

Stream.Security just launched a new AI Triage feature to assist analysts in addressing the growing volume of alerts in the cloud and SaaS. The AI Triage agent brings human-like intelligence and decision making to SOC analysts. With Stream’s real-time CloudTwin model, the triage digests updated risk-based data that factors in asset criticality, exposure, and blast radius to prioritize alerts that truly matter.
Security teams today face a fundamental imbalance: alerts are endless, but analyst time is finite. Every investigation eats away at valuable cycle time, leaving analysts focused on handling false positives or low-value noise rather than real threats.
The result? Burnout, backlogs, and missed true threats. And without live, enriched data behind alert decisions, triage becomes a guessing game rather than a reliable process.
A detection fires → an alert is generated → it lands in an analyst’s queue.
Hours later, the analyst investigates, only to discover most are benign.
This manual, reactive model collapses in the cloud era, where ephemeral workloads, role chaining, and SaaS APIs produce thousands of signals every day.
Even in organizations where alerts are enriched automatically, the AI workflow is limited. Traditional automations today do not extend into the decision-making phase, meaning that bottlenecks and resource limitations are never truly resolved.
Teams are forced to choose: scale back coverage or drown in investigations.
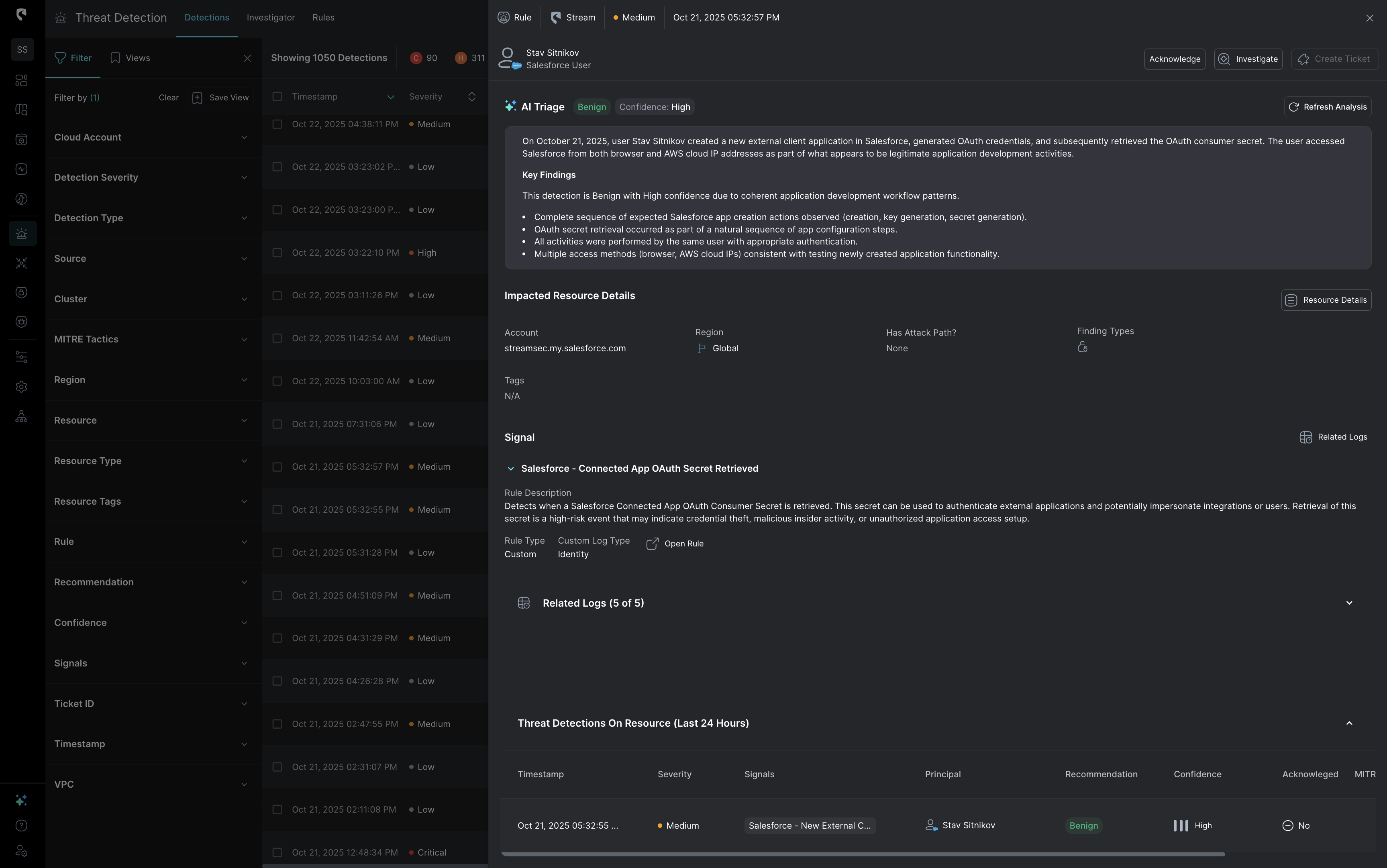
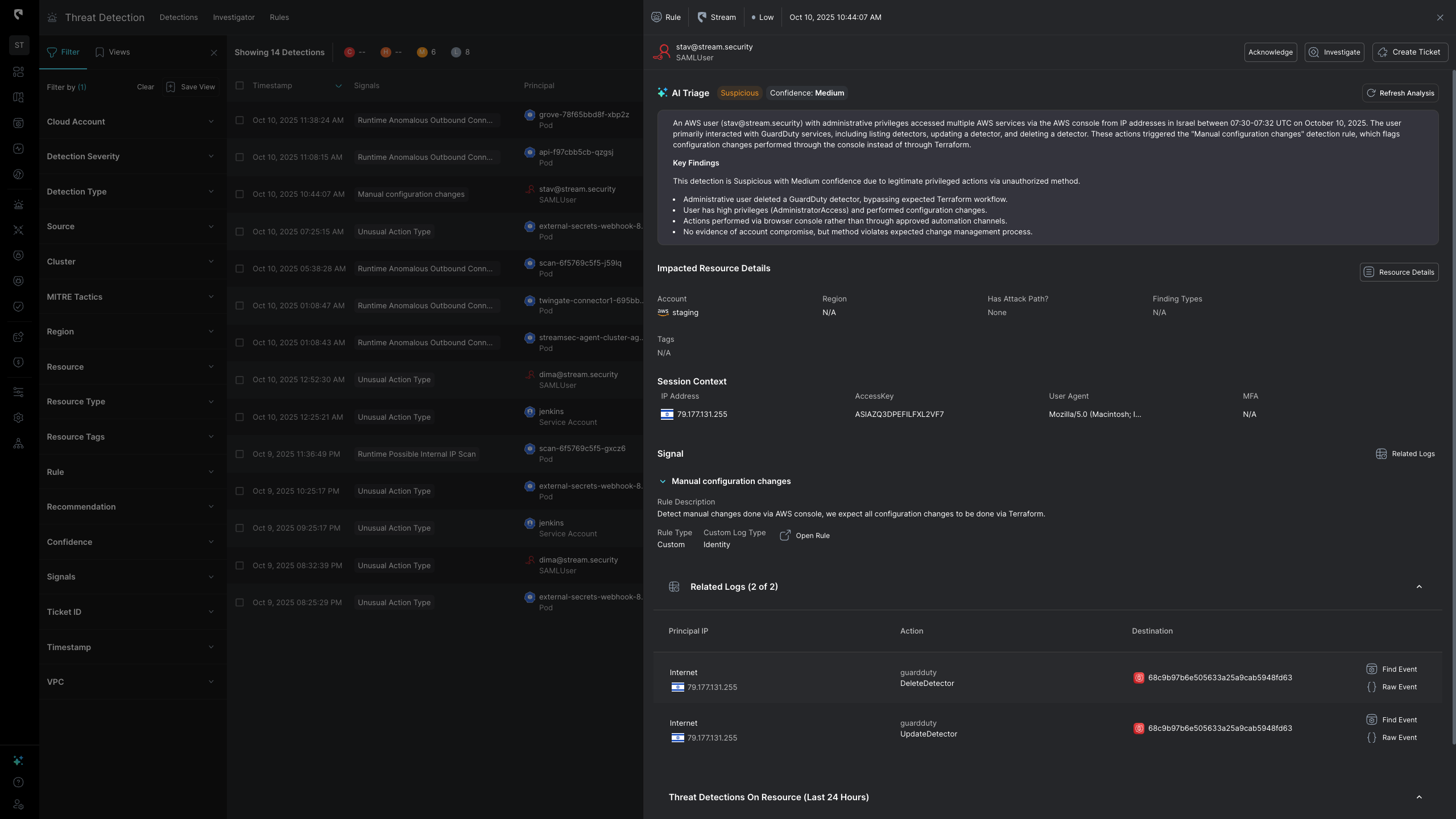
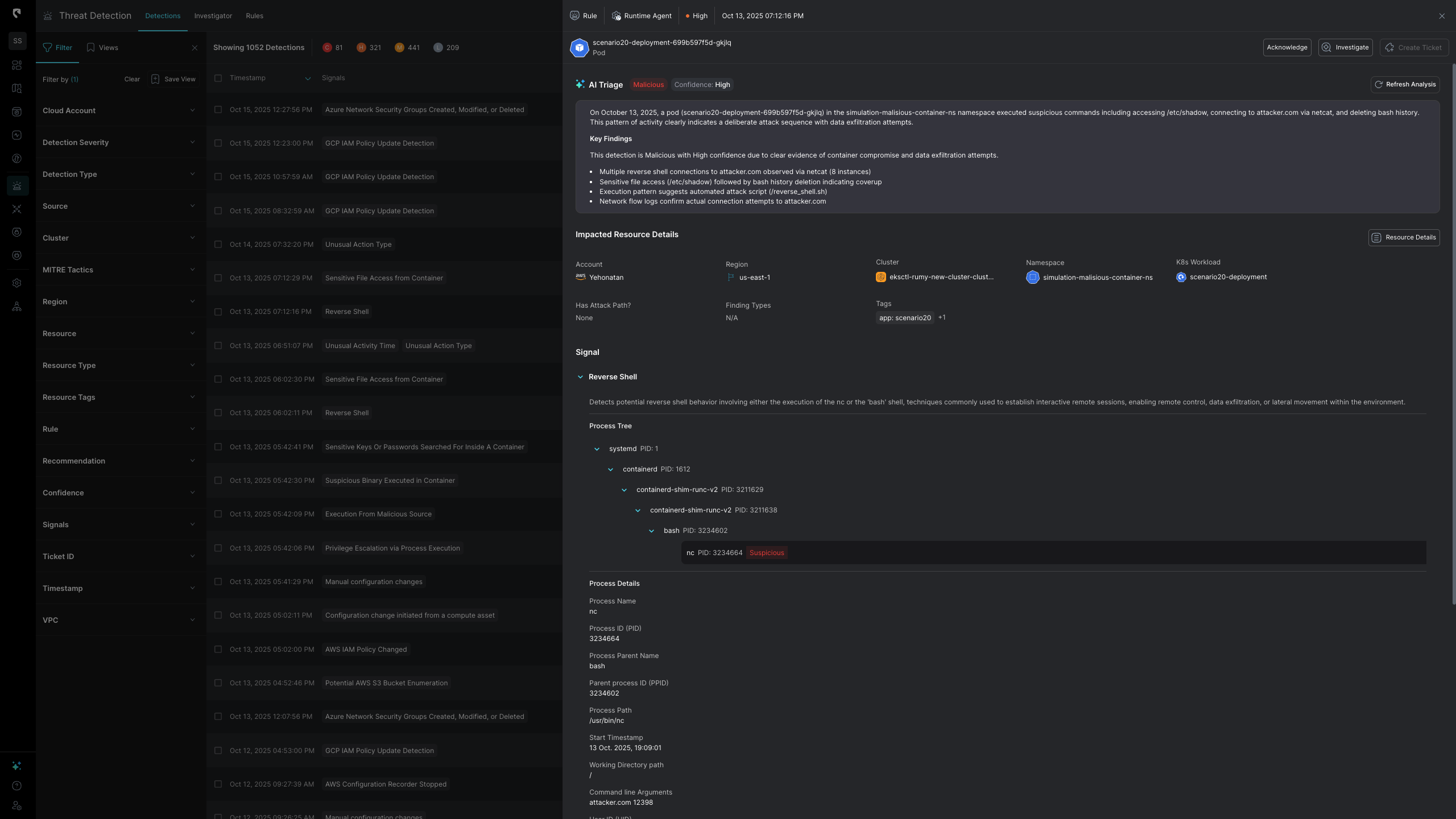
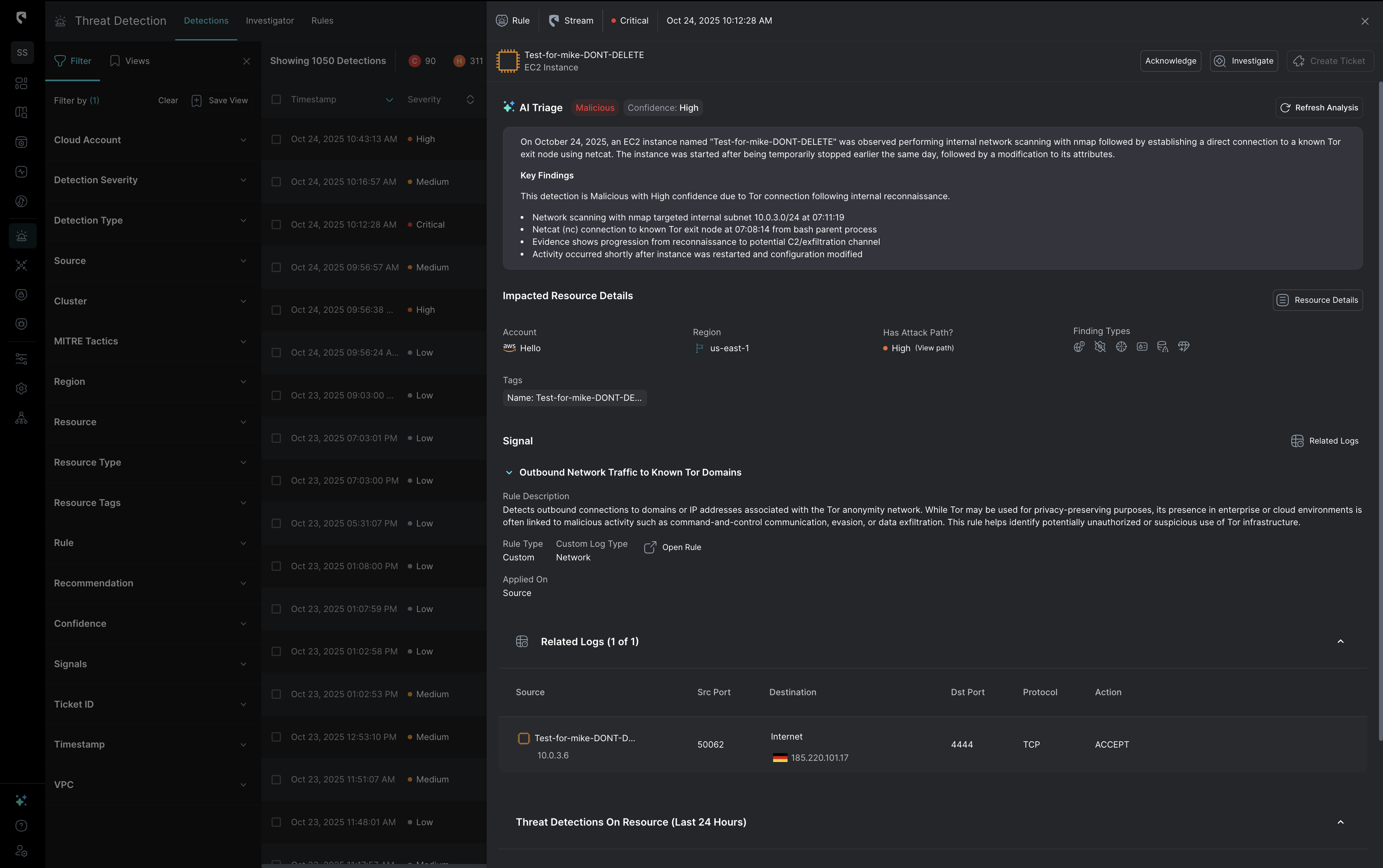
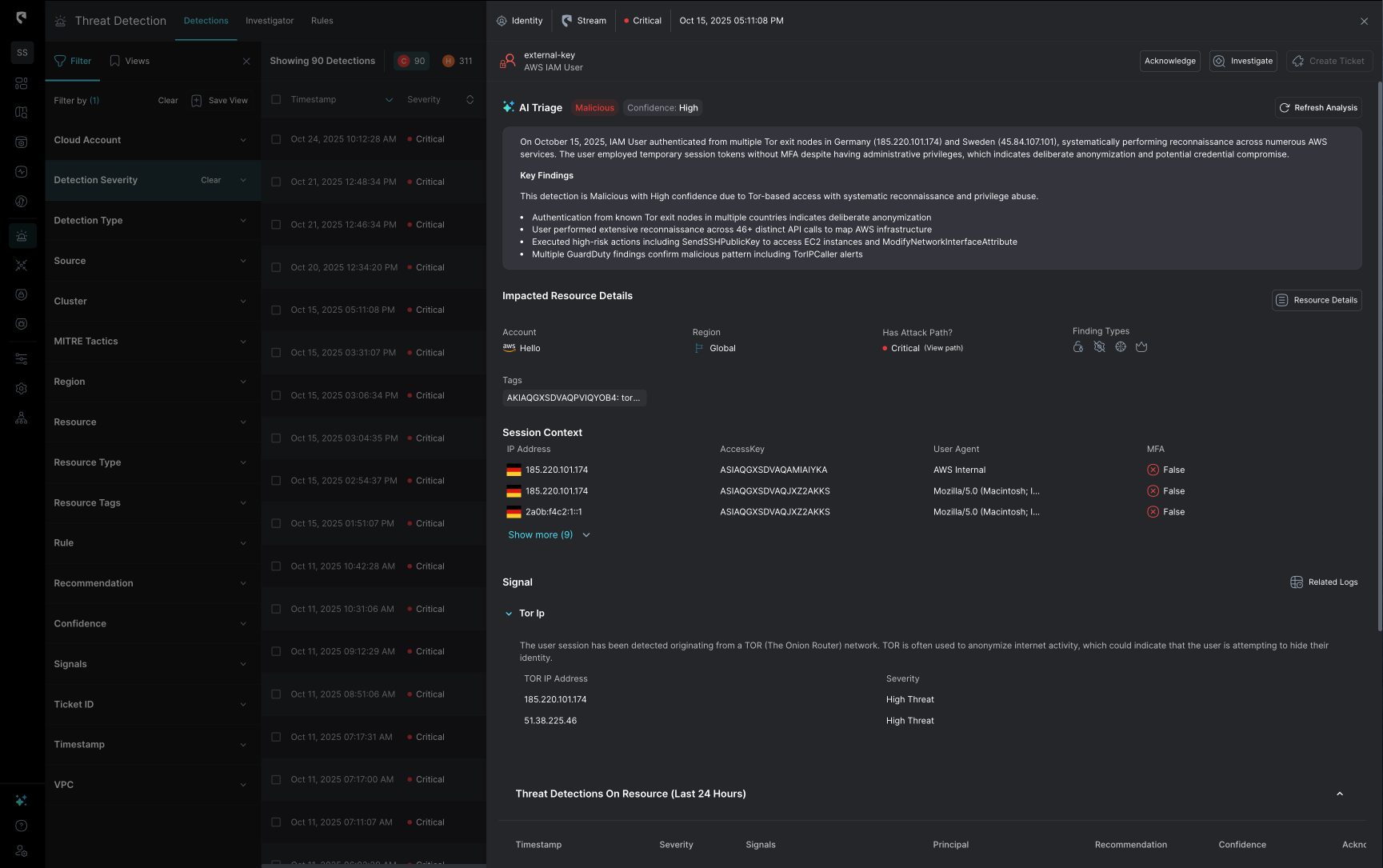
At Stream, we’ve introduced fully Automated AI Triage: a capability that doesn’t just summarize alerts but makes a final decision using real-time cloud state, complete reasoning, and full context from the environment. When the AI Triage tool determines that an alert is benign with high certainty, it automatically closes it, so your analysts never even see it. For customers already using AI Triage within Stream, false positives and alert noise has reduced dramatically.
Nothing slips through the cracks.
Unlike most AI SOC tools that rely on stateless SIEM logs or outdated CSPM snapshots, Stream takes a fundamentally different approach. Our AI-driven triage is powered by the CloudTwin™, a real-time digital twin of your entire cloud and SaaS environment.
This means your AI agent isn't guessing with partial or outdated data. It's working from a live, stateful, and accurate view of reality.
Stateful data gives AI models the best ability to triage detections accurately, working as the foundation that makes confident, automated decisions possible.
Stream was recognized in a recent Gartner® SOC Innovation Report on AI SOC tools that reinforced a critical truth: an AI agent is only as effective as the data it’s built on. And Stream takes this emphasis on data even further.
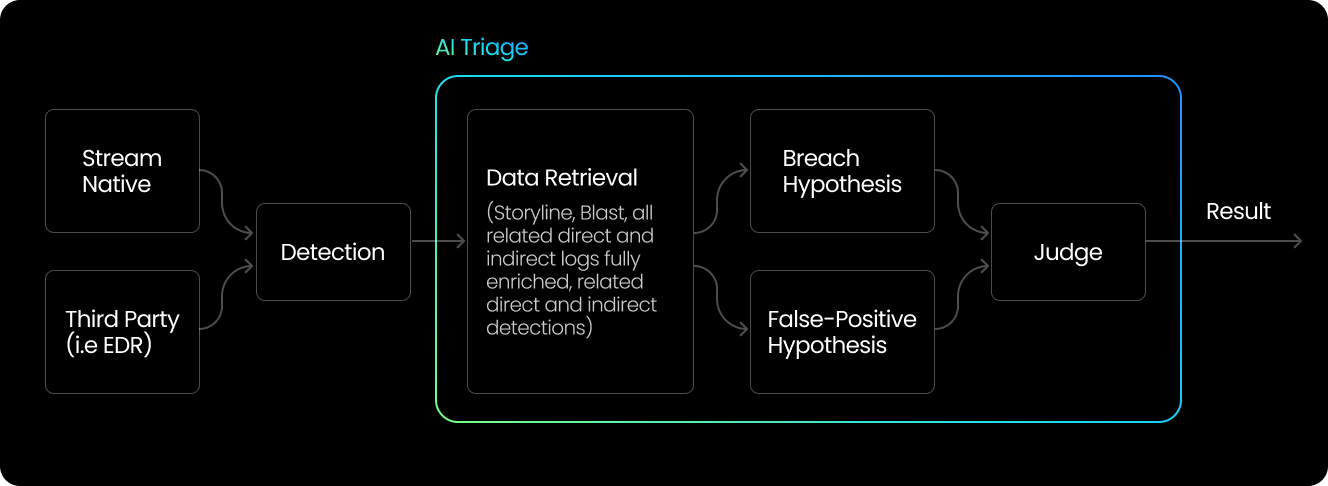
Each alert processed in Stream’s AI Triage engine goes through two distinct AI passes:
This two-pass approach replicates how experienced analysts actually think, creating balance that keeps the AI Triage agent unbiased. An AI agent biased toward marking alerts as benign will save time, but miss real threats. On the other hand, an AI agent biased toward flagging everything as suspicious will overwhelm your SOC with false positives. Therefore, Stream’s AI Triage agent works on a balance between both approaches.
Both hypotheses are then compared, and the system measures the deviation, which is a confidence gap between “breach likely” and “benign likely.” That deviation score determines whether the AI auto-closes the alert or escalates it for analyst review.
By forcing the system to argue both sides before deciding, we mimic the internal debate a senior analyst conducts instinctively.
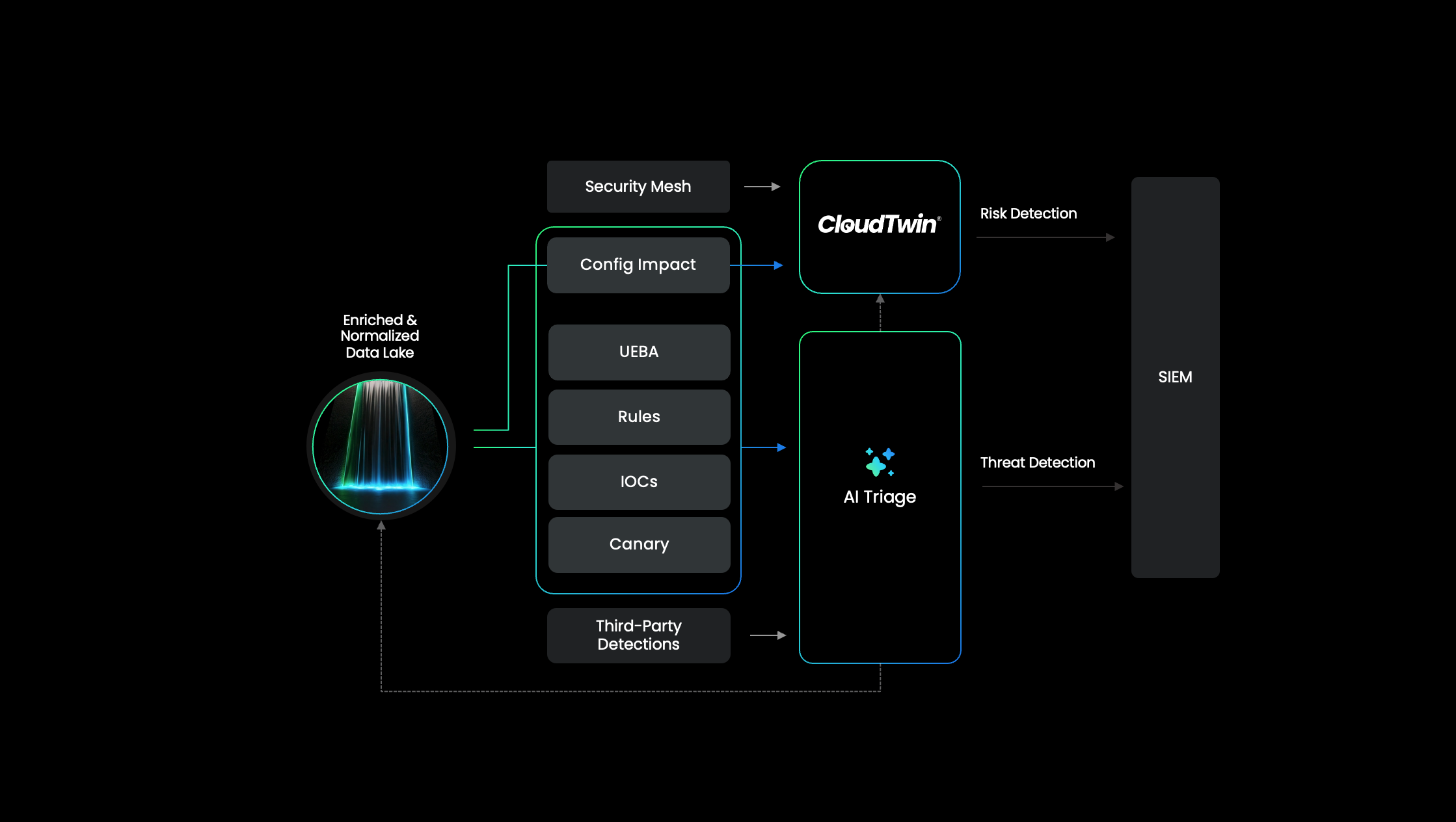
Stream's AI Triage agent cross-correlates CloudTwin context with all direct and indirect detections, linking signals across explotialiby possibility, blast radius, identities, workloads, and exposures to see the bigger picture. It understands relationships between API calls, configuration changes, and runtime behavior, giving it the same multi-angle reasoning a senior analyst would apply.
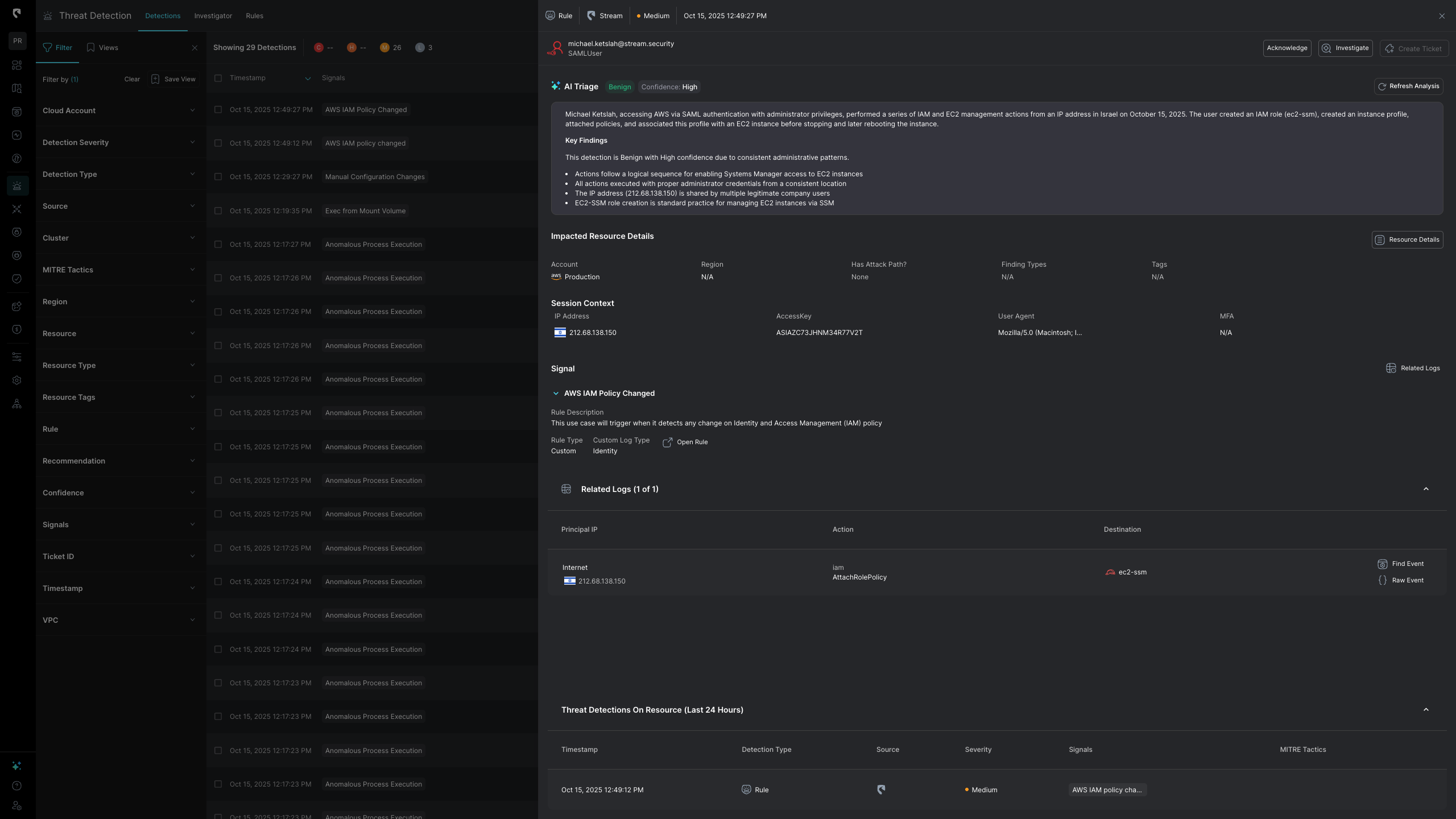
With automated triage, SOCs can see measurable improvements:
AI has been creeping into security operations for years, but most vendors stop at summarization capabilities.
At Stream.Security, we go further: AI with reasoning, not just reaction. By running dual-pass evaluations, cross-correlating CloudTwin with detections, and confidently closing benign signals, Stream gives SOCs both precision and coverage at scale. Stream’s AI Triage engine was created with the goal of elevating and empowering security analysts, so they get time back to hunt, innovate, and strengthen defenses.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.

.png)


