.png)

If you don’t know your cloud, you can’t secure it. Alerts and AI don’t help much without real context. “Know Your Cloud” (KYC) is about understanding what you actually have, who and what can access it, and what could go wrong. Get that right, and detection makes sense, AI gets smarter, and response gets better.
In fintech, KYC (Know Your Customer) is how organizations verify identity, establish trust, and manage risk. It’s the foundation of every secure transaction. Without KYC, banks and payment providers are flying blind, exposed to money laundering, fraud, and regulatory risk.
The same principle applies to cloud security operations. Most SOCs only “see” when alerts trigger. But in the cloud, the baseline itself, which includes ephemeral resources, role chaining, serverless functions, and SaaS APIs, is a moving target. If you don’t know your cloud, every detection or AI triage is just guesswork.
“Know Your Cloud” is the process of establishing identity, context, and trust in your cloud footprint as the prerequisite for security operations.
Pass/Fail Mindset:
.png)
Know Your Assets
Know Your Identities
Know Your Configurations
Know Your Risks
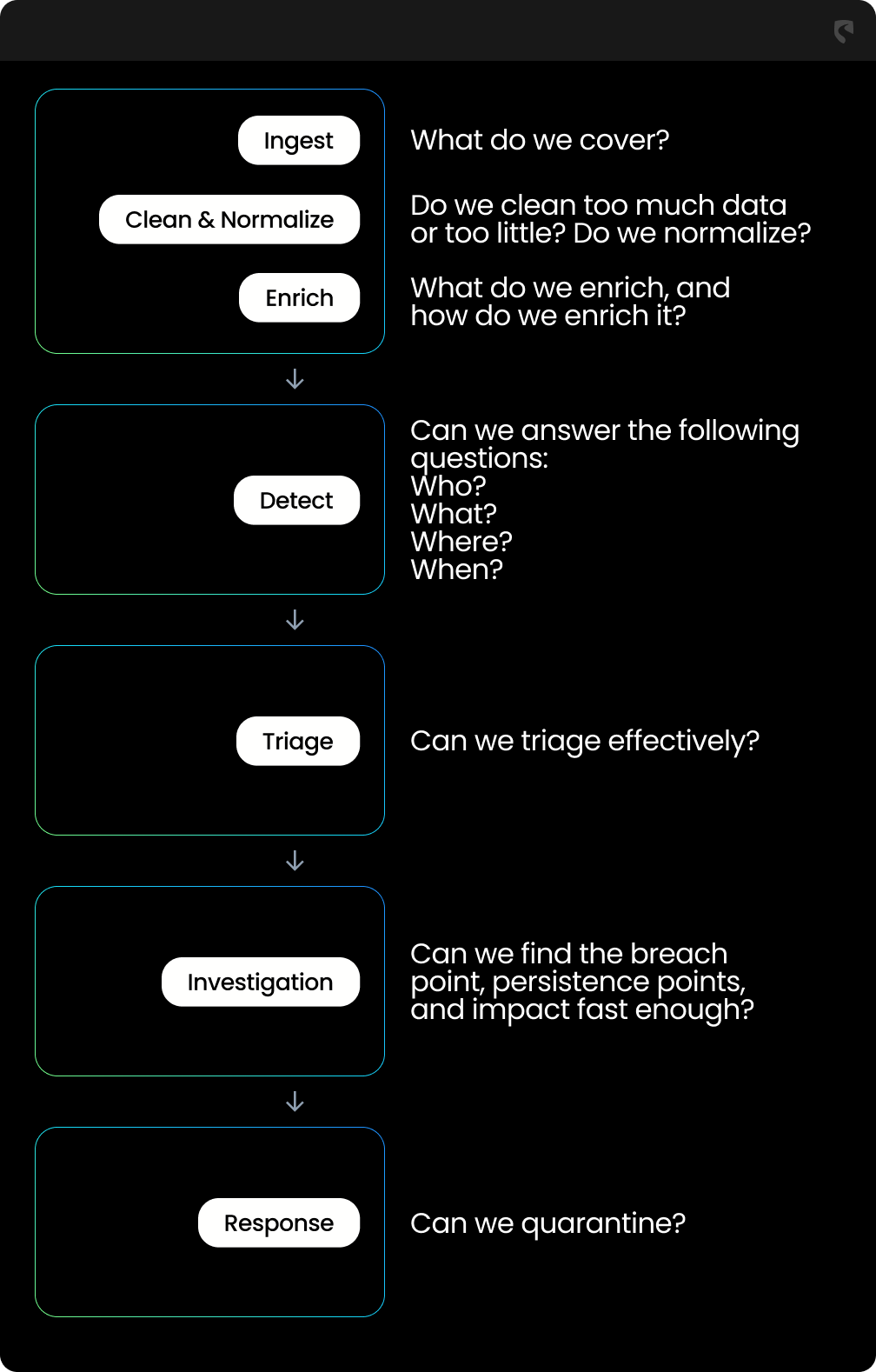
Know Your Telemetry
Know Your Detections
Know Your Responses
Without KYC for cloud SecOps:
Once you Know Your Cloud, you get:
Take the quiz to your team and see where you stand.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.


.png)
