

For years, SIEMs have been positioned as the “source of truth” for security operations. They ingest everything, correlate endlessly, and alert loudly.
And yet, they consistently miss the most critical signal in modern cloud attacks: configuration change impact.
This blog walks through how Stream.Security closes the gaps and turns config changes into impact-aware detections.
For years, SIEMs have been positioned as the “source of truth” for security operations. They ingest everything, correlate endlessly, and alert loudly.
And yet, they consistently miss the most critical signal in modern cloud attacks: configuration change impact.
SIEM architectures fundamentally lack the ability to reason about configuration change impact, leaving the most dangerous cloud risk invisible until it’s too late.
SIEMs were built in an era where infrastructure was static, identities were long-lived, and attacks unfolded slowly.
Cloud environments broke all of that.
Today:
SIEMs still ingest logs like:
But these logs say nothing on their own.
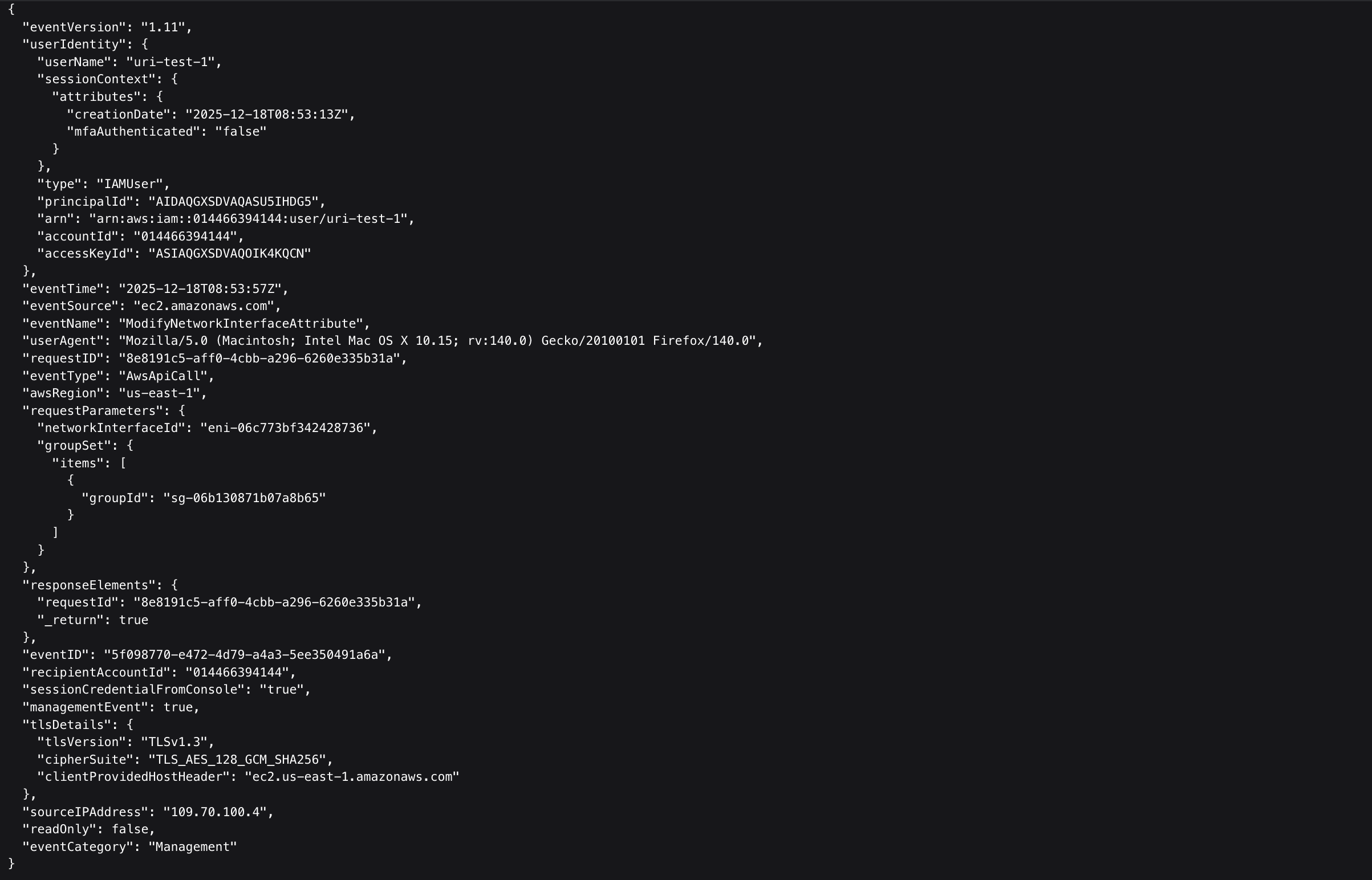
SIEM logs won’t tell you:
The logs capture isolated actions, not how those actions combine to form an exploitable attack path.
A log records that something happened. It does not explain why it matters.
In cloud breaches, attackers don’t “break in” the traditional way. In fact, they manipulate the complexity of cloud layers to enable their attacks. That means that classic detection tools won’t always flag these breach attempts as malicious.
They:
Most real-world cloud attacks begin and succeed through configuration changes.
Yet SIEMs treat configuration events as:
By the time alerts fire, the damage is already done.
SIEMs fail configuration-based detection for three core reasons:
SIEMs analyze logs after ingestion, normalization, and correlation.
But risk emerges at the moment of configuration change, not minutes later when data is exfiltrated.
A SIEM sees: “Policy updated”
It does not know:
State awareness is what turns change into meaning. An accurate, real-time view of cloud state (and how that state evolves) allows security teams to determine what impact that change made in the environment. Visibility into that “butterfly effect” of configuration changes reflects how those changes increase risk, introduce exposure, or quietly enable attacks.
Without state awareness, there is no real detection, only speculation.
Cloud attacks rely on:
Traditional correlation rules cannot model this dynamically.
As a result, SOC teams are left to manually piece together meaning from raw events, which takes away from response time, exactly when speed matters most. By the time a human can connect the dots, the attacker already has.
Modern detection and response must:
With Stream.Security, configuration changes are evaluated against live cloud state to determine actual risk.
Stream’s CloudTwin maintains a live, stateful model of your cloud and SaaS environment, continuously mapping real identity relationships, effective permissions, network reachability, and service behavior as they change. Instead of correlating isolated logs like a SIEM, the CloudTwin evaluates each configuration change against current state to determine actual exposure, exploitability, and blast radius in real time to turn raw activity into clear impact that enables fast, confident response grounded in how your cloud truly operates.
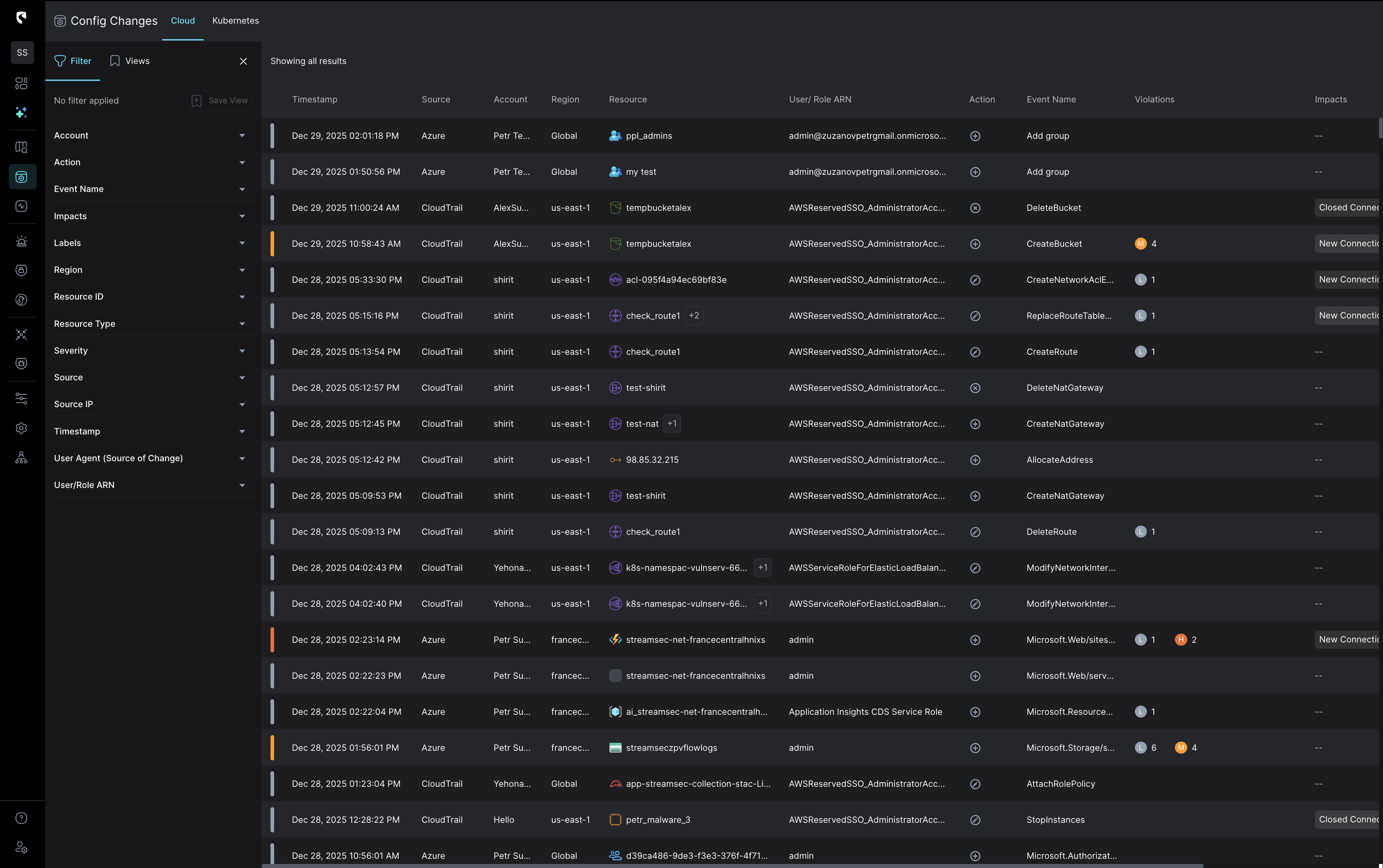
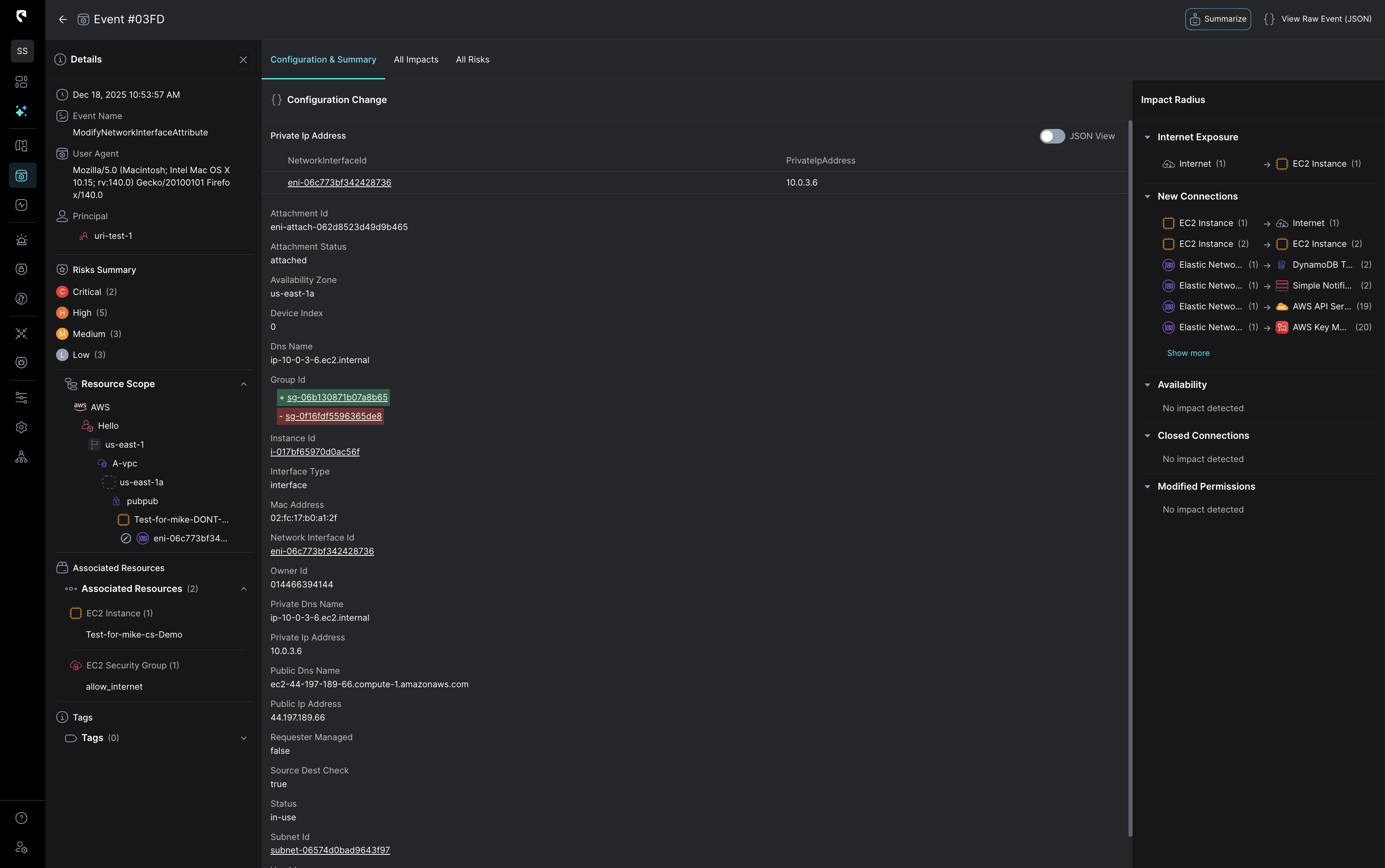
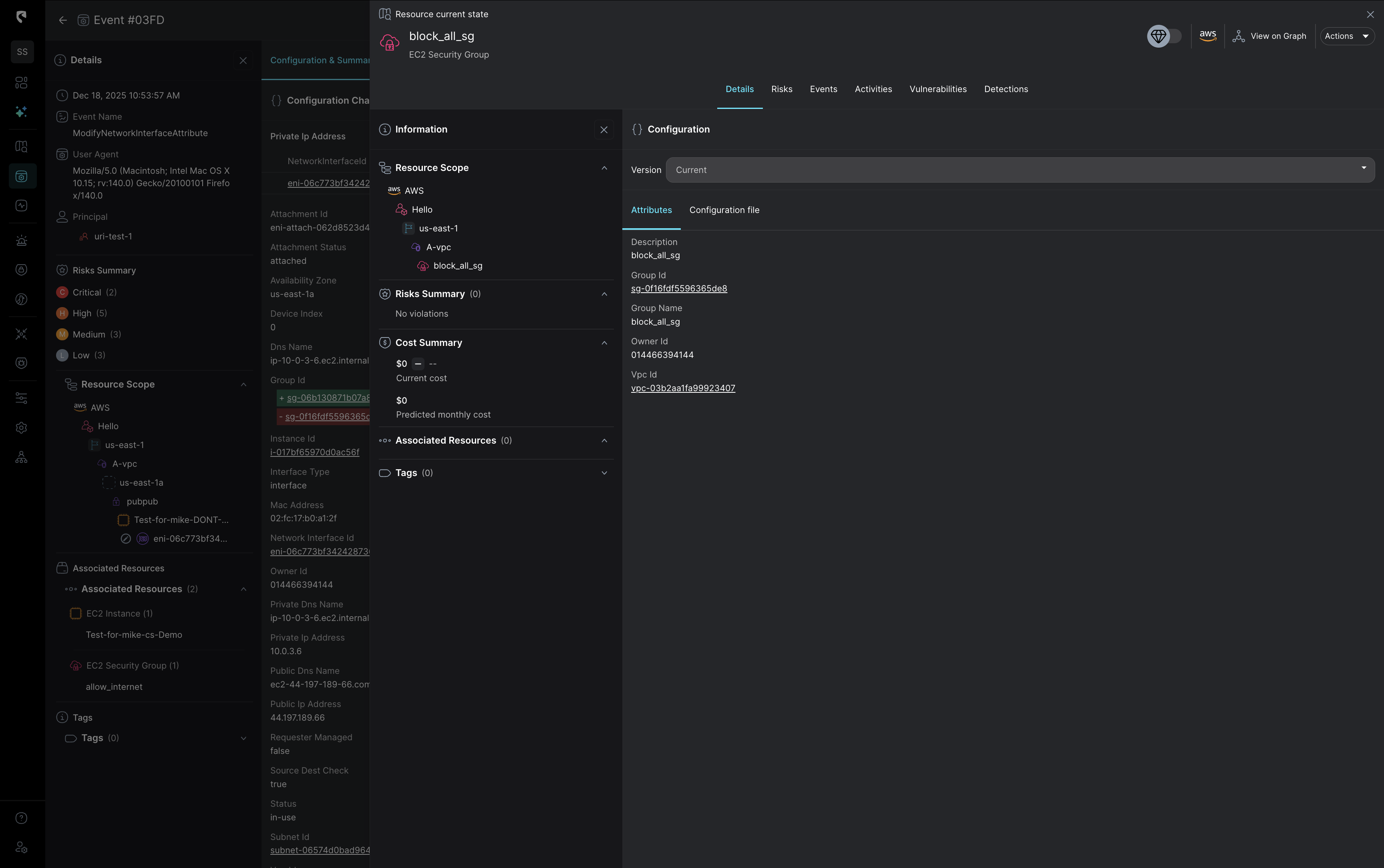
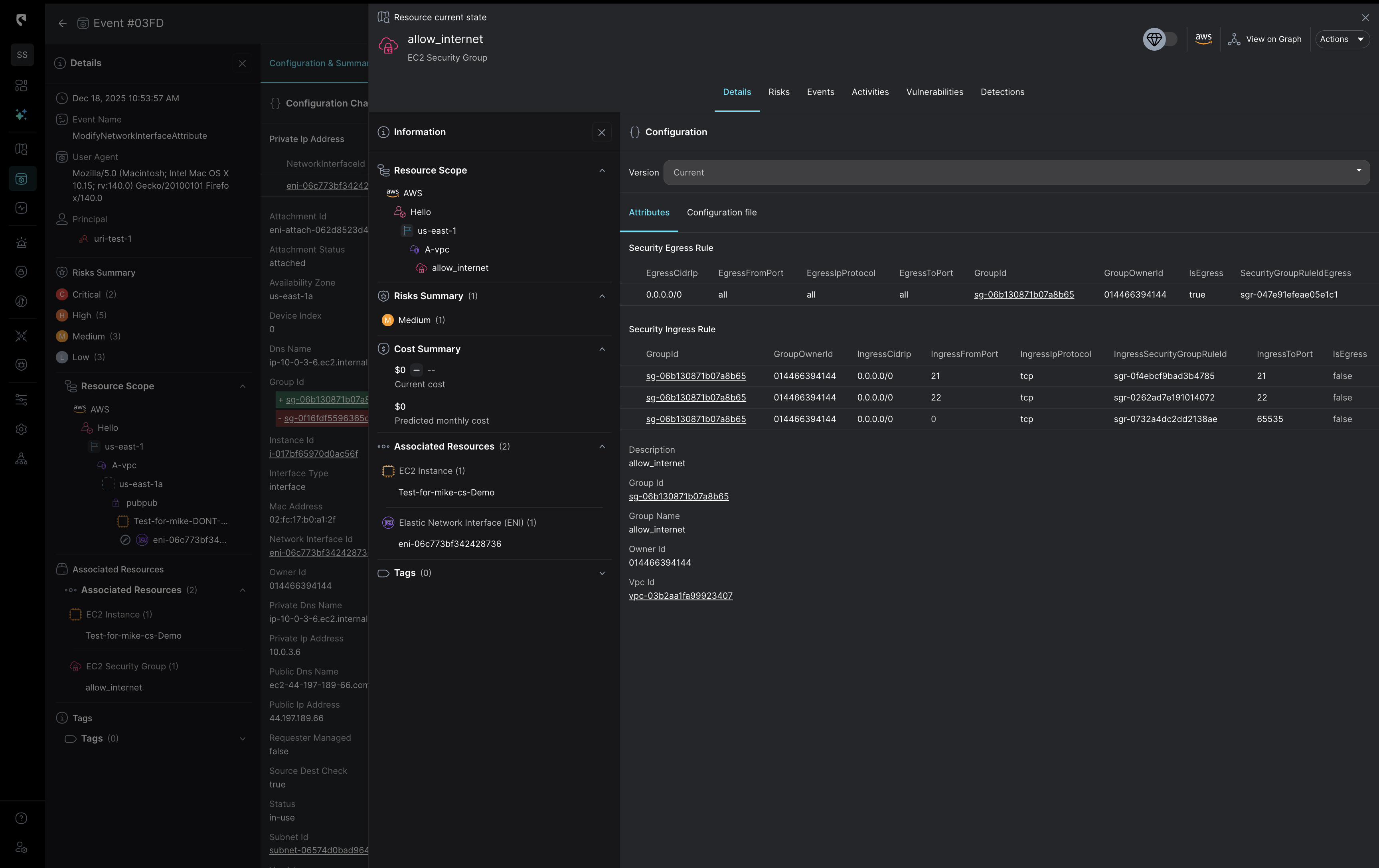

In environments where configuration changes are the attack surface, detection requires real-time state awareness, not post-facto log correlation.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.

.png)

.png)
.png)