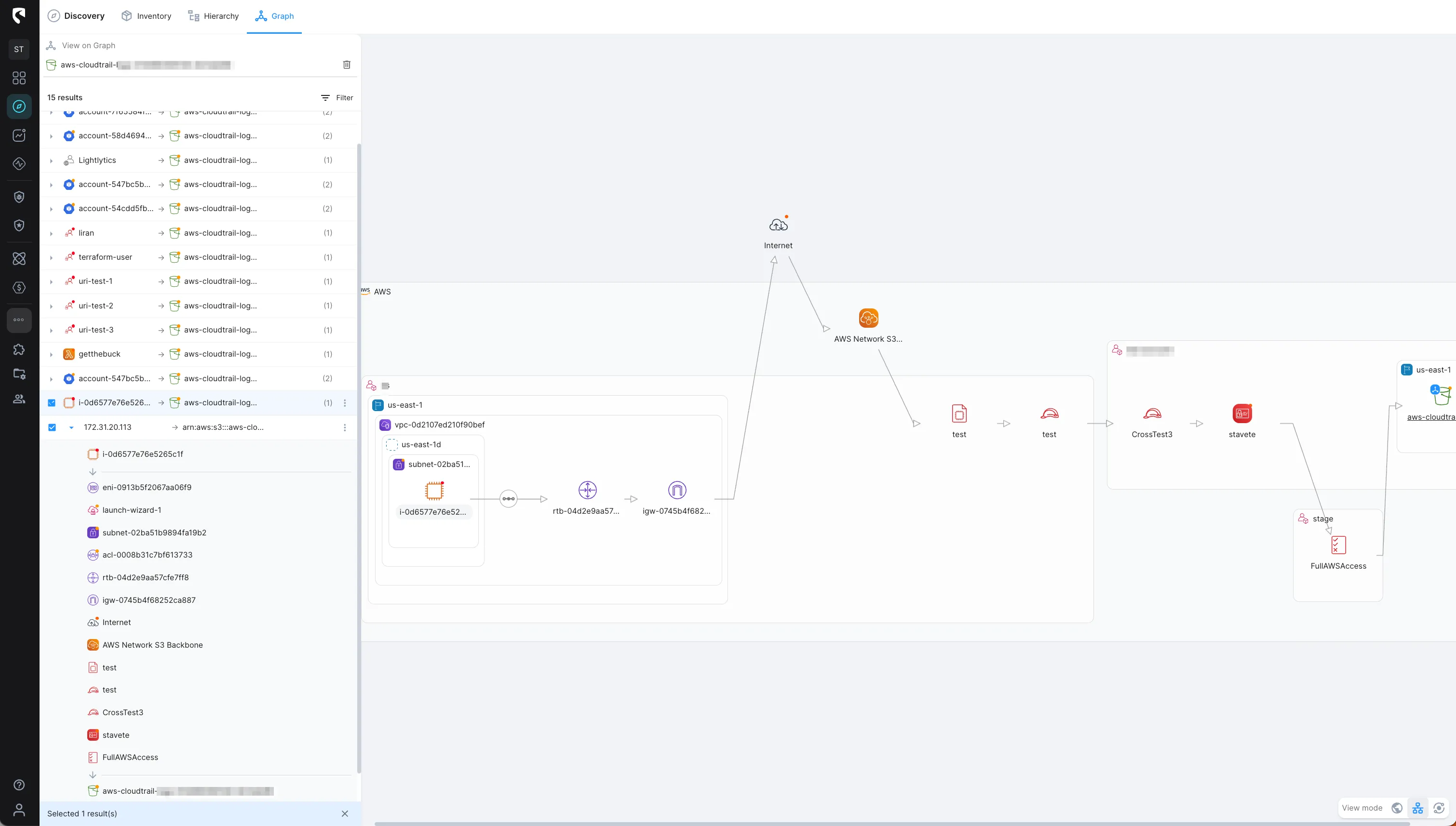
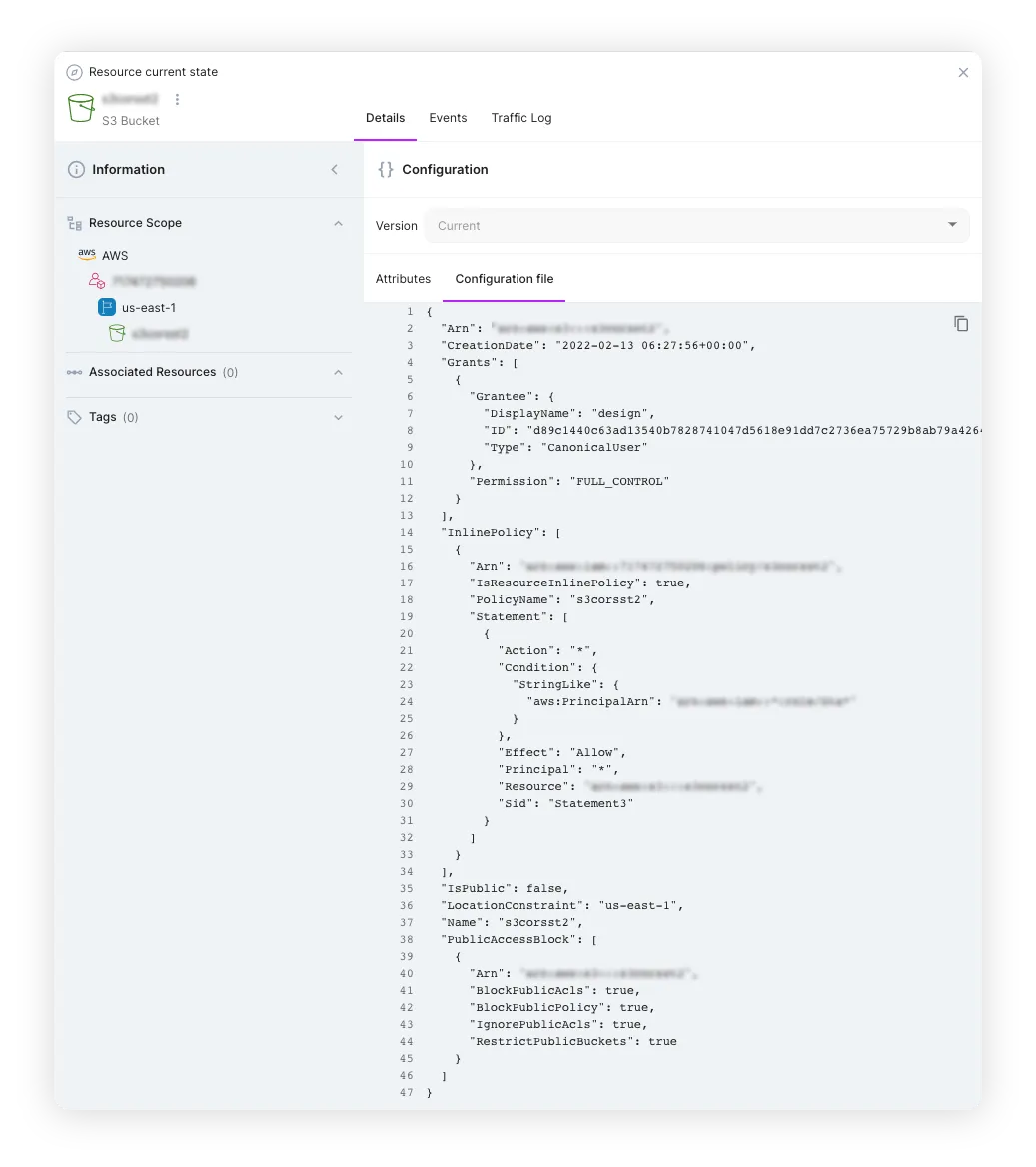
With Resource-based policies, you can also grant cross-account access to your resources. Instead of using a role as a proxy, you can attach a policy directly to the resource you want to share. The resource that you want to share must support resource-based policies.
A resource-based policy with cross-account access has an advantage over a role-based policy. If a resource is accessed via a resource-based policy, the user still works in the trusted account and does not have to give up its user permissions in place of its role permissions. In other words, the user continues to have access to resources in the trusted account at the same time as he has access to the resource in the trusting account. This is useful for tasks such as copying information to or from the shared resource in the other account.
Click here to Start your free trial now!
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
