
.png)
For large-scale cloud environments, the math is simple. When detections depend on stale data, triage is manual, and investigations are fragmented, even the best teams fall behind. Stream’s platform gives SecOps teams complete cloud visibility in real-time, with built-in automations and AI tooling that make investigations easy.
Security Operations Centers (SOCs) are under relentless pressure. Analysts tasked with triage spend most of their time battling noise rather than neutralizing threats. Traditional tools like SIEMs, SOARs, even UEBA were not built for the dynamic, high-scale nature of cloud environments. Instead of helping, they often create new bottlenecks: excessive false positives, fragmented toolchains, unrealistic expectations for junior staff.
SecOps teams don’t need more dashboards, alerts, or manual work. They need detections enriched with the context of the entire environment, and triage that doesn’t drain analysts, but empowers them. This is what lies at the core of Stream’s mission: enabling SecOps teams to detect and respond to threats in the cloud as part of a unified security workflow.
Traditional detections rely on rules and anomalies built on log data. In the mid-2010s, UEBA added baselining of users and entities, but the approach still left critical blind spots:
In the cloud, post-detection triage is a broken model. Why? Because by the time you're investigating, the environment may have already changed. Using SOAR or AI SOC tools to retrieve context from static scanners may lead to missed or misleading conclusions, especially if the last scan was 24 hours ago. In that time, a resource could have been created, exploited, and deleted, leaving no evidence for enrichment tools to analyze.
The missing piece in the puzzle is configuration awareness at detection time to ensure alert accuracy, context, and prioritization.
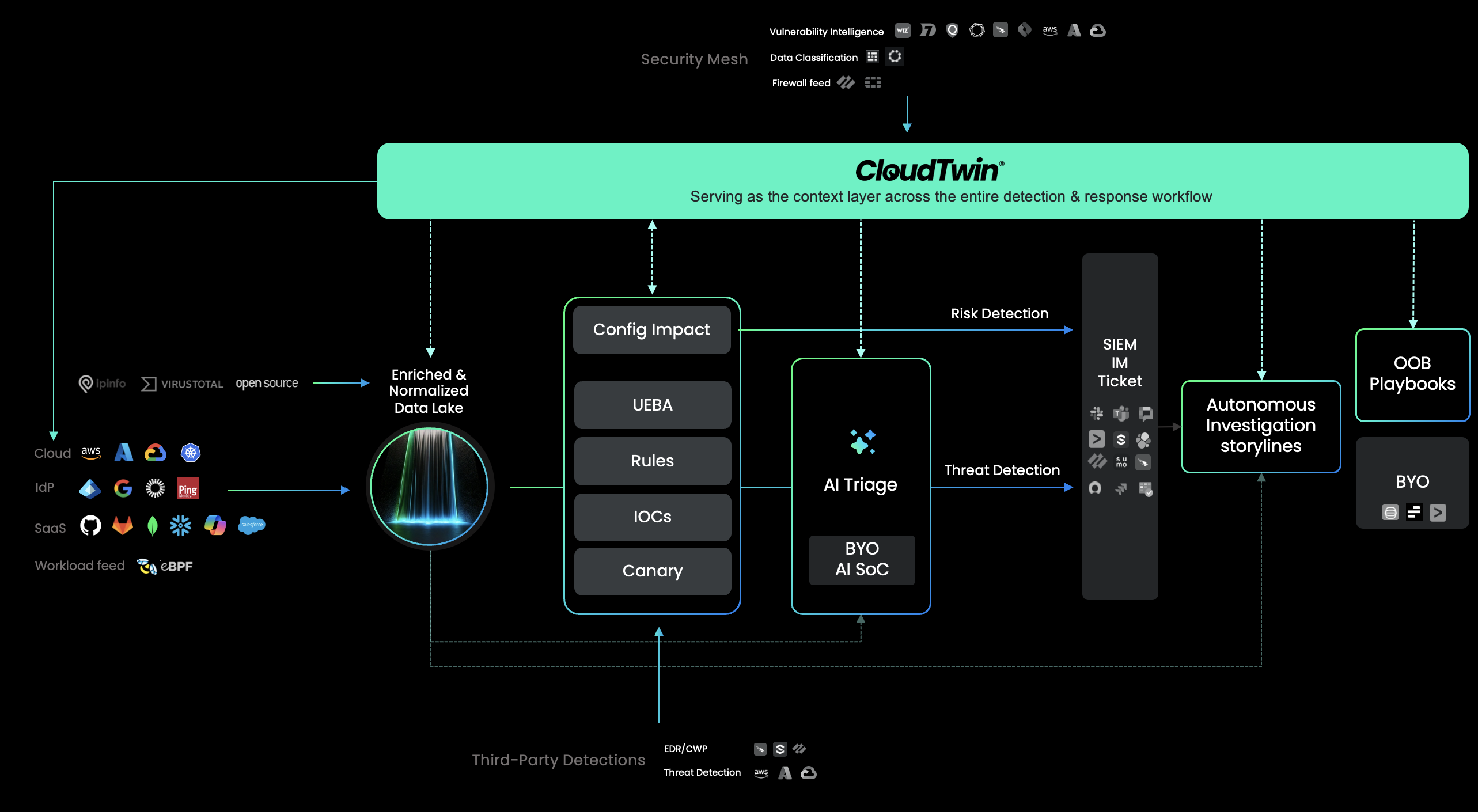
Stream’s CDR platform is run by our proprietary CloudTwin™ model that fuses runtime, identity, network, SaaS, and configuration data into a real-time fabric. This creates a single, continuous, correlated source of truth that powers multiple complementary detection engines that run in Stream’s CDR platform:
Stream’s platform then uses AI triage and automated storylines to automatically enrich, score, and correlate these high-fidelity detections into incident-level narratives instead of isolated log events. This makes incident investigation comprehensive, accessible, and actionable. Let’s take a look at how Stream helps SecOps analysts investigate incidents:
To understand more about Stream’s revolutionary cloud detection engine, let’s revisit a known CloudGoat scenario: AWS Lambda PrivEsc.
The Attack Path:
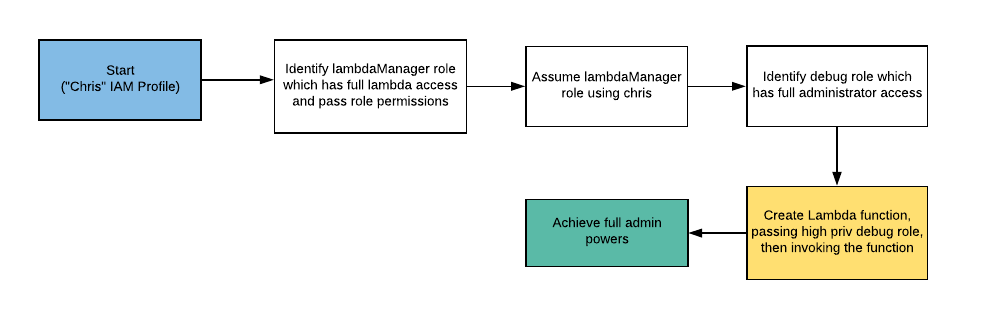
Let’s see how Stream handles the scenario:
A Config change detection alert is triggered for the IAM User getting admin privileges. (A SIEM would likely only show a new policy “AppPermissions” attached to a user, rather than as a detection that’s part of an attack storyline.)
Stream automatically logs and categorizes the ARN (Amazon Resource Name) executing the change, noting an assumed role: arn:aws:sts::014466394144:assumed-role/cg-debug-role-cgid4kbkn55zns/admin_function_v2. Stream shows this Lambda function under “Principal”
Upon first glance, this looks like a legitimate automation workflow, but Stream reveals more.
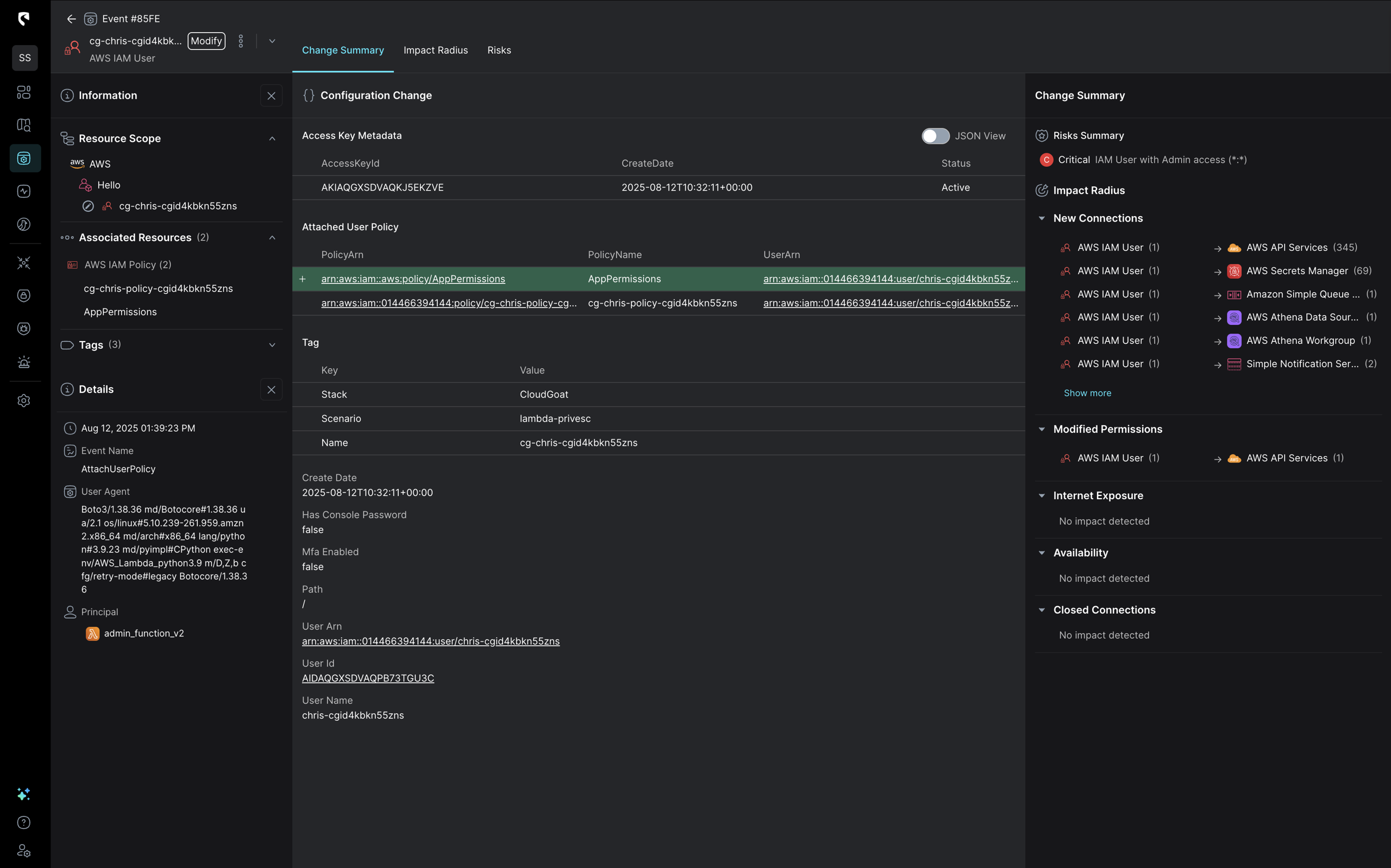
Insights into configuration changes show a more complicated story. While the role changes were detected, an alert was simultaneously trigged when the Lambda executed configuration changes. Stream’s detection engine alerts on any change carried out by compute resources, and records that the Lambda caused the alert by executing “AttachUserPolicy.”
Immediately, Stream’s CoPilot tags the event as malicious, summarizing it as a “privilege escalation attack where the Lambda function was created and then immediately used to modify IAM permissions.”
With insights into attack progression across all cloud layers, the data that Stream’s AI Copilot has access to is much more robust, making summaries accurate and actionable.
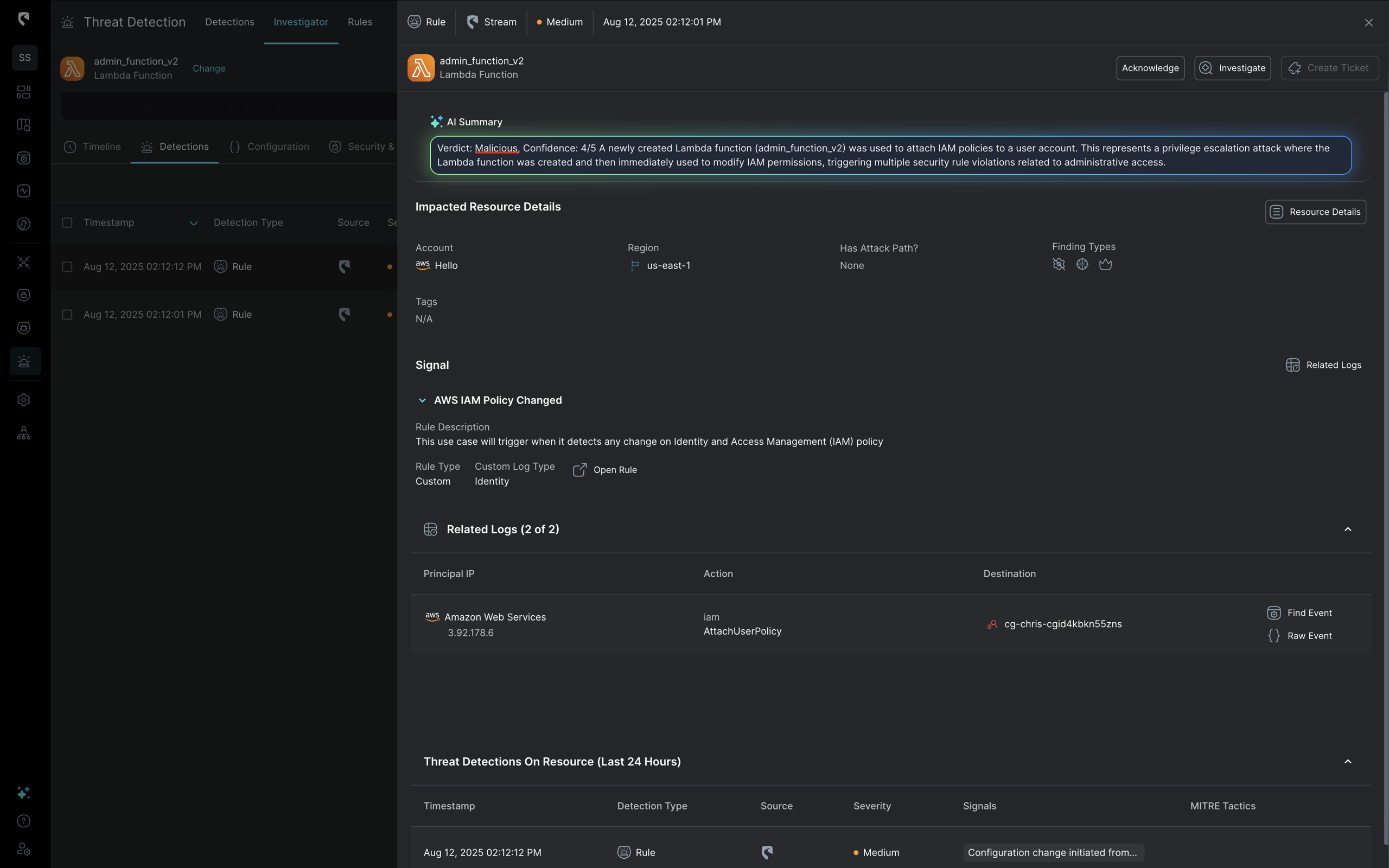
3. Stream’s Automated Storylines Make Investigation Easy
The attack entry point is automatically mapped by Stream’s Investigator, displaying the IAM principal that created the Lambda. That principal is the one targeted by the AttachPolicy.
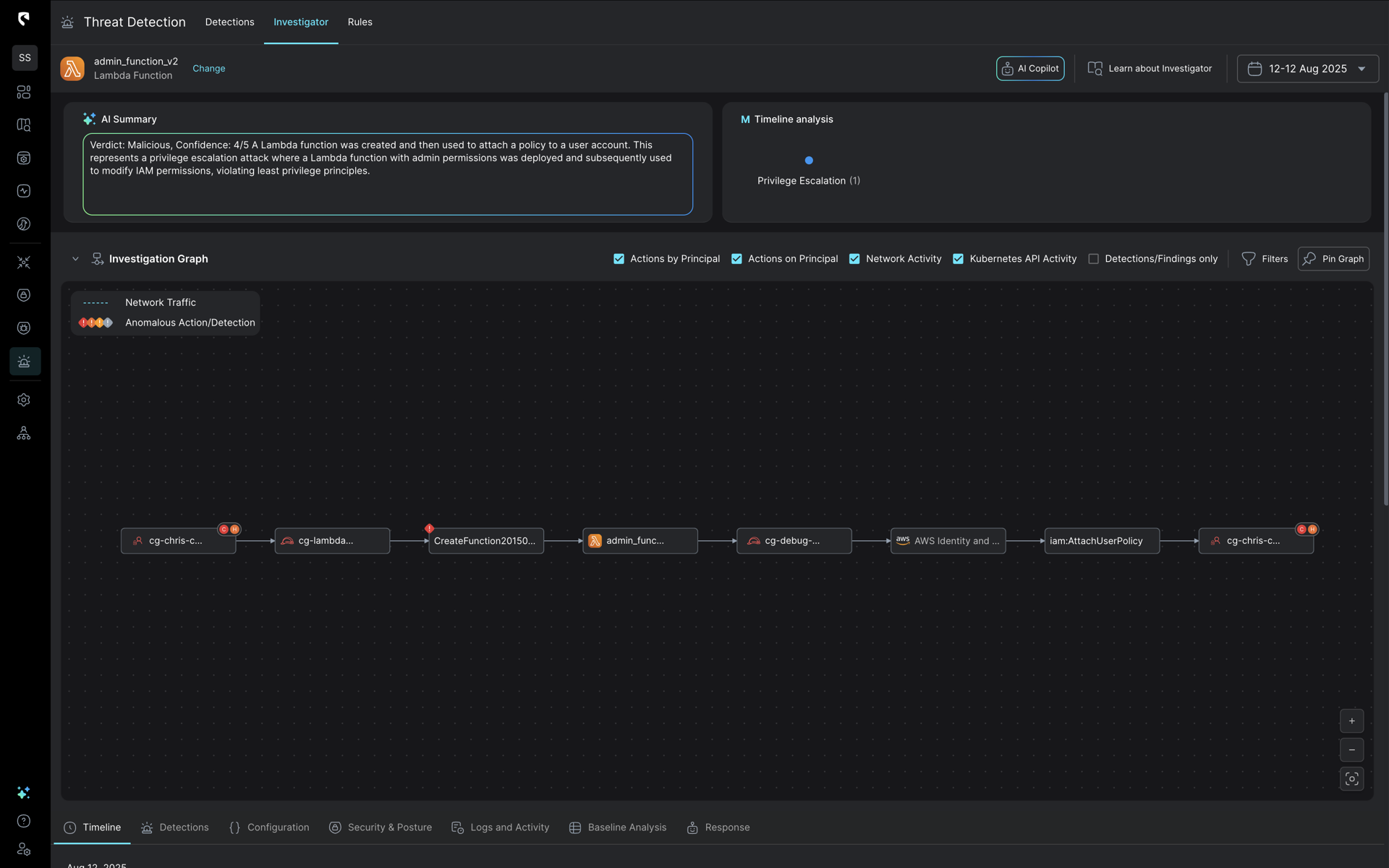
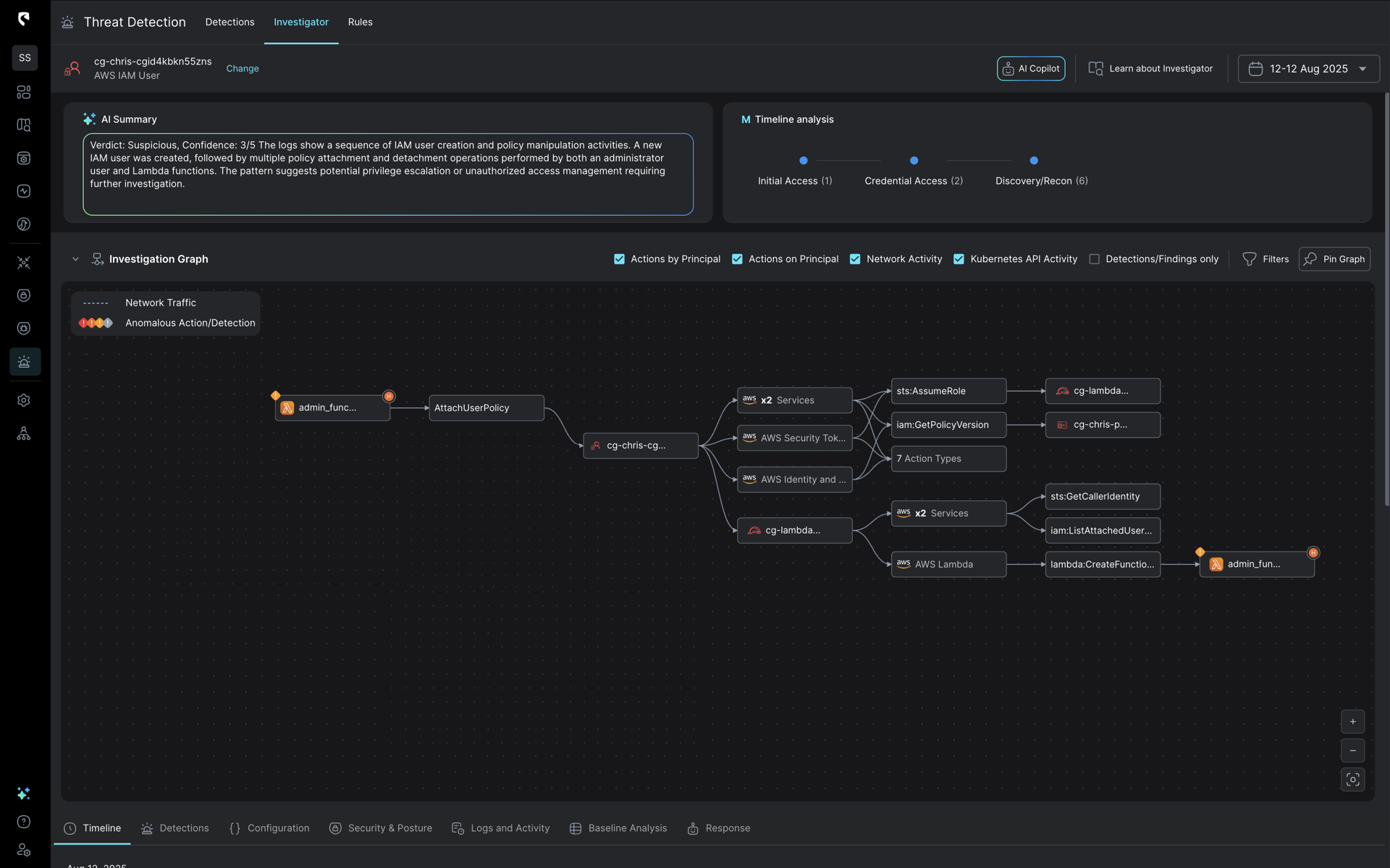
A deeper look into the IAM user activity in Stream’s platform shows who created the Lambda function and executed the privilege escalation. Stream’s Investigator traces the entire sequence of events, including initial discovery and reconnaissance activities, the role assumption steps used to create the Lambda, and the subsequent execution of the escalation.
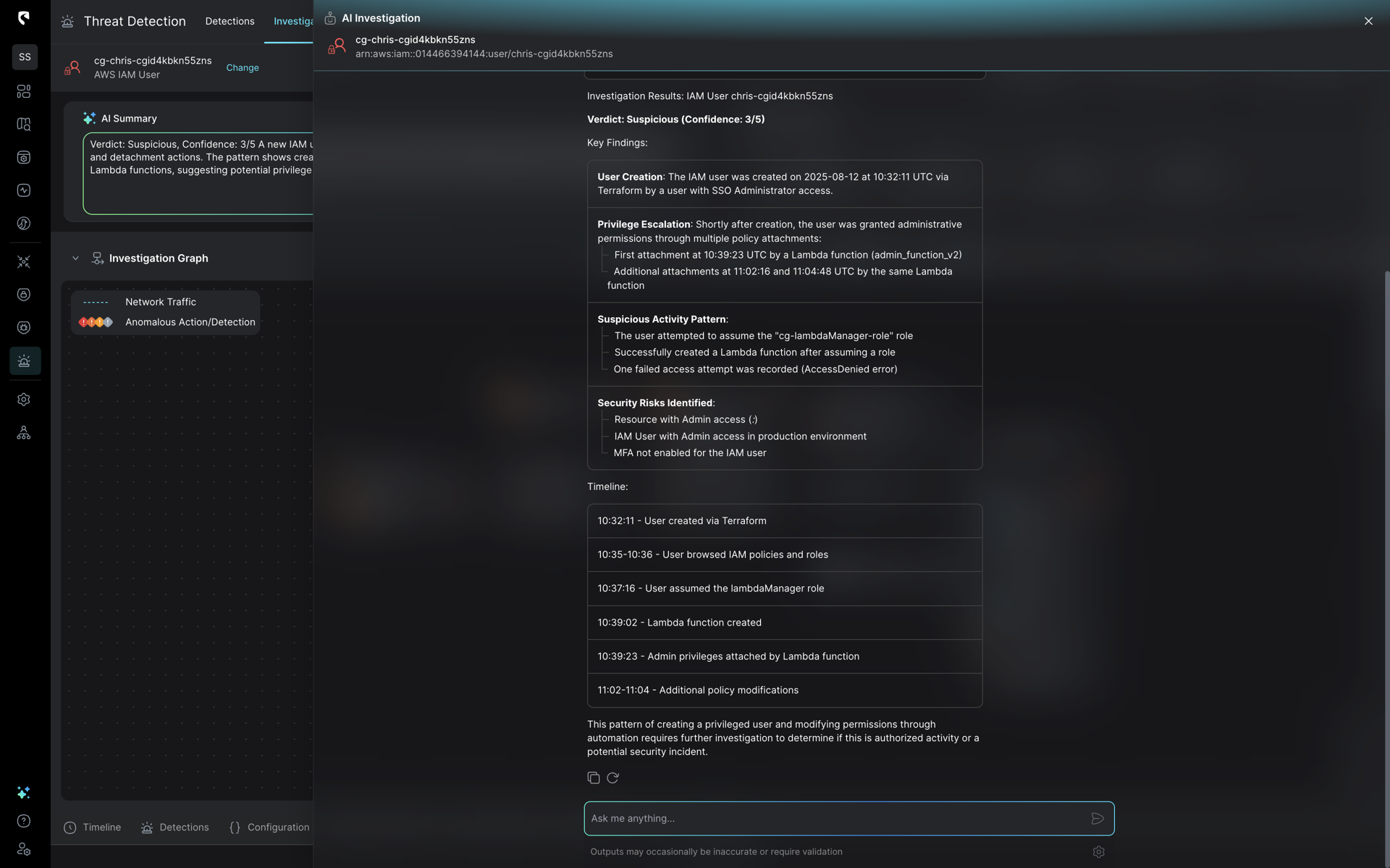
Stream’s AI Investigation CoPilot easily lays out the entire chain of events, which makes incident investigation much more streamlined for analysts.
For large-scale cloud environments, the math is simple. When detections depend on stale data, triage is manual, and investigations are fragmented, even the best teams fall behind. Stream’s platform gives SecOps teams complete cloud visibility in real-time, with built-in automations and AI tooling that make investigations easy:
The result is a SOC that scales with your cloud to become faster, smarter, and more resilient. Instead of more noise, you get clarity.
This is what modern cloud detection and response should look like - and it’s exactly what Stream delivers.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.

.png)


