
Today, we’re excited to roll out our SaaS-sourced threat detections, built to give SecOps teams complete visibility across the services powering their cloud. Stream’s SaaS detections extend our end-to-end visibility beyond all cloud layers to include SaaS as part of our commitment to delivering full-spectrum coverage in a single platform.
Public cloud environments don’t operate in isolation - they rely on a sprawling ecosystem of SaaS services across identity, code, and data. Your cloud infrastructure is continuously talking to external platforms as part of a chain of interdependent operations. And if your cloud security strategy isn’t listening to those conversations, you’re missing a major part of the story.
Today, we’re excited to roll out our SaaS-sourced threat detections, built to give SecOps teams complete visibility across the services powering their cloud. Stream’s SaaS detections extend our end-to-end visibility beyond all cloud layers to include SaaS as part of our commitment to delivering full-spectrum coverage in a single platform.
Let’s be real: attackers intentionally exploit where the boundaries between your SaaS apps and your cloud start and end.
They exploit credentials to access infrastructure, use compromised accounts to escalate permissions, or pull sensitive data via legitimate-looking queries. Without visibility into the SaaS layer, your cloud detections are working with blind spots by default. You need to understand how they connect, because that’s where real risk unfolds.
Say goodbye to those blind spots with Stream.Security’s new SaaS detection sources. 👋
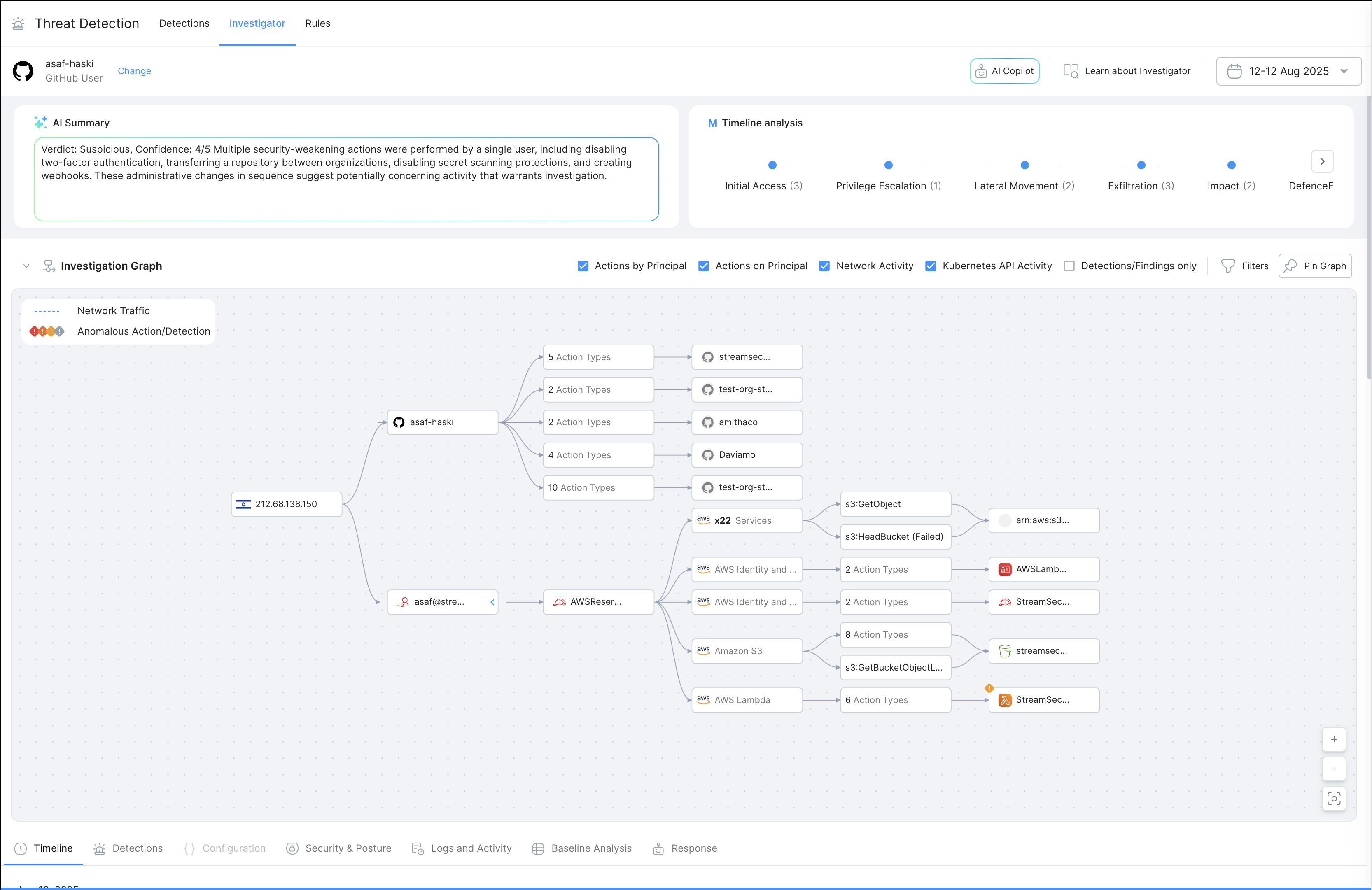
Stream applies the same detection-first approach we use in the cloud to SaaS platforms, enabling real-time threat detections across version control systems, identity providers (IdP), and cloud-connected databases. Our detection engine uses fingerprinting to build behavioral baselines for entities to spot anomalies like odd login times, access patterns, or unexpected geolocations. It comes with prebuilt detection rules, lets you create your own, and enriches signals with threat intelligence - then ties it all together with an AI Copilot that prioritizes related activity across SaaS and cloud.
Identity is the entry point for most cloud attacks, and your IdP is often the first place signs of compromise appear. Our integration with Okta ingests System Logs (available to Enterprise Plan customers) to provide deep visibility into identity-related activity, including:
IdP visibility helps detect threats like unauthorized login attempts, unusual geo locations, abnormal operations, sudden access grants, or abuse of admin privileges that are suggestive of malicious behavior.
On top of exisitng Azure Entra AD and Google Workspaces.
Version control platforms are tightly coupled with infrastructure deployment, making them critical for both productivity and security. Stream integrates with GitHub and GitLab to provide real-time visibility into developer activity, CI/CD pipelines, and potential abuse across the software supply chain.
Our integration ingests and analyzes audit log data to detect:
Each action is enriched with downstream cloud activity, so you don’t just know what happened in GitHub or GitLab, you know what it impacted. Built for DevSecOps teams, these integrations enrich activity with cloud context to surface threats (like code tampering or runner abuse) across the software supply chain that could impact production environments.
Your cloud doesn’t just store data, it moves it. And for many teams, Snowflake is where that data ends up. Stream ingests data from Snowflake and reconstructs audit logs that can be used for detection and response.
Stream takes these key audit events, detects anomalous behavior in real time, enriches that data with threat intelligence, and then correlates it with upstream cloud activity.
Our integration lets you monitor:
The result? You see not just that data moved, but who, how, and why it moved. That way, teams can determine if activity is expected or malicious.
Your CRM doesn’t just store deals. It store critical PII data and at times might store information which will allow lateral movement to the cloud. Stream ingests data from Salesforce and reconstructs audit logs that can be used for detection and response.
Stream takes these key audit events, detects anomalous behavior in real time, enriches that data with threat intelligence, and then correlates it with upstream cloud activity.
Our integration lets you monitor:
Unlike traditional connectors or webhook-based setups, Stream’s SaaS detections are deeply embedded into our attack path correlation engine. That means:
So whether a GitHub user pushes suspicious infra changes or a Snowflake account suddenly spikes access, you see the why, how, and what’s next in one place.
By integrating your critical SaaS tools into Stream.Security, you:
Our SaaS detections are live and ready to help you close the loop between cloud workloads and the SaaS services they depend on.
Request a demo to see how Stream.Security helps you stay ahead of multi-platform threats with unified cloud + SaaS visibility.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
