
Enhance Data Security: Monitor Access, Implement Cloud Policies, and Receive Real-Time Alerts on Deviations and Threats.
The modern cloud stack creates new security challenges around data at rest and in use.
Stream Security's seamless integration with AWS Macie redefines how businesses protect their most critical assets. Together, we offer a robust solution that empowers you to monitor who has access to your sensitive data, who actually use the access, implement comprehensive Data Access Policies, and receive instant alerts on any deviations and threats - all in real-time.
AWS Macie offers an advanced service designed to discover and classify sensitive information across your AWS environment. By leveraging machine learning and pattern matching, Macie identifies your most sensitive data at scale, ensuring that your privacy and security protocols are never compromised. Read more here.
Stream Security enhances this protection by integrating natively not only with AWS Macie but also with other leading sensitive data scanners, as well as allows manual asset tagging. This integration allows for the automatic designation of assets containing sensitive data as "Crown Jewels." This distinction makes it significantly easier for our mutual customers to oversee both Human and Non-Human access permissions to these pivotal assets, alerting on deviations from data access policies, including tracking actual activity in a transparent and efficient manner.
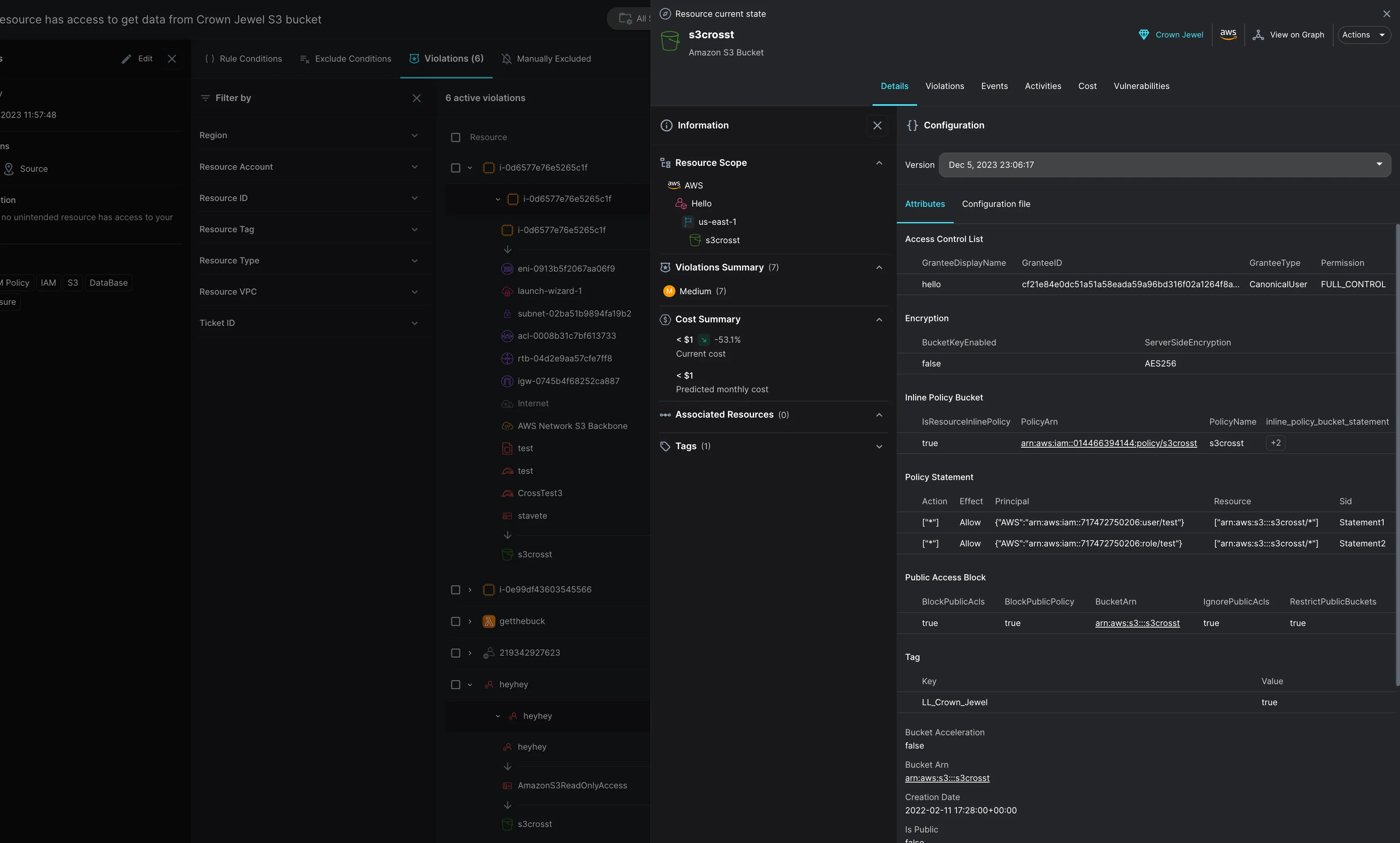
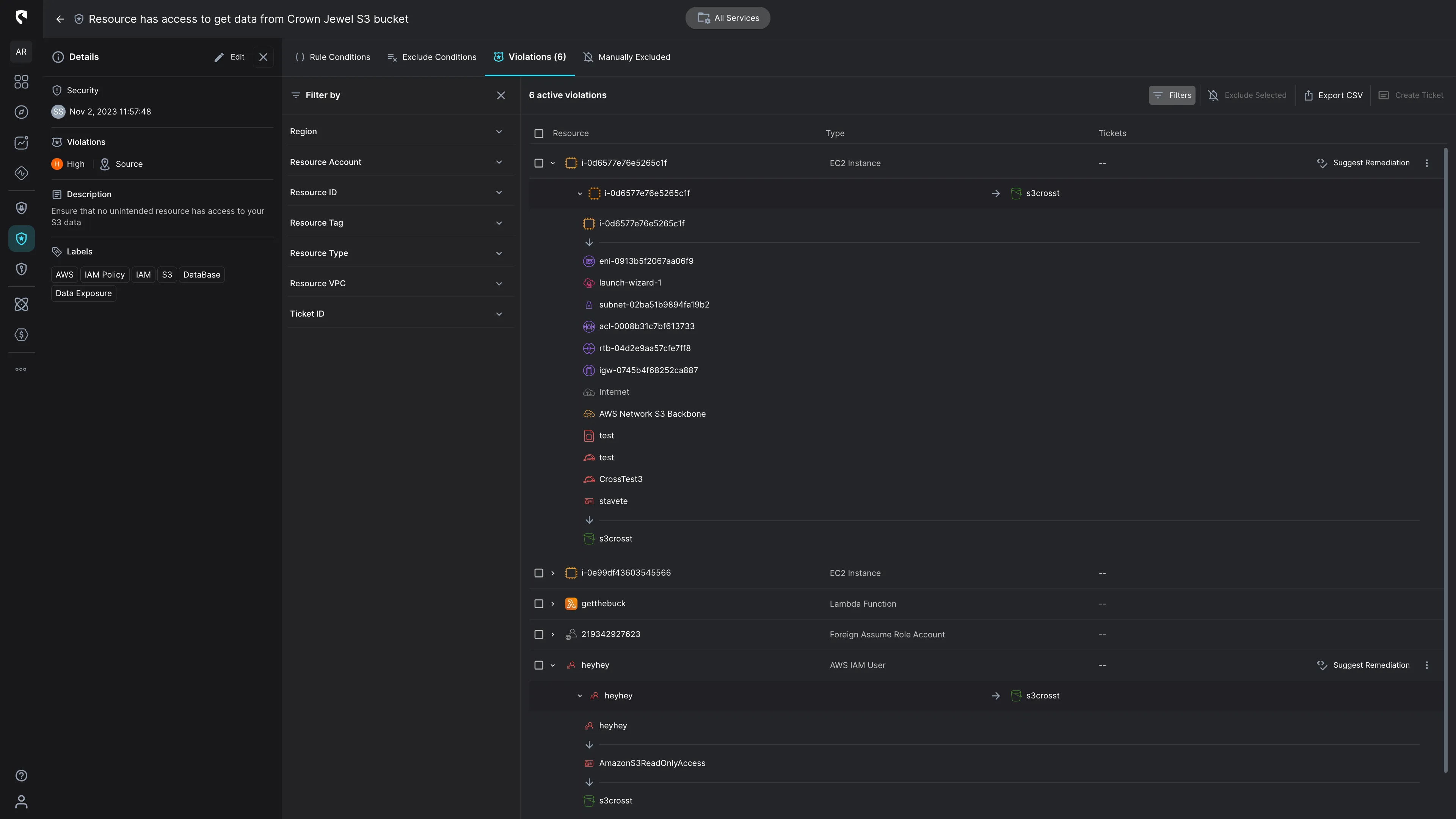
Easily declare Data Access Governance and define your organizational best-practices to reduce attack radius and meet compliance.
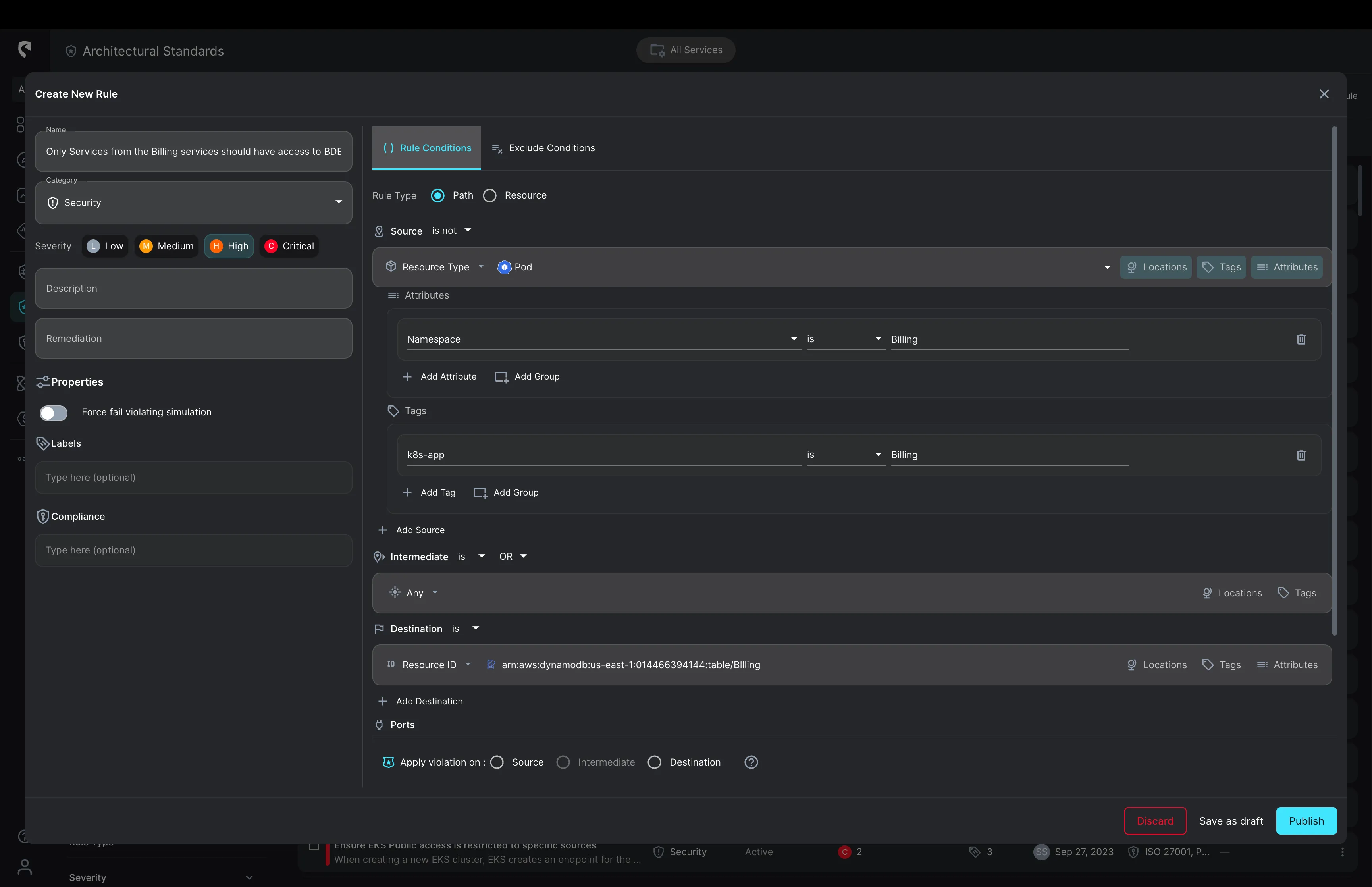
One of the most critical aspects of data security is the ability to respond swiftly to potential threats. With Stream Security, you can define Data Access Policies that are both dynamic and robust. Any deviation from these policies, whether at Runtime or during (CI) with Terraform, is immediately detected. This instant detection mechanism ensures that any unauthorized access or unexpected changes trigger alerts, allowing your InfoSec and DevOps to take immediate action and prioritize their actions based on the assessed risk associated with each entity with new access.
In addition to identifying who has access to sensitive assets, we monitor actual transactions. This enables your team to observe who actually utilizes the granted access. Our ML-based threat detection engine alerts on abnormal and malicious activities.
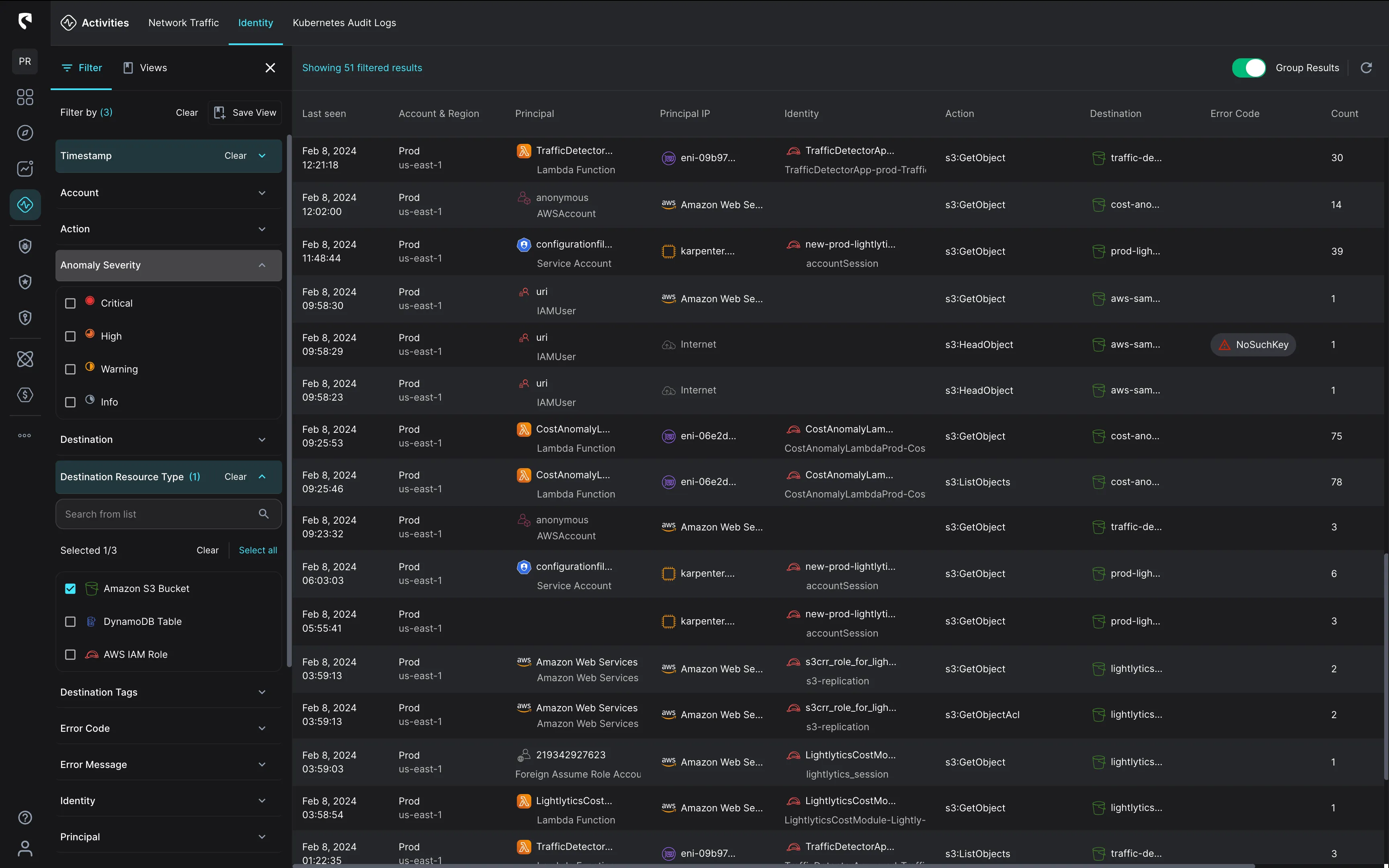
The collaboration between Stream Security and AWS Macie signifies a leap forward in data protection technology. Our mutual customers benefit from an integrated solution that not only identifies and classifies sensitive data but also monitors access and activity in real-time. By setting clear Data Access Policies and receiving immediate alerts on deviations, businesses can ensure that their data remains secure, compliant, and under control.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.
