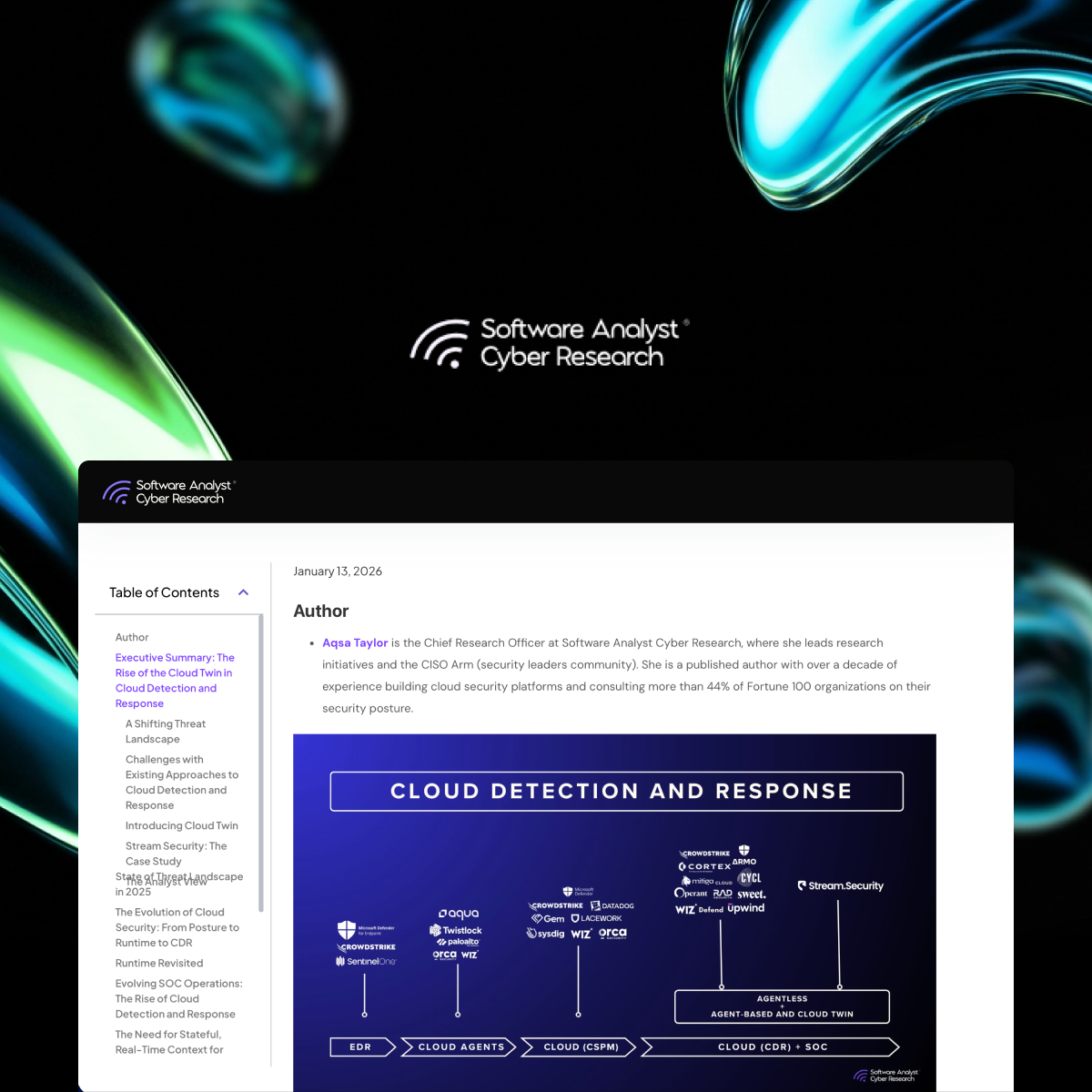
Cloud Detection & Response
Popular
Highlights
Stream Traps
CDR
Canaries: The Force Multiplier for Early Cloud Intrusion Detection
Stream delivers cloud-native detection engines, from rules and anomalies to canaries, as part of our Cloud Detection & Response (CDR) platform.Traditional canaries are siloed, making them hard to scale, hard to manage, and often ignored. Stream takes canaries further by embedding them into the CloudTwin™ fabric.

Stav Sitnikov
Oct 13, 2025
5
min





.png)
.png)
.png)





.png)
.jpg)