

Stream's CDRGoat is an open-source project that lets SecOps teams safely validate detections and investigations against realistic cloud attack paths.
Each scenario, developed by Stream’s Security Research and Product teams, includes vulnerable infrastructure and walks through a guided live attack to show exactly how adversaries exploit cloud environments in practice.
Cloud adoption has changed how attackers operate. Today’s most successful breaches are carried out by cloud conscious attackers who manipulate the configuration layer to improve their foothold, allowing them to carry out extensive attacks undetected.
That’s why we built CDRGoat: to help SecOps validate how their tools and teams respond to realistic cloud-native attack paths while remaining safe and isolated.
.png)
CDRGoat is a scenario-driven project focused on cloud-native advanced attack simulations, where manipulated configurations and weaknesses are combined with live attack techniques to demonstrate how adversaries exploit them in practice.
CDRGoat includes scenario packages that contain:
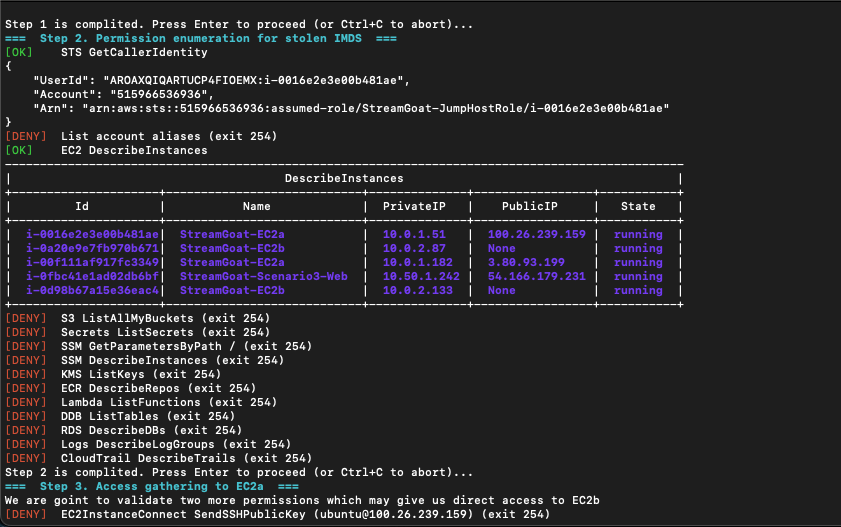
CDRGoat helps SecOps teams spot multi-stage cloud attacks, connect signals across diverse log sources, and see how configuration changes (which may seem benign) can escalate into serious incidents. The result is stronger detections, faster investigations, and greater confidence that when an alert fires, teams know exactly what it means and how to respond.
*While the current scenarios focus on common AWS attack paths, the CDRGoat project will continue to expand to address a broader range of environments and threat models.
This content is provided for educational and informational purposes only. Stream.Security’s CDRGoat is provided as-is without warranties of any kind. By using this project you accept full responsibility for all outcomes. Scenarios are intentionally vulnerable and must only be deployed in isolated, non-production accounts. Stream.Security does not guarantee the accuracy or completeness of the content and assumes no liability for any damages resulting from its use.
Stream.Security does not endorse or condone any illegal activity and disclaims any liability arising from misuse of the material. Stream.Security and project contributors assume no liability for misconfiguration or unintended consequences, including any illegal activity. Ensuring safe and appropriate use is your responsibility.
Stream.Security delivers the only cloud detection and response solution that SecOps teams can trust. Born in the cloud, Stream’s Cloud Twin solution enables real-time cloud threat and exposure modeling to accelerate response in today’s highly dynamic cloud enterprise environments. By using the Stream Security platform, SecOps teams gain unparalleled visibility and can pinpoint exposures and threats by understanding the past, present, and future of their cloud infrastructure. The AI-assisted platform helps to determine attack paths and blast radius across all elements of the cloud infrastructure to eliminate gaps accelerate MTTR by streamlining investigations, reducing knowledge gaps while maximizing team productivity and limiting burnout.

.png)


